diff --git a/.gitignore b/.gitignore
new file mode 100644
index 0000000..d578111
--- /dev/null
+++ b/.gitignore
@@ -0,0 +1,13 @@
+Pods/*
+Libraries/bin/*
+Libraries/include/*
+*.lock
+Libraries/src/*
+.DS_Store
+*.swp
+.Trashes
+*~.nib
+xcuserdata
+Libraries/lib/*
+*.xccheckout
+Build/*
diff --git a/.travis.yml b/.travis.yml
new file mode 100644
index 0000000..70ee415
--- /dev/null
+++ b/.travis.yml
@@ -0,0 +1,8 @@
+language: objective-c
+before_install:
+ - export LANG=en_US.UTF-8
+ - gem install cocoapods --no-ri --no-rdoc
+xcode_workspace: TextSecureiOS.xcworkspace
+xcode_scheme: TextSecureiOS
+xcode_sdk: iphonesimulator
+
diff --git a/Builds/TextSecureiOS-unencryptedpipeline.ipa b/Builds/TextSecureiOS-unencryptedpipeline.ipa
new file mode 100644
index 0000000..28adbf9
Binary files /dev/null and b/Builds/TextSecureiOS-unencryptedpipeline.ipa differ
diff --git a/CONTRIBUTING.md b/CONTRIBUTING.md
new file mode 100644
index 0000000..2d1e360
--- /dev/null
+++ b/CONTRIBUTING.md
@@ -0,0 +1,59 @@
+## Contribute
+
+At this early stage there are two primary developers of TextSecure iOS: [@corbett](https://github.com/corbett) and [@FredericJacobs](https://github.com/fredericjacobs) and as we move from the early stages to more advanced ones opportunities will abound to contribute to the core code base. We are particularly interested in support and contributions associated localization, code review, and automated testing, with any of the [Open Issues](https://github.com/WhisperSystems/TextSecure-iOS/issues?state=open) or [Milestones](https://github.com/WhisperSystems/TextSecure-iOS/issues/milestones?state=open). It may help to open an issue or milestone if you plan to make a contribution so we can be sure to clarify questions, give an overview of architectural plans, and ensure we do not overlap work.
+## Contributor agreement
+
+Apple requires contributors to iOS projects to relicense their code on submit. We'll have to have individual contributors sign something to enable this.
+
+Our volunteer legal have put together a form you can sign electronically. So no scanning, faxing, or carrier pigeons involved. How modern:
+https://whispersystems.org/cla/
+
+Please go ahead and sign, putting your github username in "Address line #2", so that we can accept your pull requests at our heart's delight.
+
+## Code Conventions
+
+We are trying to follow the [GitHub code conventions for Objective-C](https://github.com/github/objective-c-conventions) and we appreciate that pull requests do conform with those conventions.
+
+In addition to that, always add curly braces to your `if` conditionals, even if there is no `else`. Booleans should be declared according to their Objective-C definition, and hence take `YES` or `NO` as values.
+
+One note, for programmers joining us from Java or similar language communities, note that [exceptions are not commonly used for errors that may occur in normal use](http://stackoverflow.com/questions/324284/throwing-an-exception-in-objective-c-cocoa/324805#324805) so familiarize yourself with **NSError**
+
+###UI conventions
+We prefer to use [Storyboards](https://developer.apple.com/library/ios/documentation/general/conceptual/Devpedia-CocoaApp/Storyboard.html) vs. building UI elements within the code itself. We are not at the stage to provide a .strings localizable file for translating, but the goal is to have translatable strings in a single entry point so that we can reach users in their native language wherever possible.
+
+Some tips
+- any PR that does not use segues or story board conventions (red flags: ```[self.navigationController pushViewController:<#(UIViewController *)#> animated:<#(BOOL)#>]``` and/or manual creation of UI elements and/or orphaned ViewControllers in the storyboard) will need to be refactored prior to merge
+- the following are the storyboarder's best friends:
+
+```- (void)prepareForSegue:(UIStoryboardSegue *)segue sender:(id)sender;```
+
+``` [self performSegueWithIdentifier:<#(NSString *)#> sender:<#(id)#>];```
+
+## Tabs vs Spaces
+
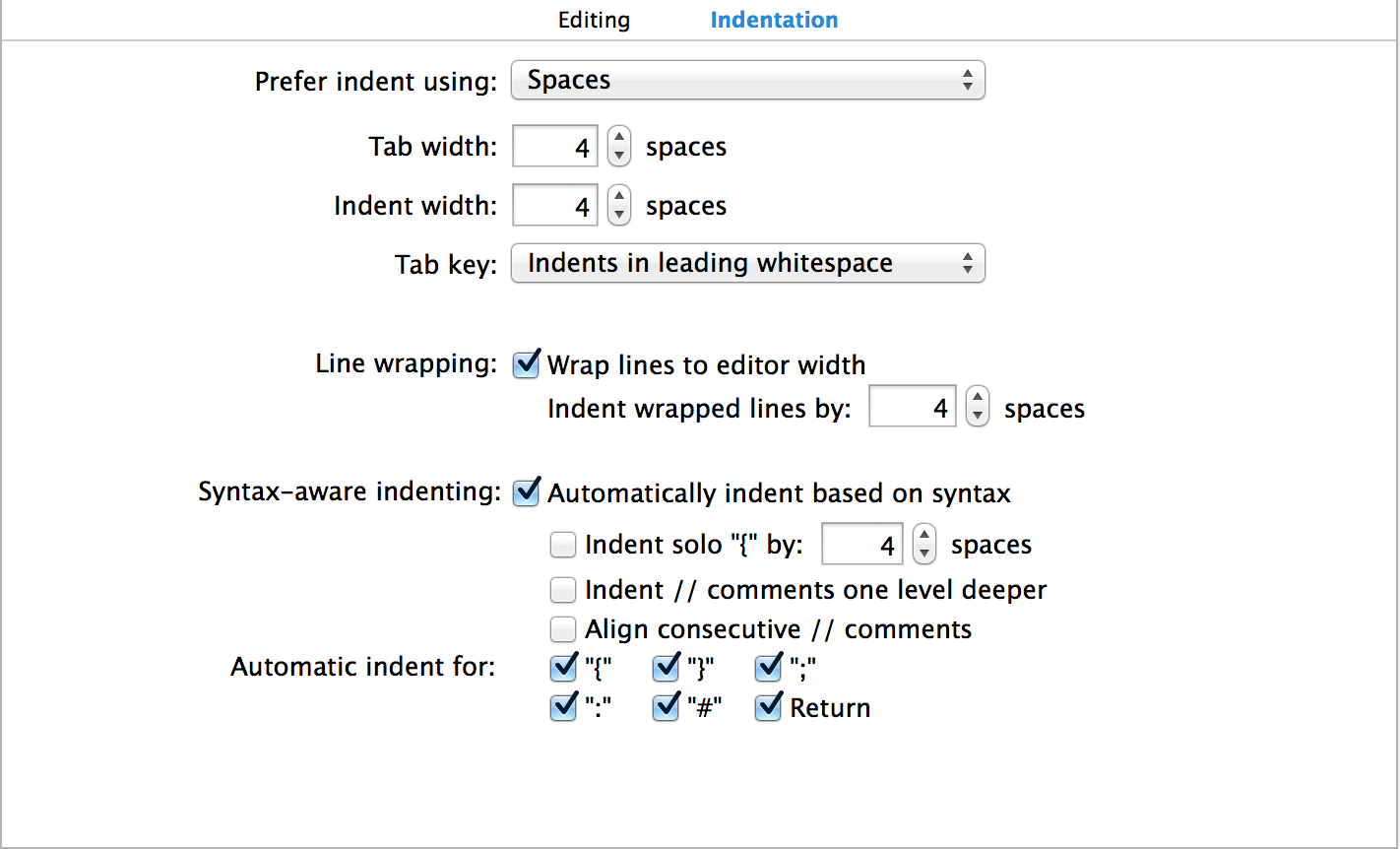
+It's the eternal debate. We chose to adopt spaces. Please set your default Xcode configuration to 4 spaces for tabs, and 4 spaces for indentation (it's Xcode's default setting).
+
+
+
+If you don't agree with us, you can use the [ClangFormat Xcode plugin](https://github.com/travisjeffery/ClangFormat-Xcode) to code with your favorite indentation style!
+
+## PR conventions
+If you are thinking about a major change, to speed up the merge talk with the lead developers first. PRs will not be accepted which break the master branch, so make sure to try, in addition to your unit tests, a simple "regression" test: register, send some messages back and forth, view a thread and conversation and make sure every is just as functional as before your PR only more so.
+
+## BitHub
+
+Open Whisper Systems is currently [experimenting](https://whispersystems.org/blog/bithub/) with the funding privacy Free and Open Source software. Payments are opt-in for the `TextSecure-iOS` repo and can be enabled by adding `MONEYMONEY` in a commit message string. For example, this is the current Open WhisperSystems payout per commit, rendered dynamically as an image by the Open WhisperSystems BitHub instance:
+
+[](https://whispersystems.org/blog/bithub/)
+
+## Contributors
+
+We would like to particularly thank the following contributors:
+
+- Dylan Bourgeois: Substantial UI/UX Improvements
+- Christine Corbett: Lead Developer
+- Alban Diquet: Substantial contributions to the storage infrastructure
+- Frederic Jacobs: Lead Developer
+- Claudiu-Vlad Ursache: UI contributions
+
+TextSecure wouldn’t be possible without the many open-source projects we depend on. Big shoutout to the maintainers of all the [pods](https://github.com/WhisperSystems/TextSecure-iOS/blob/master/Podfile) we use!
diff --git a/TextSecureiOS/Default-568h@2x.png b/Default-568h@2x.png
similarity index 100%
rename from TextSecureiOS/Default-568h@2x.png
rename to Default-568h@2x.png
diff --git a/TextSecureiOS/TextSecureiOSAssets/encyclopedia_1024 icon.psd b/Documentation/Axolotl-slides.pdf
similarity index 52%
rename from TextSecureiOS/TextSecureiOSAssets/encyclopedia_1024 icon.psd
rename to Documentation/Axolotl-slides.pdf
index 86d9921..fe65357 100644
Binary files a/TextSecureiOS/TextSecureiOSAssets/encyclopedia_1024 icon.psd and b/Documentation/Axolotl-slides.pdf differ
diff --git a/Documentation/README.md b/Documentation/README.md
new file mode 100644
index 0000000..559d8a4
--- /dev/null
+++ b/Documentation/README.md
@@ -0,0 +1,5 @@
+Protocol descriptions available
+ * https://github.com/WhisperSystems/TextSecure/wiki/ProtocolV2
+ * https://github.com/WhisperSystems/TextSecure-Server/wiki/API-Protocol
+ * https://www.whispersystems.org/blog/advanced-ratcheting/
+ * https://github.com/trevp/axolotl/wiki
diff --git a/Libraries/README.md b/Libraries/README.md
new file mode 100644
index 0000000..1432eee
--- /dev/null
+++ b/Libraries/README.md
@@ -0,0 +1,8 @@
+# Build scripts
+
+You don't need the build scripts provided in this folder to start contributing thanks to the magic of `Cocoapods`. But for security reasons (App Store builds where verifying integrity of dependencies is important) and debugging reasons, we keep the build scripts of this folder.
+
+## [Curve25519 - Donna implementation](https://github.com/agl/curve25519-donna)
+
+## [OpenSSL Website](http://www.openssl.org)
+OpenSSL is currently not used in this project and if it's a dependency we can avoid, that would be better. Because yeah, OpenSSL code ...
\ No newline at end of file
diff --git a/Libraries/RNCryptor b/Libraries/RNCryptor
deleted file mode 160000
index af3b9d7..0000000
--- a/Libraries/RNCryptor
+++ /dev/null
@@ -1 +0,0 @@
-Subproject commit af3b9d7a1c2c91b5ea2631c6ea388367b266e918
diff --git a/Libraries/build-libcurve25519.sh b/Libraries/build-libcurve25519.sh
new file mode 100755
index 0000000..c0f7dc3
--- /dev/null
+++ b/Libraries/build-libcurve25519.sh
@@ -0,0 +1,48 @@
+#!/bin/sh
+# Automatic build script for curve25519-donna for iPhoneOS and iPhoneSimulator
+# Created by Christine Corbett Moran 11/30/2013
+#
+#
+###########################################################################
+# Change values here #
+# #
+SDKVERSION="7.0" #
+# #
+# Probably shouldn't need to change anything under here
+
+CURRENTPATH=`pwd`
+CFLAGS="-Wmissing-prototypes -Wdeclaration-after-statement -O2 -Wall"
+ARCHS="i386 armv7 armv7s"
+DEVELOPER=`xcode-select -print-path`
+
+mkdir -p "${CURRENTPATH}/src"
+mkdir -p "${CURRENTPATH}/lib"
+
+cd "${CURRENTPATH}/src/"
+git clone https://github.com/agl/curve25519-donna.git
+cd "${CURRENTPATH}/src/curve25519-donna/"
+
+for ARCH in ${ARCHS}
+do
+ make clean
+ if [ "${ARCH}" == "i386" ];
+ then
+ PLATFORM="iPhoneSimulator"
+ else
+ PLATFORM="iPhoneOS"
+ fi
+ export DEVELOPER_PLATFORM="${DEVELOPER}/Platforms/${PLATFORM}.platform/Developer"
+ export SDK="${PLATFORM}${SDKVERSION}.sdk"
+ echo "Building curve25519-donna for ${PLATFORM} ${SDKVERSION} ${ARCH}"
+ export CC="/Applications/Xcode.app/Contents/Developer/usr/bin/gcc -arch ${ARCH} -miphoneos-version-min=7.0 -isysroot ${DEVELOPER_PLATFORM}/SDKs/${SDK} ${CFLAGS}"
+ mkdir -p "${CURRENTPATH}/bin/${PLATFORM}${SDKVERSION}-${ARCH}.sdk"
+ LOG="${CURRENTPATH}/bin/${PLATFORM}${SDKVERSION}-${ARCH}.sdk/curve25519-donna.log"
+ $CC -c curve25519-donna.c -m32 curve25519-donna.c >> "${LOG}" 2>&1
+ ar -rc curve25519-donna.a curve25519-donna.o >> "${LOG}" 2>&1
+ ranlib curve25519-donna.a >> "${LOG}" 2>&1
+ mv curve25519-donna.a ${CURRENTPATH}/bin/${PLATFORM}${SDKVERSION}-${ARCH}.sdk/curve25519-donna.a
+done
+
+echo "Build library for ${ARCHS}..."
+lipo -create ${CURRENTPATH}/bin/iPhoneSimulator${SDKVERSION}-i386.sdk/curve25519-donna.a ${CURRENTPATH}/bin/iPhoneOS${SDKVERSION}-armv7.sdk/curve25519-donna.a ${CURRENTPATH}/bin/iPhoneOS${SDKVERSION}-armv7s.sdk/curve25519-donna.a -output ${CURRENTPATH}/lib/curve25519-donna.a
+
diff --git a/Libraries/build-libssl.sh b/Libraries/build-libssl.sh
old mode 100644
new mode 100755
index 264291f..90faf12
--- a/Libraries/build-libssl.sh
+++ b/Libraries/build-libssl.sh
@@ -22,7 +22,7 @@
# Change values here #
# #
VERSION="1.0.1e" #
-SDKVERSION="6.1" #
+SDKVERSION="7.0" #
# #
###########################################################################
# #
@@ -57,6 +57,9 @@ DEVELOPER=`xcode-select -print-path`
# mkdir -p "${CURRENTPATH}/lib"
#
# tar zxf openssl-${VERSION}.tar.gz -C "${CURRENTPATH}/src"
+
+mkdir -p "${CURRENTPATH}/lib"
+
cd "${CURRENTPATH}/src/openssl-${VERSION}"
@@ -76,11 +79,11 @@ do
echo "Building openssl-${VERSION} for ${PLATFORM} ${SDKVERSION} ${ARCH}"
echo "Please stand by..."
- export CC="${CROSS_TOP}/usr/bin/gcc -arch ${ARCH}"
+ export CC="/Applications/Xcode.app/Contents/Developer/usr/bin/gcc -arch ${ARCH} -miphoneos-version-min=7.0"
mkdir -p "${CURRENTPATH}/bin/${PLATFORM}${SDKVERSION}-${ARCH}.sdk"
LOG="${CURRENTPATH}/bin/${PLATFORM}${SDKVERSION}-${ARCH}.sdk/build-openssl-${VERSION}.log"
- ./Configure iphoneos-cross --openssldir="${CURRENTPATH}/bin/${PLATFORM}${SDKVERSION}-${ARCH}.sdk" > "${LOG}" 2>&1
+ ./Configure iphoneos-cross --openssldir="z > "${LOG}" 2>&1
# add -isysroot to CC=
sed -ie "s!^CFLAG=!CFLAG=-isysroot ${CROSS_TOP}/SDKs/${CROSS_SDK} !" "Makefile"
diff --git a/Podfile b/Podfile
new file mode 100755
index 0000000..e501287
--- /dev/null
+++ b/Podfile
@@ -0,0 +1,37 @@
+platform :ios, '7.0'
+
+link_with ['TextSecureiOS', 'TextSecureiOS Tests']
+
+pod 'RNCryptor', '~> 2.1'
+pod 'FMDB', '~> 2.3'
+pod 'HockeySDK', '~> 3.5.5'
+pod 'libPhoneNumber-iOS', '~> 0.7.3'
+pod 'AFNetworking', '~> 2.3.1'
+pod 'SQLCipher', '~> 3.1.0'
+pod 'GoogleProtobuf', '~> 2.5.0'
+pod 'SWTableViewCell', '~> 0.3.0'
+pod 'curve25519-donna', '~> 1.2.1'
+pod 'UIImage-Categories', '~> 0.0.1'
+pod 'JSMessagesViewController', '~> 3.4.4'
+pod 'LBGIFImage', '~> 0.0.1'
+pod 'Emoticonizer', '~> 1.0.0'
+pod 'InAppSettingsKit', '~> 2.1'
+pod 'HKDFKit', '~> 0.0.1'
+pod 'RMStepsController', '~> 1.0.1'
+pod 'Navajo', '~> 0.0.1'
+pod 'SocketRocket', :podspec => "Podspecs/SocketRocket.podspec"
+
+link_with ['TextSecureiOS', 'TextSecureiOS Tests']
+post_install do |lib_rep|
+ lib_rep.project.targets.each do |target|
+ if target.name == 'Pods-FMDB'
+ target.build_configurations.each do |config|
+ if config.build_settings['OTHER_CFLAGS'].nil?
+ config.build_settings['OTHER_CFLAGS'] = Array.new
+ end
+ puts "Added -DSQLITE_HAS_CODEC CFlag to #{target.name} - #{config.name}"
+ config.build_settings['OTHER_CFLAGS'].unshift('-DSQLITE_HAS_CODEC')
+ end
+ end
+ end
+end
diff --git a/Podspecs/SocketRocket.podspec b/Podspecs/SocketRocket.podspec
new file mode 100644
index 0000000..a0641cf
--- /dev/null
+++ b/Podspecs/SocketRocket.podspec
@@ -0,0 +1,14 @@
+Pod::Spec.new do |s|
+ s.name = 'SocketRocket'
+ s.version = '0.3.2'
+ s.summary = 'A conforming WebSocket (RFC 6455) client library.'
+ s.homepage = 'https://github.com/square/SocketRocket'
+ s.authors = 'Square'
+ s.license = 'Apache License, Version 2.0'
+ s.source = { :git => 'https://github.com/FredericJacobs/SocketRocket.git', :tag => 'v0.3.2' }
+ s.source_files = 'SocketRocket/*.{h,m,c}'
+ s.requires_arc = true
+ s.ios.frameworks = %w{CFNetwork Security}
+ s.osx.frameworks = %w{CoreServices Security}
+ s.libraries = 'icucore'
+end
diff --git a/README.md b/README.md
index b6aa73b..5f775fa 100644
--- a/README.md
+++ b/README.md
@@ -1 +1,91 @@
-TextSecure for iOS, currently in prototype stage.
\ No newline at end of file
+# TextSecure for iOS
+
+Currently in early development stage. Please see [Contributing](https://github.com/WhisperSystems/TextSecure-iOS/blob/master/CONTRIBUTING.md) for details how best to contribute.
+
+### This is a working directory. TextSecure will be the instant messaging part of [Signal](https://github.com/WhisperSystems/Signal-iOS)
+
+## Temporary notice
+
+The main Cocoapods repo got corrupted. Please [follow these instructions](http://blog.cocoapods.org/Repairing-Our-Broken-Specs-Repository/) for your next `pod update`
+
+## Building
+
+1) Clone the repo to a working directory
+
+2) [CocoaPods](http://cocoapods.org) is used to manage dependencies. Pods are setup easily and are distributed via a ruby gem. Follow the simple instructions on the website to setup. After setup, run the following command from the toplevel directory of TextSecureiOS to download the dependencies for TextSecure iOS:
+
+```
+pod install
+```
+If you are having build issues, first make sure your pods are up to date
+```
+pod update
+pod install
+```
+occasionally, CocoaPods itself will need to be updated. Do this with
+```
+sudo gem update
+```
+
+3) Open the `TextSecureiOS.xcworkspace` in Xcode. **Note that for CocoaPods to work properly it is very important to always open the workspace and not the `.xcodeproj` file.** Build and Run and you are ready to go!
+
+4) Debugging network calls. If you are contributing networked code, PonyDebugger is integrated in Debug mode of the application. Check out https://github.com/square/PonyDebugger#quick-start and easily debug network code from the iOS simulator
+
+### Compile Error when building for 64-bit architecture
+
+Due to an issue in version 2.5.0 of the Google Protobuf Library the compiling fails when building the app for a 64-bit architecture (which is the case for the iPhone 5S)
+
+See the Google-Issue for this: https://code.google.com/p/protobuf/issues/detail?id=575.
+
+__However the specified Workaround in the Google Issue solves the compile errors__
+
+## Certificate Pinning
+
+TextSecure uses certificate-pinning to avoid (wo)man-in-the-middle attacks. If you use your own server, here are the steps to generate the certificate file.
+
+1) Use OpenSSL to download the certificate (copy-paste the text between the `BEGIN` and `END` into a `cert.pem` file).
+
+```bash
+openssl s_client -showcerts -connect textsecure-service.whispersystems.org:443 1.8 installed on your build machine, as well as the
+"Android Support Repository" and "Google Repository" installed from the
+Android SDK manager on your build machine.
+
+## Cryptography Notice
+
+This distribution includes cryptographic software. The country in which you currently reside may have restrictions on the import, possession, use, and/or re-export to another country, of encryption software.
+BEFORE using any encryption software, please check your country's laws, regulations and policies concerning the import, possession, or use, and re-export of encryption software, to see if this is permitted.
+See for more information.
+
+The U.S. Government Department of Commerce, Bureau of Industry and Security (BIS), has classified this software as Export Commodity Control Number (ECCN) 5D002.C.1, which includes information security software using or performing cryptographic functions with asymmetric algorithms.
+The form and manner of this distribution makes it eligible for export under the License Exception ENC Technology Software Unrestricted (TSU) exception (see the BIS Export Administration Regulations, Section 740.13) for both object code and source code.
+
+## License
+
+Copyright 2013 Whisper Systems
+
+Licensed under the GPLv3: http://www.gnu.org/licenses/gpl-3.0.html
diff --git a/Settings.bundle/Root.plist b/Settings.bundle/Root.plist
new file mode 100644
index 0000000..fb72e4f
--- /dev/null
+++ b/Settings.bundle/Root.plist
@@ -0,0 +1,94 @@
+
+
+
+
+ PreferenceSpecifiers
+
+
+ Type
+ PSGroupSpecifier
+ Title
+ Security
+
+
+ Type
+ PSToggleSwitchSpecifier
+ Title
+ Screenshot Protection
+ Key
+ screenshotProtection
+ DefaultValue
+
+
+
+ Type
+ PSGroupSpecifier
+ Title
+ Account
+
+
+ DefaultValue
+ TextSecure://?deregisterUserRequest
+ File
+ TextSecure://?deregisterUserRequest
+ Title
+ Deregister
+ Type
+ IASKOpenURLSpecifier
+
+
+ Type
+ PSGroupSpecifier
+ Title
+ Database
+
+
+ DefaultValue
+ TextSecure://?changePasswordRequest
+ File
+ TextSecure://?changePasswordRequest
+ Title
+ Reset Password
+ Type
+ IASKOpenURLSpecifier
+
+
+ KeyboardType
+ NumberPad
+ DefaultValue
+ 5
+ Type
+ PSTextFieldSpecifier
+ Title
+ Lock database after (hrs)
+ Key
+ lockDBAfter
+
+
+ Title
+ Developer
+ Type
+ PSGroupSpecifier
+
+
+ DefaultValue
+
+ Key
+ resetDB
+ Title
+ Reset Application
+ Type
+ PSToggleSwitchSpecifier
+
+
+ Title
+
+ Type
+ PSGroupSpecifier
+ Title
+
+
+ StringsTable
+ Root
+
+
diff --git a/Settings.bundle/en.lproj/Root.strings b/Settings.bundle/en.lproj/Root.strings
new file mode 100644
index 0000000..8cd87b9
Binary files /dev/null and b/Settings.bundle/en.lproj/Root.strings differ
diff --git a/TextSecureiOS Tests/CryptographyTests.mm b/TextSecureiOS Tests/CryptographyTests.mm
new file mode 100644
index 0000000..f79d91e
--- /dev/null
+++ b/TextSecureiOS Tests/CryptographyTests.mm
@@ -0,0 +1,93 @@
+//
+// CryptographyTests.m
+// TextSecureiOS
+//
+// Created by Christine Corbett Moran on 12/19/13.
+// Copyright (c) 2013 Open Whisper Systems. All rights reserved.
+//
+
+#import
+#include
+#import "Cryptography.h"
+#import "NSData+Base64.h"
+#import "NSString+Conversion.h"
+#import "TSMessageSignal.hh"
+#import "IncomingPushMessageSignal.pb.hh"
+#import "TSEncryptedWhisperMessage.hh"
+#import "TSPreKeyWhisperMessage.hh"
+#import "TSPushMessageContent.hh"
+@interface CryptographyTests : XCTestCase
+
+@end
+
+// To avoid + h files
+@interface TSMessageSignal (Test)
++ (textsecure::IncomingPushMessageSignal *)deserialize:(NSData *)data;
++ (TSWhisperMessage*) getWhisperMessageForData:(NSData*) data ofType:(TSWhisperMessageType)contentType;
+@end
+
+@interface Cryptography (Test)
++(NSData*) truncatedSHA256HMAC:(NSData*)dataToHMAC withHMACKey:(NSData*)HMACKey truncation:(int)bytes;
++(NSData*)encryptCBCMode:(NSData*) dataToEncrypt withKey:(NSData*) key withIV:(NSData*) iv withVersion:(NSData*)version withHMACKey:(NSData*) hmacKey withHMACType:(TSMACType)hmacType computedHMAC:(NSData**)hmac;
++(NSData*) decryptCBCMode:(NSData*) dataToDecrypt withKey:(NSData*) key withIV:(NSData*) iv withVersion:(NSData*)version withHMACKey:(NSData*) hmacKey withHMACType:(TSMACType)hmacType forHMAC:(NSData *)hmac;
+@end
+
+@implementation CryptographyTests
+
+
+-(void) testLocalDecryption {
+ NSString* originalMessage = @"Hawaii is awesome";
+ NSString* signalingKeyString = @"VJuRzZcwuY/6VjGw+QSPy5ROzHo8xE36mKwHNvkfyZ+mSPaDlSDcenUqavIX1Vwn\nRRIdrg==";
+ NSData* signalingKey = [NSData dataFromBase64String:signalingKeyString];
+ XCTAssertTrue([signalingKey length]==52, @"signaling key is not 52 bytes but %llu", (unsigned long long)[signalingKey length]);
+ NSData* signalingKeyAESKeyMaterial = [signalingKey subdataWithRange:NSMakeRange(0, 32)];
+ NSData* signalingKeyHMACKeyMaterial = [signalingKey subdataWithRange:NSMakeRange(32, 20)];
+ NSData* iv = [Cryptography generateRandomBytes:16];
+ NSData* version = [Cryptography generateRandomBytes:1];
+ NSData* mac;
+ //Encrypt
+
+ NSData* encryption = [Cryptography encryptCBCMode:[originalMessage dataUsingEncoding:NSUTF8StringEncoding] withKey:signalingKeyAESKeyMaterial withIV:iv withVersion:version withHMACKey:signalingKeyHMACKeyMaterial withHMACType:TSHMACSHA1Truncated10Bytes computedHMAC:&mac]; //Encrypt
+
+ NSMutableData *dataToHmac = [NSMutableData data ];
+ [dataToHmac appendData:version];
+ [dataToHmac appendData:iv];
+ [dataToHmac appendData:encryption];
+
+
+ NSData* expectedHmac = [Cryptography truncatedSHA1HMAC:dataToHmac withHMACKey:signalingKeyHMACKeyMaterial truncation:10];
+
+ XCTAssertTrue([mac isEqualToData:expectedHmac], @"Hmac of encrypted data %@, not equal to expected hmac %@", [mac base64EncodedString], [expectedHmac base64EncodedString]);
+
+ NSData* decryption=[Cryptography decryptCBCMode:encryption withKey:signalingKeyAESKeyMaterial withIV:iv withVersion:version withHMACKey:signalingKeyHMACKeyMaterial withHMACType:TSHMACSHA1Truncated10Bytes forHMAC:mac];
+
+ NSString* decryptedMessage = [[NSString alloc] initWithData:decryption encoding:NSUTF8StringEncoding];
+ XCTAssertTrue([decryptedMessage isEqualToString:originalMessage], @"Decrypted message: %@ is not equal to original: %@",decryptedMessage,originalMessage);
+
+}
+
+
+-(void) testCTRModeDecryption {
+ NSString* originalMessage = @"Hawaii is awesome";
+
+ for(int i=0; i<20; i++) {
+ NSData* lastEncryption = nil;
+ TSMessageKeys * messageKeysMeta = [[TSMessageKeys alloc] initWithCipherKey:[Cryptography generateRandomBytes:32] macKey:[Cryptography generateRandomBytes:32] counter:0];
+ for(int ctr = 0; ctr < 100; ctr++) {
+ TSMessageKeys *messageKeys = [[TSMessageKeys alloc] initWithCipherKey:messageKeysMeta.cipherKey macKey:messageKeysMeta.macKey counter:ctr];
+
+ NSData* encryption = [Cryptography encryptCTRMode:[originalMessage dataUsingEncoding:NSASCIIStringEncoding] withKeys:messageKeys];
+ XCTAssertFalse([encryption isEqualToData:lastEncryption] , @"encryption is equal to a previous encryption! this shouldn't happen with different counters, ctr=%d",ctr);
+ lastEncryption = encryption;
+ NSData* decryption = [Cryptography decryptCTRMode:encryption withKeys:messageKeys];
+
+ NSString* decryptedMessage = [[NSString alloc] initWithData:decryption encoding:NSASCIIStringEncoding];
+ XCTAssertTrue([decryptedMessage isEqualToString:originalMessage], @"Decrypted message: %@ is not equal to original: %@",decryptedMessage,originalMessage);
+ XCTAssertFalse([[originalMessage dataUsingEncoding:NSASCIIStringEncoding] isEqualToData:encryption], @"ctr encryption did nothing, as it encrypted data equals the original data. this is to catch that doesn't happen-as it could be disabled for testing/debugging");
+ }
+ }
+}
+
+
+@end
+
diff --git a/TextSecureiOS Tests/Model/TSMessageIncomingTest.m b/TextSecureiOS Tests/Model/TSMessageIncomingTest.m
new file mode 100644
index 0000000..b8aaf1d
--- /dev/null
+++ b/TextSecureiOS Tests/Model/TSMessageIncomingTest.m
@@ -0,0 +1,117 @@
+//
+// TSMessageIncomingTest.m
+// TextSecureiOS
+//
+// Created by Daniel Cestari on 3/14/14.
+// Copyright (c) 2014 Open Whisper Systems. All rights reserved.
+//
+
+#import
+
+#import "TSMessageIncoming.h"
+#import "TSKeyManager.h"
+#import "TSMessagesDatabase.h"
+#import "TSStorageMasterKey.h"
+
+@interface TSMessageIncomingTest : XCTestCase
+
+@end
+
+@implementation TSMessageIncomingTest
+
+- (void)setUp
+{
+
+ static NSString *masterPw = @"1234test";
+ static NSString *dbFileName = @"test.db";
+ static NSString *dbPreference = @"WasTestDbCreated";
+
+ [super setUp];
+ // Put setup code here. This method is called before the invocation of each test method in the class.
+
+ [TSKeyManager storeUsernameToken:@"56789"];
+
+ // Remove any existing DB
+ [TSMessagesDatabase databaseErase];
+
+
+ [TSStorageMasterKey eraseStorageMasterKey];
+ [TSStorageMasterKey createStorageMasterKeyWithPassword:masterPw error:nil];
+
+ NSError *error;
+
+ // tests datbase creation
+
+ XCTAssertTrue([TSMessagesDatabase databaseCreateWithError:&error], @"message db creation failed");
+ XCTAssertNil(error, @"message db creation returned an error");
+
+ // tests is empty
+ NSArray* threadsFromDb = [TSMessagesDatabase conversations];
+ XCTAssertTrue([threadsFromDb count]==0, @"there are threads in an empty db");
+}
+
+- (void)tearDown
+{
+ // Put teardown code here. This method is called after the invocation of each test method in the class.
+ [super tearDown];
+}
+
+- (void)testInitMessageWithContent
+{
+ NSString *content = @"Hello";
+ NSString *senderId = @"+1234567890";
+ NSDate *date = [NSDate date];
+ NSArray *attachments = @[];
+ TSGroup *group = nil;
+ TSMessageIncomingState state = TSMessageStateReceived;
+
+ TSMessageIncoming *message = [[TSMessageIncoming alloc] initMessageWithContent:content
+ sender:senderId
+ date:date
+ attachements:attachments
+ group:group
+ state:state];
+
+ XCTAssertNotNil(message);
+ XCTAssertEqual(message.content, content);
+ XCTAssertEqual(message.senderId, senderId);
+ XCTAssertEqual(message.timestamp, date);
+ XCTAssertEqual(message.attachments, attachments);
+ XCTAssertEqual(message.group, group);
+ XCTAssertEqual(message.state, state);
+}
+
+- (void)testSetStateWithCompletion
+{
+ NSString *content = @"Hello";
+ NSString *senderId = @"+1234567890";
+ NSDate *date = [NSDate date];
+ NSArray *attachments = @[];
+ TSGroup *group = nil;
+ TSMessageIncomingState state = TSMessageStateReceived;
+
+ TSMessageIncoming *message = [[TSMessageIncoming alloc] initMessageWithContent:content
+ sender:senderId
+ date:date
+ attachements:attachments
+ group:group
+ state:state];
+ XCTAssertEqual(message.state, TSMessageStateReceived);
+
+ dispatch_semaphore_t semaphore = dispatch_semaphore_create(0);
+
+ [message setState:TSMessageStateRead withCompletion:^(BOOL success) {
+ if (success) {
+ XCTAssertEqual(message.state, TSMessageStateRead);
+ } else {
+ XCTFail(@"method reported failure");
+ }
+
+ dispatch_semaphore_signal(semaphore);
+ }];
+
+ dispatch_semaphore_wait(semaphore, DISPATCH_TIME_FOREVER);
+}
+
+
+@end
diff --git a/TextSecureiOS Tests/Model/TSMessageOutgoingTest.m b/TextSecureiOS Tests/Model/TSMessageOutgoingTest.m
new file mode 100644
index 0000000..720b76f
--- /dev/null
+++ b/TextSecureiOS Tests/Model/TSMessageOutgoingTest.m
@@ -0,0 +1,57 @@
+//
+// TSMessageOutgoingTest.m
+// TextSecureiOS
+//
+// Created by Daniel Cestari on 3/12/14.
+// Copyright (c) 2014 Open Whisper Systems. All rights reserved.
+//
+
+#import
+
+#import "TSMessageOutgoing.h"
+#import "TSGroup.h"
+
+@interface TSMessageOutgoingTest : XCTestCase
+
+@end
+
+@implementation TSMessageOutgoingTest
+
+- (void)setUp
+{
+ [super setUp];
+ // Put setup code here; it will be run once, before the first test case.
+}
+
+- (void)tearDown
+{
+ // Put teardown code here; it will be run once, after the last test case.
+ [super tearDown];
+}
+
+- (void)testInitMessageWithContent
+{
+ NSString *content = @"Hello";
+ NSString *recipientId = @"+1234567890";
+ NSDate *date = [NSDate date];
+ NSArray *attachments = @[];
+ TSGroup *group = nil;
+ TSMessageOutgoingState state = TSMessageStatePendingSend;
+
+ TSMessageOutgoing *message = [[TSMessageOutgoing alloc] initMessageWithContent:content
+ recipient:recipientId
+ date:date
+ attachements:attachments
+ group:group
+ state:state];
+
+ XCTAssertNotNil(message);
+ XCTAssertEqual(message.content, content);
+ XCTAssertEqual(message.recipientId, recipientId);
+ XCTAssertEqual(message.timestamp, date);
+ XCTAssertEqual(message.attachments, attachments);
+ XCTAssertEqual(message.group, group);
+ XCTAssertEqual(message.state, state);
+}
+
+@end
diff --git a/TextSecureiOS Tests/PasswordUnlockViewControllerTests.m b/TextSecureiOS Tests/PasswordUnlockViewControllerTests.m
new file mode 100644
index 0000000..ec1f9bd
--- /dev/null
+++ b/TextSecureiOS Tests/PasswordUnlockViewControllerTests.m
@@ -0,0 +1,136 @@
+//
+// UnlockViewControllerTests.m
+// TextSecureiOS
+//
+// Created by Daniel Witurna on 28.02.14.
+// Copyright (c) 2014 Open Whisper Systems. All rights reserved.
+//
+
+#import
+#import "PasswordUnlockViewController.h"
+#import "TSStorageMasterKey.h"
+
+@interface PasswordUnlockViewControllerTests : XCTestCase
+@property (strong, nonatomic) PasswordUnlockViewController *controller;
+@end
+
+static NSString *masterPw = @"1234test";
+
+// Get access to private delegate methods and textfield for testing.
+@interface PasswordUnlockViewController ()
+@property(nonatomic, strong) IBOutlet UITextField *passwordTextField;
+@end
+
+@implementation PasswordUnlockViewControllerTests
+
+- (void)setUp
+{
+ [super setUp];
+
+ NSError *err = nil;
+ //Setup storage key master and lock it.
+ [TSStorageMasterKey eraseStorageMasterKey];
+ [TSStorageMasterKey createStorageMasterKeyWithPassword:masterPw error:&err];
+ [TSStorageMasterKey lockStorageMasterKey];
+
+ XCTAssertNil(err, @"Creating storage master key failed.");
+
+ UIStoryboard *storyboard = [UIStoryboard storyboardWithName:@"MainStoryboard" bundle:nil];
+ self.controller = [storyboard instantiateViewControllerWithIdentifier:@"PasswordUnlockViewController"];
+ [self.controller performSelectorOnMainThread:@selector(loadView) withObject:nil waitUntilDone:YES];
+}
+
+- (void)tearDown
+{
+ self.controller = nil;
+ [super tearDown];
+}
+
+- (void)testEnterCorrectPassword
+{
+ UITextField *passwordTextField = self.controller.passwordTextField;
+ NSString *correctPassword = masterPw;
+ passwordTextField.text = correctPassword;
+
+ [self.controller textFieldShouldReturn:passwordTextField]; //Triggers unlock button press
+
+ BOOL didUnlock = ![TSStorageMasterKey isStorageMasterKeyLocked];
+
+ XCTAssertTrue(didUnlock, @"Password unlock with correct password failed");
+}
+
+- (void)testEnterWrongPassword
+{
+ UITextField *passwordTextField = self.controller.passwordTextField;
+ NSString *wrongPassword = @"test1234";
+ passwordTextField.text = wrongPassword;
+
+ [self.controller textFieldShouldReturn:passwordTextField]; //Triggers unlock button press
+
+ BOOL didUnlock = ![TSStorageMasterKey isStorageMasterKeyLocked];
+
+ XCTAssertFalse(didUnlock, @"Password unlock with wrong password succeeded");
+}
+
+- (void)testEnterEmptyPassword
+{
+ UITextField *passwordTextField = self.controller.passwordTextField;
+ NSString *wrongPassword = @"";
+ passwordTextField.text = wrongPassword;
+
+ [self.controller textFieldShouldReturn:passwordTextField]; //Triggers unlock button press
+
+ BOOL didUnlock = ![TSStorageMasterKey isStorageMasterKeyLocked];
+
+ XCTAssertFalse(didUnlock, @"Password unlock with wrong password succeeded");
+}
+
+- (void)testNilPassword
+{
+ UITextField *passwordTextField = self.controller.passwordTextField;
+ NSString *wrongPassword = nil;
+ passwordTextField.text = wrongPassword;
+
+ [self.controller textFieldShouldReturn:passwordTextField]; //Triggers unlock button press
+
+ BOOL didUnlock = ![TSStorageMasterKey isStorageMasterKeyLocked];
+
+ XCTAssertFalse(didUnlock, @"Password unlock with wrong password succeeded");
+}
+
+- (void)testVeryLongPassword
+{
+ UITextField *passwordTextField = self.controller.passwordTextField;
+ // Creating a string with NSUIntegerMax length will lead to out-of-memory situation.
+ // After trying various values, decided for 2^20, which is still pretty long and
+ // works on 32-bit Simulator in a reasonable amount of time.
+ NSUInteger length = pow(2,20);
+ NSString *veryLongString = [@"" stringByPaddingToLength:length withString:@"a" startingAtIndex:0];
+ passwordTextField.text = veryLongString;
+
+ [self.controller textFieldShouldReturn:passwordTextField]; //Triggers unlock button press
+
+ BOOL didUnlock = ![TSStorageMasterKey isStorageMasterKeyLocked];
+
+ XCTAssertFalse(didUnlock, @"Password unlock with wrong password succeeded");
+}
+
+- (void)testUnusualCharactersPassword{
+ UITextField *passwordTextField = self.controller.passwordTextField;
+ // Code for creating string with a lot of different unicode characters found
+ // here http://cocoadev.com/UniCode
+ NSMutableString *testString = [[NSMutableString alloc] initWithCapacity:55296-32];
+ for (int i = 32; i < 55296; i++) {
+ [testString appendFormat:@"%C", (unichar)i];
+ }
+ passwordTextField.text = testString;
+
+ [self.controller textFieldShouldReturn:passwordTextField]; //Triggers unlock button press
+
+ BOOL didUnlock = ![TSStorageMasterKey isStorageMasterKeyLocked];
+
+ XCTAssertFalse(didUnlock, @"Password unlock with wrong password succeeded");
+}
+
+
+@end
\ No newline at end of file
diff --git a/TextSecureiOS Tests/TSAxolotlConsistencyTest.m b/TextSecureiOS Tests/TSAxolotlConsistencyTest.m
new file mode 100644
index 0000000..03beba7
--- /dev/null
+++ b/TextSecureiOS Tests/TSAxolotlConsistencyTest.m
@@ -0,0 +1,99 @@
+//
+// TSAxolotlConsistencyTest.m
+// TextSecureiOS
+//
+// Created by Frederic Jacobs on 26/03/14.
+// Copyright (c) 2014 Open Whisper Systems. All rights reserved.
+//
+
+
+
+/**
+ ......................................................................
+ . o \ o / _ o __| \ / |__ o _ \ o / o .
+ . /|\ | /\ __\o \o | o/ o/__ /\ | /|\ .
+ . / \ / \ | \ /) | ( \ /o\ / ) | (\ / | / \ / \ .
+ . ....................................................... .
+ . \ o / . . \ o / .
+ . | . . | .
+ . / \ . . / \ .
+ . . . .
+ . _ o . . _ o .
+ . /\ . . /\ .
+ . | \ . . | \ .
+ . . . .
+ . . . .
+ . __\o . . __\o .
+ . /) | . . /) | .
+ . . . .
+ . __| . . __| .
+ . \o . . \o .
+ . ( \ . . ( \ .
+ . . . .
+ . \ / . . \ / .
+ . | . !!! WARNING !!! . | .
+ . /o\ . The following tests do not prove that the . /o\ .
+ . . ratchet is properly implemented but just . .
+ . |__ . that the implementation is consistent. . |__ .
+ . o/ . . o/ .
+ ./ ) . ./ ) .
+ . . . .
+ . . . .
+ . o/__ . . o/__ .
+ . | (\ . . | (\ .
+ . . . .
+ . o _ . . o _ .
+ . /\ . . /\ .
+ . / | . . / | .
+ . . . .
+ . \ o / . . \ o / .
+ . | . . | .
+ . / \ . . / \ .
+ . ....................................................... .
+ . o \ o / _ o __| \ / |__ o _ \ o / o .
+ . /|\ | /\ __\o \o | o/ o/__ /\ | /|\ .
+ . / \ / \ | \ /) | ( \ /o\ / ) | (\ / | / \ / \ .
+ dc.....................................................................
+ */
+
+
+
+
+#import
+
+@interface TSAxolotlConsistencyTest : XCTestCase
+
+@end
+
+@implementation TSAxolotlConsistencyTest
+
+- (void)setUp
+{
+ [super setUp];
+ // Put setup code here. This method is called before the invocation of each test method in the class.
+}
+
+- (void)tearDown
+{
+ // Put teardown code here. This method is called after the invocation of each test method in the class.
+ [super tearDown];
+}
+
+- (void)testEncryptionDecryption
+{
+ NSString *senderID = @"+10000000";
+ NSString *receiverID = @"+41000000";
+ /**
+ * Session for encryption
+ */
+
+
+
+ /**
+ * Session for decryption
+ */
+
+ XCTFail(@"No implementation for \"%s\"", __PRETTY_FUNCTION__);
+}
+
+@end
diff --git a/TextSecureiOS Tests/TSECKeyPairTests.m b/TextSecureiOS Tests/TSECKeyPairTests.m
new file mode 100644
index 0000000..87e320f
--- /dev/null
+++ b/TextSecureiOS Tests/TSECKeyPairTests.m
@@ -0,0 +1,66 @@
+//
+// TSECKeyPairTests.m
+// TextSecureiOS
+//
+// Created by Alban Diquet on 12/29/13.
+// Copyright (c) 2013 Open Whisper Systems. All rights reserved.
+//
+
+#import
+#import "TSECKeyPair.h"
+
+
+@interface TSECKeyPairTests : XCTestCase
+
+@end
+
+@implementation TSECKeyPairTests
+
+- (void)setUp
+{
+ [super setUp];
+ // Put setup code here; it will be run once, before the first test case.
+}
+
+- (void)tearDown
+{
+ // Put teardown code here; it will be run once, after the last test case.
+ [super tearDown];
+}
+
+
+- (void)testGenerateKeyPair
+{
+ TSECKeyPair *keyPair = [TSECKeyPair keyPairGenerateWithPreKeyId:1];
+ XCTAssertNotNil(keyPair, @"Key pair generation returned a nil key pair.");
+
+ NSData *publicKey = [keyPair publicKey];
+ XCTAssertNotNil(publicKey, @"Key pair generation returned a nil public key.");
+}
+
+
+- (void)testGenerateSharedSecret
+{
+ TSECKeyPair *keyPair1 = [TSECKeyPair keyPairGenerateWithPreKeyId:1];
+ TSECKeyPair *keyPair2 = [TSECKeyPair keyPairGenerateWithPreKeyId:2];
+
+ NSData *publicKey = [keyPair1 publicKey];
+ NSData *sharedSecret = [keyPair2 generateSharedSecretFromPublicKey:publicKey];
+ XCTAssertNotNil(sharedSecret, @"Shared secret generation returned a nil shared secret.");
+}
+
+
+- (void)testSerialization
+{
+ TSECKeyPair *keyPair1 = [TSECKeyPair keyPairGenerateWithPreKeyId:1];
+ NSData *serializedKeyPair = [NSKeyedArchiver archivedDataWithRootObject:keyPair1];
+ XCTAssertNotNil(serializedKeyPair, @"Key pair serialization returned a nil data object.");
+
+ TSECKeyPair *keyPair2 = [NSKeyedUnarchiver unarchiveObjectWithData:serializedKeyPair];
+ XCTAssertNotNil(keyPair2, @"Key pair de-serialization returned a nil key pair.");
+
+ XCTAssertEqualObjects([keyPair1 publicKey], [keyPair2 publicKey], @"Key pair de-serialization returned a different public key");
+}
+
+
+@end
diff --git a/TextSecureiOS Tests/TSEncryptedDatabaseTests.m b/TextSecureiOS Tests/TSEncryptedDatabaseTests.m
new file mode 100644
index 0000000..14dc02c
--- /dev/null
+++ b/TextSecureiOS Tests/TSEncryptedDatabaseTests.m
@@ -0,0 +1,133 @@
+//
+// TSEncryptedDatabase2Tests.m
+// TextSecureiOS
+//
+// Created by Alban Diquet on 12/29/13.
+// Copyright (c) 2013 Open Whisper Systems. All rights reserved.
+//
+
+#import
+#import "TSStorageError.h"
+#import "TSDatabaseManager.h"
+#import "TSStorageMasterKey.h"
+#import "FilePath.h"
+#import "FMDatabase.h"
+#import "FMDatabaseQueue.h"
+
+@interface TSEncryptedDatabaseTests : XCTestCase
+
+@end
+
+
+static NSString *masterPw = @"1234test";
+static NSString *dbFileName = @"test.db";
+static NSString *dbPreference = @"WasTestDbCreated";
+
+
+@implementation TSEncryptedDatabaseTests
+
+- (void)setUp
+{
+ [super setUp];
+
+ // Create a storage master key
+ [TSStorageMasterKey eraseStorageMasterKey];
+ [TSStorageMasterKey createStorageMasterKeyWithPassword:masterPw error:nil];
+
+ [TSDatabaseManager databaseEraseAtFilePath:[FilePath pathInDocumentsDirectory:dbFileName] updateBoolPreference:dbPreference];
+}
+
+- (void)tearDown
+{
+ // Put teardown code here; it will be run once, after the last test case.
+ [super tearDown];
+}
+
+
+
+- (void)testDatabaseCreate
+{
+ NSError *error = nil;
+ TSDatabaseManager *encDb = [TSDatabaseManager databaseCreateAtFilePath:[FilePath pathInDocumentsDirectory:dbFileName] updateBoolPreference:dbPreference error:&error];
+
+ XCTAssertNotNil(encDb, @"database creation returned nil");
+ XCTAssertNil(error, @"database creation returned an error");
+}
+
+
+- (void)testDatabaseCreateWithPreviousDatabaseRemnants
+{
+ NSError *error = nil;
+ [TSDatabaseManager databaseCreateAtFilePath:[FilePath pathInDocumentsDirectory:dbFileName] updateBoolPreference:@"" error:nil];
+
+ TSDatabaseManager *encDb = [TSDatabaseManager databaseCreateAtFilePath:[FilePath pathInDocumentsDirectory:dbFileName] updateBoolPreference:dbPreference error:&error];
+
+ XCTAssertNil(error, @"database creation returned an error");
+ XCTAssertNotNil(encDb, @"database creation failed");
+}
+
+
+- (void)testDatabaseCreateWithoutMasterStorageKey
+{
+ [TSStorageMasterKey eraseStorageMasterKey];
+ NSError *error = nil;
+ TSDatabaseManager *encDb = [TSDatabaseManager databaseCreateAtFilePath:[FilePath pathInDocumentsDirectory:dbFileName] updateBoolPreference:dbPreference error:&error];
+
+ XCTAssertNotNil(error, @"database creation succeeded with no master key");
+ XCTAssertTrue([[error domain] isEqualToString:TSStorageErrorDomain], @"database creation succeeded with no master key returned an unexpected error");
+ XCTAssertEqual([error code], TSStorageErrorStorageKeyNotCreated, @"database creation succeeded with no master key returned an unexpected error");
+ XCTAssertNil(encDb, @"database creation succeeded with no master key");
+ [TSStorageMasterKey createStorageMasterKeyWithPassword:masterPw error:nil];
+}
+
+
+- (void)testDatabaseCreateAndOverwrite
+{
+ NSError *error = nil;
+ [TSDatabaseManager databaseCreateAtFilePath:[FilePath pathInDocumentsDirectory:dbFileName] updateBoolPreference:dbPreference error:&error];
+
+ TSDatabaseManager *encDb = [TSDatabaseManager databaseCreateAtFilePath:[FilePath pathInDocumentsDirectory:dbFileName] updateBoolPreference:dbPreference error:&error];
+
+ XCTAssertNotNil(error, @"database overwrite did not return an error");
+ XCTAssertTrue([[error domain] isEqualToString:TSStorageErrorDomain], @"database overwrite returned an unexpected error");
+ XCTAssertEqual([error code], TSStorageErrorDatabaseAlreadyCreated, @"database overwrite returned an unexpected error");
+ XCTAssertNil(encDb, @"database overwrite succeeded");
+}
+
+
+- (void)testDatabaseDecrypt
+{
+ [TSDatabaseManager databaseCreateAtFilePath:[FilePath pathInDocumentsDirectory:dbFileName] updateBoolPreference:dbPreference error:nil];
+
+ NSError *error = nil;
+ TSDatabaseManager *encDb = [TSDatabaseManager databaseOpenAndDecryptAtFilePath:[FilePath pathInDocumentsDirectory:dbFileName] error:&error];
+
+ XCTAssertNotNil(encDb, @"database decryption returned nil");
+ XCTAssertNil(error, @"database decryption returned an error");
+}
+
+- (void)testDatabaseDecryptWithCorruptedStorageKey
+{
+ NSError *error = nil;
+ TSDatabaseManager *encDb = [TSDatabaseManager databaseCreateAtFilePath:[FilePath pathInDocumentsDirectory:dbFileName] updateBoolPreference:dbPreference error:nil];
+
+ // Write something to the DB
+ [encDb.dbQueue inDatabase: ^(FMDatabase *db) {
+ [db executeUpdate:@"CREATE TABLE user_identity_key (serialized_keypair BLOB)"];
+ }];
+
+ // Replace the storage key but use the same password
+ [TSStorageMasterKey eraseStorageMasterKey];
+ [TSStorageMasterKey createStorageMasterKeyWithPassword:masterPw error:&error];
+
+ encDb = [TSDatabaseManager databaseOpenAndDecryptAtFilePath:[FilePath pathInDocumentsDirectory:dbFileName] error:&error];
+
+ XCTAssertNotNil(error, @"database decryption with invalid storage key did not return an error");
+ XCTAssertTrue([[error domain] isEqualToString:TSStorageErrorDomain], @"database decryption with invalid storage key returned an unexpected error");
+ XCTAssertEqual([error code], TSStorageErrorStorageKeyCorrupted, @"database decryption with invalid storage key returned an unexpected error");
+ XCTAssertNil(encDb, @"database decryption with invalid storage key succeeded");
+}
+
+
+
+@end
diff --git a/TextSecureiOS Tests/TSMessagesDatabaseTests.m b/TextSecureiOS Tests/TSMessagesDatabaseTests.m
new file mode 100644
index 0000000..39d51a4
--- /dev/null
+++ b/TextSecureiOS Tests/TSMessagesDatabaseTests.m
@@ -0,0 +1,135 @@
+//
+// TSMessagesDatabase.m
+// TSMessagesDatabase Tests
+//
+// Created by Alban Diquet on 11/24/13.
+// Copyright (c) 2013 Open Whisper Systems. All rights reserved.
+//
+
+#import
+#import "TSMessagesDatabase.h"
+#import "TSStorageError.h"
+#import "Cryptography.h"
+#import "NSData+Base64.h"
+#import "TSStorageMasterKey.h"
+#import "TSContact.h"
+#import "TSECKeyPair.h"
+#import "TSMessage.h"
+#import "TSKeyManager.h"
+#import "Constants.h"
+#import "TSSession.h"
+
+static NSString *masterPw = @"1234test";
+
+@interface TSECKeyPair (Test)
+-(NSData*) getPrivateKey;
+@end
+
+
+@implementation TSECKeyPair (Test)
+-(NSData*) getPrivateKey {
+ return [NSData dataWithBytes:self->privateKey length:32];
+}
+@end
+
+@interface TSMessagesDatabaseTests : XCTestCase
+@property (nonatomic) TSContact *contact;
+@property (nonatomic) TSMessage* message;
+
+@end
+
+@implementation TSMessagesDatabaseTests
+
+- (void)setUp
+{
+ [super setUp];
+
+ [TSKeyManager storeUsernameToken:@"56789"];
+
+ self.contact = [[TSContact alloc] initWithRegisteredID:@"12345" relay:nil];
+
+ self.message = [[TSMessage alloc] initWithSenderId:[TSKeyManager getUsernameToken] recipientId:self.contact.registeredID date:[NSDate date] content:@"Hello World" attachements:nil groupId:nil];
+
+ // Remove any existing DB
+ [TSMessagesDatabase databaseErase];
+
+
+ [TSStorageMasterKey eraseStorageMasterKey];
+ [TSStorageMasterKey createStorageMasterKeyWithPassword:masterPw error:nil];
+
+ NSError *error;
+
+ // tests datbase creation
+
+ XCTAssertTrue([TSMessagesDatabase databaseCreateWithError:&error], @"message db creation failed");
+ XCTAssertNil(error, @"message db creation returned an error");
+
+ // tests is empty
+ NSArray* threadsFromDb = [TSMessagesDatabase conversations];
+ NSArray *messages = [TSMessagesDatabase messagesWithContact:self.contact];
+ XCTAssertTrue([threadsFromDb count]==0, @"there are threads in an empty db");
+ XCTAssertTrue([messages count]==0, @"there are threads in an empty db");
+
+ [TSMessagesDatabase storeMessage:self.message];
+}
+
+- (void)tearDown
+{
+ // Put teardown code here. This method is called after the invocation of each test method in the class.
+ [super tearDown];
+ [TSStorageMasterKey eraseStorageMasterKey];
+}
+
+- (void) testStoreMessage {
+ NSArray *messages = [TSMessagesDatabase messagesWithContact:self.contact];
+ XCTAssertTrue([messages count]==1, @"database should just have one message in it, instead has %lu",(unsigned long)[messages count]);
+ XCTAssertTrue([[[messages objectAtIndex:0] content] isEqualToString:self.message.content], @"message bodies not equal");
+}
+
+- (void)testStoreSession{
+ XCTAssertTrue([[TSMessagesDatabase sessionsForContact:self.contact] count] == 0, @"We had sessions before test started!");
+
+ TSSession *session = [[TSSession alloc] initWithContact:self.contact deviceId:1];
+
+ session.rootKey = [Cryptography generateRandomBytes:10];
+ session.senderChainKey = [[TSChainKey alloc]initWithChainKeyWithKey:[Cryptography generateRandomBytes:10] index:1];
+
+ session.senderEphemeral = [TSECKeyPair keyPairGenerateWithPreKeyId:0];
+
+ NSData *chainData = [Cryptography generateRandomBytes:10];
+ NSData *chainKey = [Cryptography generateRandomBytes:10];
+
+ [session addReceiverChain:chainData chainKey:[[TSChainKey alloc] initWithChainKeyWithKey:chainKey index:1]];
+
+ [TSMessagesDatabase storeSession:session];
+
+ TSSession *retreivedSession = [TSMessagesDatabase sessionForRegisteredId:self.contact.registeredID deviceId:1];
+
+ XCTAssertTrue([retreivedSession.rootKey isEqualToData:session.rootKey], @"Rootkeys don't match");
+ XCTAssertTrue([retreivedSession.senderChainKey.key isEqualToData:session.senderChainKey.key], @"SenderKeyChain keys don't match");
+ XCTAssertTrue([retreivedSession.senderEphemeral.publicKey isEqualToData:session.senderEphemeral.publicKey], @"SenderEphemeral keys don't match");
+ XCTAssertTrue([[retreivedSession receiverChainKey:chainData].key isEqualToData:chainKey], @"Receiver chain keys don't match");
+
+ // The basic properties seem to be saved properly, now let's test 5 with 5 receiving chains and a change of some properties.
+
+ NSMutableArray *chainKeys = [NSMutableArray array];
+ NSMutableArray *ephemerals = [NSMutableArray array];
+ for (int i = 5; i > 0; i--) {
+ TSChainKey *chainKey = [[TSChainKey alloc]initWithChainKeyWithKey:[Cryptography generateRandomBytes:30] index:1];
+ NSData *randomData = [Cryptography generateRandomBytes:32];
+ [retreivedSession addReceiverChain:randomData chainKey:chainKey];
+ [chainKeys addObject:chainKey];
+ [ephemerals addObject:randomData];
+ }
+
+ [TSMessagesDatabase storeSession:retreivedSession];
+
+ TSSession *retreivedSession2 = [TSMessagesDatabase sessionForRegisteredId:self.contact.registeredID deviceId:1];
+
+ for (int i = 4; i >= 0; i --) {
+ XCTAssert([[retreivedSession2 receiverChainKey:[ephemerals objectAtIndex:i]].key isEqualToData: ((TSChainKey*)[chainKeys objectAtIndex:i]).key], @"ChainKey not updated!");
+ }
+}
+
+
+@end
diff --git a/TextSecureiOS Tests/TSProtocolBufferWrapperTests.mm b/TextSecureiOS Tests/TSProtocolBufferWrapperTests.mm
new file mode 100644
index 0000000..d029da5
--- /dev/null
+++ b/TextSecureiOS Tests/TSProtocolBufferWrapperTests.mm
@@ -0,0 +1,464 @@
+ //
+// TSProtocolBufferWrapperTests.m
+// TextSecureiOS
+//
+// Created by Christine Corbett Moran on 1/11/14.
+// Copyright (c) 2014 Open Whisper Systems. All rights reserved.
+//
+
+#import
+#import "TSProtocolBufferWrapper.hh"
+#import "Cryptography.h"
+#import "TSWhisperMessage.hh"
+#import "TSMessageSignal.hh"
+#import "IncomingPushMessageSignal.pb.hh"
+#import "TSPushMessageContent.hh"
+#import "TSEncryptedWhisperMessage.hh"
+#import "TSPreKeyWhisperMessage.hh"
+#import "TSGroupContext.h"
+#import "Constants.h"
+@interface TSProtocolBufferWrapper (Test)
+- (textsecure::IncomingPushMessageSignal *)deserialize:(NSData *)data;
+@end
+
+
+
+@interface TSProtocolBufferWrapperTests : XCTestCase
+@property(nonatomic,strong) TSProtocolBufferWrapper* pbWrapper;
+@property(nonatomic,strong) NSString* body;
+@property(nonatomic,strong) NSArray* attachments;
+@property(nonatomic,strong) TSGroupContext* groupContext;
+@property(nonatomic,strong) NSData* ephemeral;
+@property(nonatomic,strong) NSData* myNextEphemeral;
+@property(nonatomic,strong) NSNumber* prevCounter;
+@property(nonatomic,strong) NSNumber* counter;
+@property(nonatomic,strong) NSNumber* theirPrekeyId;
+@property(nonatomic,strong) NSData* version;
+@property(nonatomic,strong) NSData* cipherKey;
+@property(nonatomic,strong) NSData* hmacKey;
+@property(nonatomic,strong) TSMessageKeys *messageKeys;
+@property(nonatomic,strong) NSString* source;
+@property(nonatomic,strong) NSNumber* sourceDevice;
+@property(nonatomic,strong) NSDate* timestamp;
+
+@end
+
+
+@implementation TSProtocolBufferWrapperTests
+
+- (void)setUp {
+ [super setUp];
+
+ // Neded for TSPushmessageContent
+ _body = @"hello Hawaii";
+ _attachments = nil;
+ _groupContext = nil;
+
+ // needed for TSPreKeyWhisperMessage
+ _myNextEphemeral = [Cryptography generateRandomBytes:32];
+ _theirPrekeyId = [NSNumber numberWithInt:1337];
+
+ // needed for TSEncryptedWhisperMessage
+ _ephemeral = [Cryptography generateRandomBytes:32];
+ _prevCounter = [NSNumber numberWithInt:0];
+ _counter = [NSNumber numberWithInt:0];
+ _version = [Cryptography generateRandomBytes:1];
+
+ // needed for encryption of WhisperMessage
+ _cipherKey = [Cryptography generateRandomBytes:32];
+ _hmacKey = [Cryptography generateRandomBytes:32];
+ _messageKeys = [[TSMessageKeys alloc] initWithCipherKey:_cipherKey macKey:_hmacKey counter:[_counter intValue]];
+
+ // neede for the TSMessagesignal
+ _source = @"+11111111";
+ _sourceDevice = [NSNumber numberWithUnsignedLong:7654321];
+ _timestamp = [NSDate date];
+
+
+ // needed for optional attachment testing
+ NSData* attachment1Key = [Cryptography generateRandomBytes:32];
+ NSData* attachment2Key = [Cryptography generateRandomBytes:32];
+
+ TSAttachment *attachment1 = [[TSAttachment alloc] initWithAttachmentId:[NSNumber numberWithInt:42] contentMIMEType:@"image/jpg" decryptionKey:attachment1Key];
+ TSAttachment *attachment2 = [[TSAttachment alloc] initWithAttachmentId:[NSNumber numberWithInt:35] contentMIMEType:@"video/mp4" decryptionKey:attachment2Key];
+ _attachments = [NSArray arrayWithObjects:attachment1,attachment2, nil];
+
+
+ // needed for optional group testing
+ NSString* member1 = @"+12345678";
+ NSString* member2 = @"+987665";
+ NSString* member3 = @"+11111111";
+ NSData* groupId = [Cryptography generateRandomBytes:8];
+ TSAttachment *avatar = attachment1;
+
+ _groupContext = [[TSGroupContext alloc] initWithId:groupId withType:TSUpdateGroupContext withName:@"Winter Break of Code" withMembers:@[member1,member2,member3] withAvatar:avatar];
+
+
+
+ _pbWrapper = [[TSProtocolBufferWrapper alloc] init];
+
+}
+
+- (void)tearDown {
+ [super tearDown];
+}
+
+/*
+ PushMessageSignal.type = {3=PreKeyWhisperMessage,0=Unencrypted,1=WhisperMessage }
+ PushMessageSignal.message = {PreKeyWhisperMessage,PushMessageContent,WhisperMessage}
+
+ PreKeyWhisperMessage.message = WhisperMessage
+ PushMessageContent.body = "hey, here's the real message"
+ WhisperMessage.message = PushMessageContent
+ */
+
+
+-(void) testCompareAndroidSerialization {
+
+ // Neded for TSPushmessageContent
+ NSString* body = @"hello Hawaii";
+
+ // needed for TSEncryptedWhisperMessage
+ const unsigned char zero32Bytes[] = {0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,
+ 0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,
+ 0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,
+ 0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00};
+ const unsigned char zeroByte[] = {0x00};
+
+ NSData* zero32Data = [NSData dataWithBytes:zero32Bytes length:sizeof(zero32Bytes)];
+ NSData* zero1Data = [NSData dataWithBytes:zeroByte length:sizeof(zeroByte)];
+ NSData *ephemeral = zero32Data;
+ NSNumber *prevCounter = [NSNumber numberWithInt:0];
+ NSNumber* counter = [NSNumber numberWithInt:0];
+ NSData* version = zero1Data;
+ NSNumber* theirPrekeyId = [NSNumber numberWithInt:0];
+
+ // needed for encryption of WhisperMessage
+ NSData* cipherKey = zero32Data;
+
+
+ // Stuffing into objective c
+ TSPushMessageContent* pushContent = [[TSPushMessageContent alloc] initWithBody:body withAttachments:nil withGroupContext:nil];
+
+ TSEncryptedWhisperMessage* tsEncryptedMessage = [[TSEncryptedWhisperMessage alloc] initWithEphemeralKey:ephemeral previousCounter:prevCounter counter:counter encryptedPushMessageContent:[pushContent getTextSecureProtocolData] forVersion:version HMACKey:cipherKey];
+ TSPreKeyWhisperMessage* tsPreKeyWhisperMessage = [TSPreKeyWhisperMessage constructFirstMessageWithEncryptedPushMessageContent:[pushContent getTextSecureProtocolData] theirPrekeyId:theirPrekeyId myCurrentEphemeral:ephemeral myNextEphemeral:ephemeral forVersion:version withHMACKey:cipherKey];
+
+
+ NSString* base64SerializediOSTSPushMessageContentCurrent = [[pushContent getTextSecureProtocolData] base64EncodedStringWithOptions:0];
+
+ NSString* base64SerializediOSTSEncryptedWhisperMessageCurrent = [[tsEncryptedMessage getTextSecureProtocolData] base64EncodedStringWithOptions:0];
+ NSString* base64SerializediOSTSPreKeyWhisperMessageCurrent = [[tsPreKeyWhisperMessage getTextSecureProtocolData] base64EncodedStringWithOptions:0];
+
+ XCTAssertTrue([base64SerializediOSTSEncryptedWhisperMessageCurrent isEqualToString:[tsPreKeyWhisperMessage.message base64EncodedStringWithOptions:0]]);
+
+
+ NSLog(@"%@",base64SerializediOSTSPushMessageContentCurrent);
+ NSLog(@"%@",base64SerializediOSTSEncryptedWhisperMessageCurrent);
+ NSLog(@"%@",base64SerializediOSTSPreKeyWhisperMessageCurrent);
+
+
+ // // gives for iOS currently
+ // NSString* base64SerializediOSTSPushMessageContentCurrent = @"CgxoZWxsbyBIYXdhaWk=";
+ // NSString* base64SerializediOSTSEncryptedWhisperMessageCurrent = @"AAohBQAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAEAAYACIOCgxoZWxsbyBIYXdhaWncdNiDCuAuow==";
+ // NSString* base64SerializediOSTSPreKeyWhisperMessageCurrent = @"AAgAEiEFAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAaACJAAAohBQAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAEAAYACIOCgxoZWxsbyBIYXdhaWncdNiDCuAuow==";
+
+
+
+ // Droid gives us for equavalent data/ephemeral etc.
+ NSString* base64SerializedDroidTSPushMessageContentCurrent = @"CgxoZWxsbyBIYXdhaWk=";
+ NSString* base64SerializedDroidTSEncryptedWhisperMessageCurrent = @"CiAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAABAAGAAiDgoMaGVsbG8gSGF3YWlp";
+ NSString* base64SerializedDroidTSPreKeyWhisperMessageCurrent = @"CAASIAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGiAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAACI2CiAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAABAAGAAiDgoMaGVsbG8gSGF3YWlpKAA=";
+
+
+ XCTAssertTrue([base64SerializediOSTSPushMessageContentCurrent isEqualToString:base64SerializedDroidTSPushMessageContentCurrent], @"push messages PBs not equal ios %@ droid %@",base64SerializediOSTSPushMessageContentCurrent,base64SerializedDroidTSPushMessageContentCurrent);
+ XCTAssertTrue([base64SerializediOSTSEncryptedWhisperMessageCurrent isEqualToString:base64SerializedDroidTSEncryptedWhisperMessageCurrent], @"encrypted message PBs not equal ios %@ droid %@",base64SerializediOSTSEncryptedWhisperMessageCurrent,base64SerializedDroidTSEncryptedWhisperMessageCurrent);
+ XCTAssertTrue([base64SerializediOSTSPreKeyWhisperMessageCurrent isEqualToString:base64SerializedDroidTSPreKeyWhisperMessageCurrent], @"prekey messages PBs not equal ios %@ droid %@",base64SerializediOSTSPreKeyWhisperMessageCurrent,base64SerializedDroidTSPreKeyWhisperMessageCurrent);
+}
+
+-(void) testPrekeyWhisperMessageSerialization {
+ /* TODO: debug this test. as iOS->iOS, Droid->iOS, iOS->Droid first sends now work clearly the PreKeyWhisperMessage protocol buffer serialization isn't all bad. but the // this is crashing // line is well, crashing here. Probably an issue with the test itself
+ (inna hurry) but should be massaged to pass */
+ // Stuffing into objective c
+ TSPushMessageContent* pushContent = [[TSPushMessageContent alloc] initWithBody:_body withAttachments:nil withGroupContext:nil];
+ NSData* encryptedContent = [Cryptography encryptCTRMode:[pushContent getTextSecureProtocolData] withKeys:_messageKeys];
+
+ TSEncryptedWhisperMessage* tsEncryptedMessage = [[TSEncryptedWhisperMessage alloc] initWithEphemeralKey:_ephemeral previousCounter:_prevCounter counter:_counter encryptedPushMessageContent:encryptedContent forVersion:_version HMACKey:_cipherKey];
+
+ TSPreKeyWhisperMessage *tsPreKeyWhisperMessage = [TSPreKeyWhisperMessage constructFirstMessageWithEncryptedPushMessageContent:[tsEncryptedMessage getTextSecureProtocolData] theirPrekeyId:_theirPrekeyId myCurrentEphemeral:_ephemeral myNextEphemeral:_myNextEphemeral forVersion:_version withHMACKey:_cipherKey];
+
+
+
+ NSData* serializedPreKeyMessage = [tsPreKeyWhisperMessage getTextSecureProtocolData];
+
+ TSPreKeyWhisperMessage* deserializedPreKeyMessage = [[TSPreKeyWhisperMessage alloc] initWithTextSecureProtocolData:serializedPreKeyMessage]; // this is crashing
+ XCTAssertTrue([deserializedPreKeyMessage.version isEqualToData:tsPreKeyWhisperMessage.version],@"versions not equal: deserialized: %@, original %@",deserializedPreKeyMessage.version ,tsPreKeyWhisperMessage.version);
+ XCTAssertTrue([deserializedPreKeyMessage.preKeyId isEqualToNumber:tsPreKeyWhisperMessage.preKeyId],@"preKeyIds not equal: deserialized: %@, original %@",deserializedPreKeyMessage.preKeyId ,tsPreKeyWhisperMessage.preKeyId);
+ XCTAssertTrue([deserializedPreKeyMessage.baseKey isEqualToData:tsPreKeyWhisperMessage.baseKey],@"base keys not equal: deserialized: %@, original %@", deserializedPreKeyMessage.baseKey,tsPreKeyWhisperMessage.baseKey);
+ XCTAssertTrue([deserializedPreKeyMessage.identityKey isEqualToData:tsPreKeyWhisperMessage.identityKey],@"identity keys not equal: deserialized: %@, original %@", deserializedPreKeyMessage.identityKey,tsPreKeyWhisperMessage.identityKey);
+
+
+ XCTAssertTrue([deserializedPreKeyMessage.message isEqualToData:encryptedContent],@"encrypted push message content %@ not equal to deserialized version %@",encryptedContent,deserializedPreKeyMessage.message);
+ NSData* decryptedPushMessageContentData = [Cryptography decryptCTRMode:deserializedPreKeyMessage.message withKeys:_messageKeys];
+ XCTAssertTrue([decryptedPushMessageContentData isEqualToData:[pushContent getTextSecureProtocolData]],@"decrypted push message content %@ not equal to original decrypted version %@",decryptedPushMessageContentData,[pushContent getTextSecureProtocolData]);
+ TSEncryptedWhisperMessage* deserializedEncryptedMessage = [[TSEncryptedWhisperMessage alloc] initWithData:decryptedPushMessageContentData];
+ XCTAssertTrue([deserializedEncryptedMessage.previousCounter isEqualToNumber:tsEncryptedMessage.previousCounter], @"previous counters unequal");
+ XCTAssertTrue([deserializedEncryptedMessage.counter isEqualToNumber:tsEncryptedMessage.counter], @"counters unequal");
+ XCTAssertTrue([deserializedEncryptedMessage.ephemeralKey isEqualToData:tsEncryptedMessage.ephemeralKey], @"ephemeral keys unequal; deserialization %@, encrypted %@",deserializedEncryptedMessage.ephemeralKey,tsEncryptedMessage.ephemeralKey);
+
+
+ NSData *decryptedSerializedPushMessageContent = [Cryptography decryptCTRMode:deserializedEncryptedMessage.message withKeys:_messageKeys];
+ TSPushMessageContent *deserializedPushMessageContent = [[TSPushMessageContent alloc] initWithData:decryptedSerializedPushMessageContent];
+
+ XCTAssertTrue([deserializedPushMessageContent.body isEqualToString:pushContent.body], @"messages not equal derialized %@, original %@",deserializedPushMessageContent.body,pushContent.body);
+}
+
+-(void) testMessageSignalSerializationNoAttachmentsNoGroup {
+
+
+ // Stuffing into objective c
+ TSPushMessageContent *pushContent = [[TSPushMessageContent alloc] initWithBody:_body withAttachments:nil withGroupContext:nil];
+ NSData* encryptedContent = [Cryptography encryptCTRMode:[pushContent getTextSecureProtocolData] withKeys:_messageKeys];
+
+ TSEncryptedWhisperMessage *tsEncryptedMessage = [[TSEncryptedWhisperMessage alloc] initWithEphemeralKey:_ephemeral previousCounter:_prevCounter counter:_counter encryptedPushMessageContent:encryptedContent forVersion:_version HMACKey:_cipherKey];
+ TSMessageSignal* messageSignal = [[TSMessageSignal alloc] initWithMessage:tsEncryptedMessage withContentType:TSEncryptedWhisperMessageType withSource:_source withSourceDevice:_sourceDevice withTimestamp:_timestamp];
+
+
+ NSData *serializedMessageSignal = [messageSignal getTextSecureProtocolData];
+ TSMessageSignal* deserializedMessageSignal = [[TSMessageSignal alloc] initWithTextSecureProtocolData:serializedMessageSignal];
+
+ XCTAssertTrue(messageSignal.contentType == deserializedMessageSignal.contentType,@"TSMessageSignal contentType unequal after serialization");
+ XCTAssertTrue([messageSignal.sourceDevice isEqualToNumber:deserializedMessageSignal.sourceDevice],@"TSMessageSignal sourceDevice unequal after serialization");
+ XCTAssertTrue([messageSignal.source isEqualToString:deserializedMessageSignal.source],@"TSMessageSignal source unequal after serialization");
+
+ NSDateFormatter *dateFormatter = [[NSDateFormatter alloc] init];
+ [dateFormatter setDateStyle:NSDateFormatterMediumStyle];
+ [dateFormatter setTimeStyle:NSDateFormatterNoStyle];
+ NSString* nowString = [dateFormatter stringFromDate:messageSignal.timestamp];
+ NSString* convertedNowString = [dateFormatter stringFromDate:deserializedMessageSignal.timestamp];
+
+ XCTAssertTrue([nowString isEqualToString:convertedNowString],@"TSMessageSignal dates unequal after serialization");
+
+
+
+ TSEncryptedWhisperMessage *deserializedEncryptedMessage = (TSEncryptedWhisperMessage*)deserializedMessageSignal.message;
+
+ NSData *decryptedSerializedPushMessageContent = [Cryptography decryptCTRMode:deserializedEncryptedMessage.message withKeys:_messageKeys];
+ TSPushMessageContent *deserializedPushMessageContent = [[TSPushMessageContent alloc] initWithData:decryptedSerializedPushMessageContent];
+ XCTAssertTrue([pushContent.body isEqualToString:deserializedPushMessageContent.body],@"TSMessageSignal message unequal after serialization");
+}
+
+
+
+-(void)testPushMessageContentBodySerialization {
+ TSPushMessageContent *pushContent = [[TSPushMessageContent alloc] initWithBody:_body withAttachments:nil withGroupContext:nil];
+
+ NSData *serializedMessageContent = [pushContent getTextSecureProtocolData];
+ TSPushMessageContent *deserializedPushContent = [[TSPushMessageContent alloc] initWithData:serializedMessageContent];
+
+ XCTAssertTrue([pushContent.body isEqualToString:deserializedPushContent.body], @"Push message content serialization/deserialization failed");
+ XCTAssertTrue([deserializedPushContent.attachments count]==0, @"deserialization has attachments when there should be none");
+
+}
+
+
+-(void)testEncryptedWhisperMessageSerializationNoAttachmentsNoGroup {
+
+ // Stuffing into objective c
+ TSPushMessageContent *pushContent = [[TSPushMessageContent alloc] initWithBody:_body withAttachments:nil withGroupContext:nil];
+ NSData* encryptedContent = [Cryptography encryptCTRMode:[pushContent getTextSecureProtocolData] withKeys:_messageKeys];
+
+ TSEncryptedWhisperMessage *tsEncryptedMessage = [[TSEncryptedWhisperMessage alloc] initWithEphemeralKey:_ephemeral previousCounter:_prevCounter counter:_counter encryptedPushMessageContent:encryptedContent forVersion:_version HMACKey:_cipherKey];
+
+
+ NSData* serializedEncryptedMessage = [tsEncryptedMessage getTextSecureProtocolData];
+
+ TSEncryptedWhisperMessage *deserializedEncryptedMessage = [[TSEncryptedWhisperMessage alloc] initWithTextSecureProtocolData:serializedEncryptedMessage];
+
+ NSLog(@"encrypted whispermessage original vs new %@ vs. %@",tsEncryptedMessage,deserializedEncryptedMessage);
+ XCTAssertTrue([deserializedEncryptedMessage.previousCounter isEqualToNumber:tsEncryptedMessage.previousCounter], @"previous counters unequal");
+
+ XCTAssertTrue([deserializedEncryptedMessage.counter isEqualToNumber:tsEncryptedMessage.counter], @"counters unequal");
+ XCTAssertTrue([deserializedEncryptedMessage.ephemeralKey isEqualToData:tsEncryptedMessage.ephemeralKey], @"ephemeral keys unequal; deserialization %@, encrypted %@",deserializedEncryptedMessage.ephemeralKey,tsEncryptedMessage.ephemeralKey);
+
+
+ NSData *decryptedSerializedPushMessageContent = [Cryptography decryptCTRMode:deserializedEncryptedMessage.message withKeys:_messageKeys];
+ TSPushMessageContent *deserializedPushMessageContent = [[TSPushMessageContent alloc] initWithData:decryptedSerializedPushMessageContent];
+
+ XCTAssertTrue([deserializedPushMessageContent.body isEqualToString:pushContent.body], @"messages not equal");
+}
+
+
+
+-(void) testPushMessageContentAttachmentSerializationDynamic {
+
+ TSPushMessageContent *pushContent = [[TSPushMessageContent alloc] initWithBody:_body withAttachments:_attachments withGroupContext:nil];
+
+
+
+ NSData *serializedMessageContent = [pushContent getTextSecureProtocolData];
+ TSPushMessageContent *deserializedPushContent = [[TSPushMessageContent alloc] initWithData:serializedMessageContent];
+
+ XCTAssertTrue([pushContent.body isEqualToString:deserializedPushContent.body], @"Push message content serialization/deserialization failed");
+
+ XCTAssertTrue([deserializedPushContent.attachments count]==2, @"deserialization doesn't have the right number of attachments, actually has %lu",(unsigned long)[deserializedPushContent.attachments count]);
+
+ TSAttachment *attachment1 = [pushContent.attachments objectAtIndex:0];
+ TSAttachment *attachment2 = [pushContent.attachments objectAtIndex:1];
+
+
+ TSAttachment *attachment1Deserialized = [deserializedPushContent.attachments objectAtIndex:0];
+ TSAttachment *attachment2Deserialized = [deserializedPushContent.attachments objectAtIndex:1];
+
+
+
+ XCTAssertTrue([attachment1Deserialized.attachmentId isEqualToNumber:attachment1.attachmentId], @"deserialized ids do not match for attachment 1");
+ XCTAssertTrue([attachment2Deserialized.attachmentId isEqualToNumber:attachment2.attachmentId], @"deserialized ids do not match for attachment 2");
+
+ XCTAssertTrue(attachment1Deserialized.attachmentType == attachment1.attachmentType, @"deserialized ids do not match for attachment 1");
+ XCTAssertTrue(attachment2Deserialized.attachmentType == attachment2.attachmentType, @"deserialized ids do not match for attachment 2");
+
+ XCTAssertTrue([attachment1Deserialized.attachmentDecryptionKey isEqualToData:attachment1.attachmentDecryptionKey], @"deserialized ids do not match for attachment 1 deserialized %@ serialized %@",attachment1Deserialized.attachmentDecryptionKey,attachment1.attachmentDecryptionKey);
+ XCTAssertTrue([attachment2Deserialized.attachmentDecryptionKey isEqualToData:attachment2.attachmentDecryptionKey], @"deserialized ids do not match for attachment 2 deserialized %@ serialized %@",attachment2Deserialized.attachmentDecryptionKey,attachment2.attachmentDecryptionKey);
+
+
+}
+
+
+-(void) testPushMessageContentAttachmentSerializationStatic {
+ unsigned char testkey = 7;
+ NSData* attachment1Key = [NSData dataWithBytes:&testkey length:sizeof(testkey)];
+
+ TSAttachment *attachment1 = [[TSAttachment alloc] initWithAttachmentId:[NSNumber numberWithInt:42] contentMIMEType:@"image/jpg" decryptionKey:attachment1Key];
+ TSMessage *message = [[TSMessage alloc] initWithSenderId:@"1234" recipientId:@"1234567" date:[[NSDate alloc] init] content:@"Surf is up" attachements:@[attachment1] groupId:nil];
+ NSData *serializedMessageContent = [TSPushMessageContent serializedPushMessageContentForMessage:message withGroupContect:nil];
+ TSPushMessageContent *deserializedPushContent = [[TSPushMessageContent alloc] initWithData:serializedMessageContent];
+
+ XCTAssertTrue([message.content isEqualToString:deserializedPushContent.body], @"Push message content serialization/deserialization failed");
+ XCTAssertTrue([deserializedPushContent.attachments count]==1, @"deserialization doesn't have the right number of attachments, actually has %lu",(unsigned long)[deserializedPushContent.attachments count]);
+
+ TSAttachment *attachment1Deserialized = [deserializedPushContent.attachments objectAtIndex:0];
+
+
+ XCTAssertTrue([attachment1Deserialized.attachmentId isEqualToNumber:attachment1.attachmentId], @"deserialized ids do not match for attachment 1");
+
+ XCTAssertTrue(attachment1Deserialized.attachmentType == attachment1.attachmentType, @"deserialized ids do not match for attachment 1");
+
+ // TODO: this is currently failing meaning attachments don't make it through deserialization process
+ XCTAssertTrue([attachment1Deserialized.attachmentDecryptionKey isEqualToData:attachment1.attachmentDecryptionKey], @"deserialized ids do not match for attachment 1 deserialized %@ serialized %@",attachment1Deserialized.attachmentDecryptionKey,attachment1.attachmentDecryptionKey);
+
+
+}
+
+
+-(void) testPushMessageContentGroupSerializationDynamic {
+ TSPushMessageContent *pushContent = [[TSPushMessageContent alloc] initWithBody:_body withAttachments:nil withGroupContext:_groupContext];
+
+ NSData *serializedMessageContent = [pushContent getTextSecureProtocolData];
+ TSPushMessageContent *deserializedPushContent = [[TSPushMessageContent alloc] initWithData:serializedMessageContent];
+
+ XCTAssertTrue([pushContent.body isEqualToString:deserializedPushContent.body], @"Push message content serialization/deserialization failed");
+ XCTAssertTrue(deserializedPushContent.groupContext!=nil, @"deserialization doesn't give us a group, at all");
+
+ TSGroupContext *groupContextDeserialized = deserializedPushContent.groupContext;
+ XCTAssertTrue([groupContextDeserialized.gid isEqualToData:_groupContext.gid],@"deserialized group id doesn't match original");
+ XCTAssertTrue(groupContextDeserialized.type==_groupContext.type,@"deserialized group type doesn't match original");
+ XCTAssertTrue([groupContextDeserialized.members count]==3,@"deserialized group doesn't have same number of members as original");
+
+ for(NSUInteger i=0; i<3; i++) {
+ XCTAssertTrue([[groupContextDeserialized.members objectAtIndex:i] isEqualToString:[pushContent.groupContext.members objectAtIndex:i]],@"deserialized group member %d not the same as original",i);
+ }
+
+ TSAttachment *groupContextAvatarDeserialized = deserializedPushContent.groupContext.avatar;
+ XCTAssertTrue([groupContextAvatarDeserialized.attachmentId isEqualToNumber:pushContent.groupContext.avatar.attachmentId], @"deserialized ids do not match for avatar");
+ XCTAssertTrue(groupContextAvatarDeserialized.attachmentType == pushContent.groupContext.avatar.attachmentType, @"deserialized ids do not match for avatar");
+ XCTAssertTrue([groupContextAvatarDeserialized.attachmentDecryptionKey isEqualToData:pushContent.groupContext.avatar.attachmentDecryptionKey], @"deserialized ids do not match for avatar");
+
+}
+
+
+
+-(void) testPushMessageContentGroupSerializationStatic {
+
+ NSString* member1 = @"12345678";
+ NSString* member2 = @"987665";
+ NSString* member3 = @"11111111";
+ NSData* avatarKey = [Cryptography generateRandomBytes:32];
+ NSData* groupId = [Cryptography generateRandomBytes:8];
+ TSAttachment *avatar = [[TSAttachment alloc] initWithAttachmentId:[NSNumber numberWithInt:42] contentMIMEType:@"image/jpg" decryptionKey:avatarKey];
+
+
+
+ TSGroupContext *groupContext = [[TSGroupContext alloc] initWithId:groupId withType:TSUpdateGroupContext withName:@"Winter Break of Code" withMembers:[NSArray arrayWithObjects:member1,member2,member3, nil] withAvatar:avatar];
+
+
+ TSMessage *message = [[TSMessage alloc] initWithSenderId:@"1234" recipientId:@"1234567" date:[[NSDate alloc] init] content:@"Surf is up" attachements:nil groupId:nil];
+ NSData *serializedMessageContent = [TSPushMessageContent serializedPushMessageContentForMessage:message withGroupContect:groupContext];
+
+
+ TSPushMessageContent *deserializedPushContent = [[TSPushMessageContent alloc] initWithData:serializedMessageContent];
+
+ XCTAssertTrue([message.content isEqualToString:deserializedPushContent.body], @"Push message content serialization/deserialization failed");
+ XCTAssertTrue(deserializedPushContent.groupContext!=nil, @"deserialization doesn't give us a group, at all");
+
+ TSGroupContext *groupContextDeserialized = deserializedPushContent.groupContext;
+ XCTAssertTrue([groupContextDeserialized.gid isEqualToData:groupContext.gid],@"deserialized group id doesn't match original");
+ XCTAssertTrue(groupContextDeserialized.type==groupContext.type,@"deserialized group type doesn't match original");
+ XCTAssertTrue([groupContextDeserialized.members count]==3,@"deserialized group doesn't have same number of members as original");
+
+
+ XCTAssertTrue([[groupContextDeserialized.members objectAtIndex:0] isEqualToString:member1],@"deserialized group member 1 not the same as original");
+ XCTAssertTrue([[groupContextDeserialized.members objectAtIndex:1] isEqualToString:member2],@"deserialized group member 1 not the same as original");
+ XCTAssertTrue([[groupContextDeserialized.members objectAtIndex:2] isEqualToString:member3],@"deserialized group member 1 not the same as original");
+
+
+ TSAttachment *groupContextAvatarDeserialized = deserializedPushContent.groupContext.avatar;
+ XCTAssertTrue([groupContextAvatarDeserialized.attachmentId isEqualToNumber:avatar.attachmentId], @"deserialized ids do not match for avatar");
+ XCTAssertTrue(groupContextAvatarDeserialized.attachmentType == avatar.attachmentType, @"deserialized ids do not match for avatar");
+ XCTAssertTrue([groupContextAvatarDeserialized.attachmentDecryptionKey isEqualToData:avatar.attachmentDecryptionKey], @"deserialized ids do not match for avatar");
+
+}
+
+
+-(void) testObjcDateToCpp {
+ NSDate* now = [NSDate date];
+ uint64_t cppDate = [self.pbWrapper objcDateToCpp:now];
+ NSDate *convertedNow = [self.pbWrapper cppDateToObjc:cppDate];
+ NSDateFormatter *dateFormatter = [[NSDateFormatter alloc] init];
+ [dateFormatter setDateStyle:NSDateFormatterMediumStyle];
+ [dateFormatter setTimeStyle:NSDateFormatterNoStyle];
+ NSString* nowString = [dateFormatter stringFromDate:now];
+ NSString* convertedNowString = [dateFormatter stringFromDate:convertedNow];
+ XCTAssertTrue([nowString isEqualToString:convertedNowString], @"date conversion is off conversion %@ not equal to original %@",convertedNowString,nowString);
+
+}
+
+-(void) testObjcStringToCpp {
+ NSString *string = @"Hawaii is amazing";
+ const std::string cppString = [self.pbWrapper objcStringToCpp:string];
+ NSString *convertedString = [self.pbWrapper cppStringToObjc:cppString];
+ XCTAssertTrue([convertedString isEqualToString:string], @"date conversion is off conversion %@ not equal to original %@",convertedString,string);
+}
+
+-(void) testObjcDataToCppString {
+ NSData* data = [Cryptography generateRandomBytes:64];
+ const std::string cppDataString = [self.pbWrapper objcDataToCppString:data];
+ NSData* convertedData = [self.pbWrapper cppStringToObjcData:cppDataString];
+ XCTAssertTrue([convertedData isEqualToData:data], @"data conversion is off conversion %@ not equal to original %@",convertedData,data);
+}
+
+-(void) testObjcNumberToCppUInt32 {
+ NSNumber *number = [NSNumber numberWithUnsignedInt:arc4random()];
+ uint32_t cppNumber = [self.pbWrapper objcNumberToCppUInt32:number];
+ NSNumber *convertedNumber = [self.pbWrapper cppUInt32ToNSNumber:cppNumber];
+ XCTAssertTrue([number isEqualToNumber:convertedNumber], @"date conversion is off conversion %@ not equal to original %@",convertedNumber,number);
+}
+
+-(void) testObjcNumberToCppUInt64 {
+ NSNumber *number = [NSNumber numberWithUnsignedLong:arc4random()];
+ uint64_t cppNumber = [self.pbWrapper objcNumberToCppUInt64:number];
+ NSNumber *convertedNumber = [self.pbWrapper cppUInt64ToNSNumber:cppNumber];
+ XCTAssertTrue([number isEqualToNumber:convertedNumber], @"date conversion is off conversion %@ not equal to original %@",convertedNumber,number);
+}
+
+
+@end
diff --git a/TextSecureiOS Tests/TSStorageMasterKeyTests.m b/TextSecureiOS Tests/TSStorageMasterKeyTests.m
new file mode 100644
index 0000000..de0d1d0
--- /dev/null
+++ b/TextSecureiOS Tests/TSStorageMasterKeyTests.m
@@ -0,0 +1,176 @@
+//
+// TSStorageMasterKeyTests.m
+// TextSecureiOS
+//
+// Created by Alban Diquet on 12/29/13.
+// Copyright (c) 2013 Open Whisper Systems. All rights reserved.
+//
+
+#import
+#import "TSStorageMasterKey.h"
+#import "TSStorageError.h"
+#import "KeychainWrapper.h"
+#import "Constants.h"
+
+
+@interface TSStorageMasterKeyTests : XCTestCase
+
+@end
+
+static NSString *masterPw = @"1234test";
+
+
+@implementation TSStorageMasterKeyTests
+
+- (void)setUp
+{
+ [super setUp];
+ [TSStorageMasterKey eraseStorageMasterKey];
+}
+
+- (void)tearDown
+{
+ // Put teardown code here; it will be run once, after the last test case.
+ [super tearDown];
+}
+
+
+- (void)testCreate
+{
+ NSError *error = nil;
+ XCTAssertFalse([TSStorageMasterKey wasStorageMasterKeyCreated], @"wrong default preference");
+
+ NSData *masterKey = [TSStorageMasterKey createStorageMasterKeyWithPassword:masterPw error:&error];
+ XCTAssertNotNil(masterKey, @"master storage key creation returned nil");
+ XCTAssertNil(error, @"master storage key creation returned an error");
+ XCTAssertTrue([TSStorageMasterKey wasStorageMasterKeyCreated], @"master storage key creation did not update preferences");
+}
+
+- (void)testCreateAndOverwrite
+{
+ NSError *error = nil;
+ [TSStorageMasterKey createStorageMasterKeyWithPassword:masterPw error:&error];
+ NSData *masterKey = [TSStorageMasterKey createStorageMasterKeyWithPassword:masterPw error:&error];
+
+ XCTAssertNotNil(error, @"master storage key overwrite did not return an error");
+ XCTAssertTrue([[error domain] isEqualToString:TSStorageErrorDomain], @"master storage key overwrite returned an unexcpected error");
+ XCTAssertEqual([error code], TSStorageErrorStorageKeyAlreadyCreated, @"master storage key overwrite returned an unexcpected error");
+ XCTAssertNil(masterKey, @"master storage key overwrite returned an unexcpected error");
+}
+
+- (void)testUnlock
+{
+ [TSStorageMasterKey createStorageMasterKeyWithPassword:masterPw error:nil];
+
+ NSError *error = nil;
+ NSData *masterKey = [TSStorageMasterKey unlockStorageMasterKeyUsingPassword:masterPw error:&error];
+ XCTAssertNotNil(masterKey, @"master storage key unlocking returned nil");
+ XCTAssertNil(error, @"master storage key unlocking returned an error");
+}
+
+- (void)testUnlockWithWrongPassword
+{
+ [TSStorageMasterKey createStorageMasterKeyWithPassword:masterPw error:nil];
+
+ NSError *error = nil;
+ NSData *masterKey = [TSStorageMasterKey unlockStorageMasterKeyUsingPassword:@"wrongpassword" error:&error];
+
+ XCTAssertNotNil(error, @"master storage key was unlocked with an invalid password");
+ XCTAssertTrue([[error domain] isEqualToString:TSStorageErrorDomain], @"master storage key unlocking returned an unexpected error");
+ XCTAssertEqual([error code], TSStorageErrorInvalidPassword, @"master storage key unlocking returned an unexpected error");
+ XCTAssertNil(masterKey, @"master storage key was unlocked with an invalid password");
+}
+
+- (void)testUnlockBeforeCreation
+{
+
+ NSError *error = nil;
+ NSData *masterKey = [TSStorageMasterKey unlockStorageMasterKeyUsingPassword:@"wrongpassword" error:&error];
+
+ XCTAssertNotNil(error, @"master storage key was unlocked before creation");
+ XCTAssertTrue([[error domain] isEqualToString:TSStorageErrorDomain], @"master storage key unlocking returned an unexpected error");
+ XCTAssertEqual([error code], TSStorageErrorStorageKeyNotCreated, @"master storage key unlocking returned an unexpected error");
+ XCTAssertNil(masterKey, @"master storage key was unlocked before creation");
+}
+
+- (void)testGetBeforeCreation
+{
+
+ NSError *error = nil;
+ NSData *masterKey = [TSStorageMasterKey getStorageMasterKeyWithError:&error];
+
+ XCTAssertNotNil(error, @"master storage key was unlocked before creation");
+ XCTAssertTrue([[error domain] isEqualToString:TSStorageErrorDomain], @"master storage key unlocking returned an unexpected error");
+ XCTAssertEqual([error code], TSStorageErrorStorageKeyNotCreated, @"master storage key unlocking returned an unexpected error");
+ XCTAssertNil(masterKey, @"master storage key was unlocked before creation");
+}
+
+- (void)testLock
+{
+ [TSStorageMasterKey createStorageMasterKeyWithPassword:masterPw error:nil];
+ [TSStorageMasterKey lockStorageMasterKey];
+
+
+ NSError *error = nil;
+ NSData *masterKey = [TSStorageMasterKey getStorageMasterKeyWithError:&error];
+
+ XCTAssertNotNil(error, @"master storage key locking failed");
+ XCTAssertTrue([[error domain] isEqualToString:TSStorageErrorDomain], @"master storage key unlocking returned an unexpected error");
+ XCTAssertEqual([error code], TSStorageErrorStorageKeyLocked, @"master storage key unlocking returned an unexpected error");
+
+ XCTAssertTrue([TSStorageMasterKey isStorageMasterKeyLocked],@"master storage key locking failed");
+ XCTAssertNil(masterKey, @"master storage key locking failed");
+}
+
+- (void)testPasswordChange
+{
+ [TSStorageMasterKey createStorageMasterKeyWithPassword:masterPw error:nil];
+
+ NSString *newPassword = @"test4321";
+ NSError *error = nil;
+ [TSStorageMasterKey changeStorageMasterKeyPasswordFrom:masterPw to:newPassword error:&error];
+ NSData *masterKey = [TSStorageMasterKey unlockStorageMasterKeyUsingPassword:masterPw error:&error];
+ XCTAssertNil(masterKey, @"master storage key password change failed");
+ XCTAssertTrue([[error domain] isEqualToString:TSStorageErrorDomain], @"master storage key unlocking returned an unexpected error");
+ XCTAssertEqual([error code], TSStorageErrorInvalidPassword, @"master storage key unlocking returned an unexpected error");
+ XCTAssertNotNil(error, @"master storage key password change failed");
+
+ error = nil;
+ masterKey = [TSStorageMasterKey unlockStorageMasterKeyUsingPassword:newPassword error:&error];
+ XCTAssertNotNil(masterKey, @"master storage key unlocking returned nil");
+ XCTAssertNil(error, @"master storage key unlocking returned an error");
+
+}
+
+- (void)testUnlockWithDeletedKeychain
+{
+ [TSStorageMasterKey createStorageMasterKeyWithPassword:masterPw error:nil];
+ [TSStorageMasterKey lockStorageMasterKey];
+ [KeychainWrapper deleteItemFromKeychainWithIdentifier:encryptedMasterSecretKeyStorageId];
+
+ NSError *error = nil;
+ NSData *masterKey = [TSStorageMasterKey unlockStorageMasterKeyUsingPassword:masterPw error:&error];
+
+ XCTAssertNotNil(error, @"master storage key locking failed");
+ XCTAssertTrue([[error domain] isEqualToString:TSStorageErrorDomain], @"master storage key was unlocked with deleted keychain");
+ XCTAssertEqual([error code], TSStorageErrorStorageKeyCorrupted, @"master storage key was unlocked with deleted keychain");
+ XCTAssertNil(masterKey, @"master storage key was unlocked with deleted keychain");
+}
+
+
+- (void)testErase
+{
+ [TSStorageMasterKey createStorageMasterKeyWithPassword:masterPw error:nil];
+ [TSStorageMasterKey eraseStorageMasterKey];
+
+ NSError *error = nil;
+ NSData *masterKey = [TSStorageMasterKey unlockStorageMasterKeyUsingPassword:masterPw error:&error];
+
+ XCTAssertNil(masterKey, @"master storage key deletion failed");
+ XCTAssertNotNil(error, @"master storage key deletion failed");
+ XCTAssertTrue([[error domain] isEqualToString:TSStorageErrorDomain], @"master storage key deletion failed");
+ XCTAssertEqual([error code], TSStorageErrorStorageKeyNotCreated, @"master storage key deletion failed");
+}
+
+
+@end
diff --git a/TextSecureiOS Tests/TSUserKeysDatabaseTests.m b/TextSecureiOS Tests/TSUserKeysDatabaseTests.m
new file mode 100644
index 0000000..1b7d76f
--- /dev/null
+++ b/TextSecureiOS Tests/TSUserKeysDatabaseTests.m
@@ -0,0 +1,59 @@
+//
+// TSUserKeysDatabaseTests.m
+// TextSecureiOS
+//
+// Created by Alban Diquet on 12/29/13.
+// Copyright (c) 2013 Open Whisper Systems. All rights reserved.
+//
+
+#import
+#import "TSUserKeysDatabase.h"
+#import "TSStorageMasterKey.h"
+#import "Constants.h"
+@interface TSUserKeysDatabaseTests : XCTestCase
+
+@end
+
+
+static NSString *storageKeyPw = @"1234test";
+
+
+@implementation TSUserKeysDatabaseTests
+
+- (void)setUp
+{
+ [super setUp];
+
+ // Remove any existing DB
+ [TSUserKeysDatabase databaseErase];
+
+ // Create a storage master key
+ [TSStorageMasterKey eraseStorageMasterKey];
+ [TSStorageMasterKey createStorageMasterKeyWithPassword:storageKeyPw error:nil];
+}
+
+- (void)tearDown
+{
+ // Put teardown code here; it will be run once, after the last test case.
+ [super tearDown];
+}
+
+
+- (void)testDatabaseCreate
+{
+ NSError *error = nil;
+ XCTAssertTrue([TSUserKeysDatabase databaseCreateUserKeysWithError:&error], @"database creation failed");
+ XCTAssertNil(error, @"database creation returned an error");
+
+
+ XCTAssertNotNil([TSUserKeysDatabase allPreKeys], @"database creation returned nil prekeys");
+ XCTAssertNotNil([TSUserKeysDatabase identityKey], @"database creation returned nil identity key");
+ // Check for key of last resort
+ XCTAssertNotNil([TSUserKeysDatabase preKeyWithId:kLastResortKeyId], @"database creation returned nil for key of last resort");
+}
+
+
+
+
+
+@end
diff --git a/TextSecureiOS Tests/TSWaitingPushMessageDatabaseTests.m b/TextSecureiOS Tests/TSWaitingPushMessageDatabaseTests.m
new file mode 100644
index 0000000..b0bdf28
--- /dev/null
+++ b/TextSecureiOS Tests/TSWaitingPushMessageDatabaseTests.m
@@ -0,0 +1,32 @@
+//
+// TSWaitingPushMessageDatabaseTests.m
+// TextSecureiOS
+//
+// Created by Christine Corbett Moran on 3/7/14.
+// Copyright (c) 2014 Open Whisper Systems. All rights reserved.
+//
+
+#import
+
+#warning needs implemented
+@interface TSWaitingPushMessageDatabaseTests : XCTestCase
+
+@end
+
+@implementation TSWaitingPushMessageDatabaseTests
+
+- (void)setUp
+{
+ [super setUp];
+ // Put setup code here; it will be run once, before the first test case.
+}
+
+- (void)tearDown
+{
+ // Put teardown code here; it will be run once, after the last test case.
+ [super tearDown];
+}
+
+
+
+@end
diff --git a/TextSecureiOSTests/TextSecureiOSTests-Info.plist b/TextSecureiOS Tests/TextSecureiOS Tests-Info.plist
similarity index 88%
rename from TextSecureiOSTests/TextSecureiOSTests-Info.plist
rename to TextSecureiOS Tests/TextSecureiOS Tests-Info.plist
index edee81c..418bf8d 100644
--- a/TextSecureiOSTests/TextSecureiOSTests-Info.plist
+++ b/TextSecureiOS Tests/TextSecureiOS Tests-Info.plist
@@ -7,7 +7,7 @@
CFBundleExecutable
${EXECUTABLE_NAME}
CFBundleIdentifier
- com.openwhispersystems.${PRODUCT_NAME:rfc1034identifier}
+ org.whispersystems.whisper.${PRODUCT_NAME:rfc1034identifier}
CFBundleInfoDictionaryVersion
6.0
CFBundlePackageType
diff --git a/TextSecureiOS Tests/TextSecureiOS Tests-Prefix.pch b/TextSecureiOS Tests/TextSecureiOS Tests-Prefix.pch
new file mode 100644
index 0000000..3fdee9d
--- /dev/null
+++ b/TextSecureiOS Tests/TextSecureiOS Tests-Prefix.pch
@@ -0,0 +1,10 @@
+//
+// Prefix header
+//
+// The contents of this file are implicitly included at the beginning of every source file.
+//
+
+#ifdef __OBJC__
+ #import
+ #import
+#endif
diff --git a/TextSecureiOS Tests/VerificationViewControllerTests.m b/TextSecureiOS Tests/VerificationViewControllerTests.m
new file mode 100644
index 0000000..76c4488
--- /dev/null
+++ b/TextSecureiOS Tests/VerificationViewControllerTests.m
@@ -0,0 +1,123 @@
+//
+// VerificationViewControllerTests.m
+// TextSecureiOS
+//
+// Created by Troy Farrell on 2/25/14.
+// Copyright (c) 2014 Open Whisper Systems. All rights reserved.
+//
+
+#import
+#import "VerificationViewController.h"
+
+@interface VerificationViewControllerTests : XCTestCase
+@property (strong, nonatomic) VerificationViewController *controller;
+@end
+
+// Steal this private method for testing.
+@interface VerificationViewController ()
+-(void)setLocaleCountry;
+@end
+
+@implementation VerificationViewControllerTests
+
+- (void)setUp
+{
+ [super setUp];
+
+ UIStoryboard *storyboard = [UIStoryboard storyboardWithName:@"MainStoryboard" bundle:nil];
+ self.controller = [storyboard instantiateViewControllerWithIdentifier:@"VerificationViewController"];
+ [self.controller performSelectorOnMainThread:@selector(loadView) withObject:nil waitUntilDone:YES];
+}
+
+- (void)tearDown
+{
+ self.controller = nil;
+ [super tearDown];
+}
+
+// This test verifies that entering a basic US phone number works
+-(void)testBasicUSPhoneNumber
+{
+ // Focus and set the countryCodeInput.
+ UITextField *countryCodeInput = self.controller.countryCodeInput;
+ [self.controller textFieldShouldBeginEditing:countryCodeInput];
+ countryCodeInput.text = @"+1";
+
+ // Focus and set the phoneNumber.
+ UITextField *phoneNumber = self.controller.phoneNumber;
+ NSRange range = NSMakeRange(0, 0);
+ NSArray *number = @[@"2", @"1", @"2", @"7", @"3", @"6", @"5", @"0", @"0", @"0"];
+ [self.controller textFieldShouldBeginEditing:phoneNumber];
+ for (NSUInteger i = 0; i < number.count; i++) {
+ if (4 == i || 7 == i) { // account for dashes in these positions
+ range.location++;
+ }
+ [self.controller textField:phoneNumber shouldChangeCharactersInRange:range replacementString:[number objectAtIndex:i]];
+ range.location++;
+ }
+
+ NSString *expectedPhoneNUmber = @"212-736-5000";
+ XCTAssert([phoneNumber.text isEqualToString:expectedPhoneNUmber], @"phoneNumber does not match expected value");
+}
+
+// This test is to ensure that the countryCodeInput is never empty. This is
+// a related, but separate issue to the -(void)testEmptyCountryCodeCrash
+// test.
+- (void)testEmptyCountryCodeInputPrevention
+{
+ // Pretend that the view controller became visible.
+ [self.controller setLocaleCountry];
+
+ // Focus on the countryCodeInput. This causes the existing text to be
+ // cleared.
+ UITextField *countryCodeInput = self.controller.countryCodeInput;
+ [self.controller textFieldShouldBeginEditing:countryCodeInput];
+
+ // Verify that the countryCodeInput text field has only a +.
+ XCTAssert([countryCodeInput.text isEqualToString:@"+"], @"countryCodeInput text is not only a +");
+
+ // Stop editing the text field.
+ [self.controller textFieldDidEndEditing:countryCodeInput];
+
+ // The countryCodeInput text must not be @"" or @"+".
+ XCTAssert(countryCodeInput.text.length > 1, @"countryCodeInput text is too short.");
+ XCTAssert([[countryCodeInput.text substringToIndex:1] isEqualToString:@"+"], @"countryCodeInput text does not start with +");
+
+ NSString *numbersPart = [countryCodeInput.text substringFromIndex:1];
+ NSCharacterSet *numbers = [NSCharacterSet decimalDigitCharacterSet];
+ NSRange range = [numbersPart rangeOfCharacterFromSet:numbers];
+
+ XCTAssert(range.location != NSNotFound, @"countryCodeInput text does not contain a digit");
+}
+
+// This test is to ensure that focusing on the countryCodeInput after
+// selecting a country does not cause the country code to be hidden.
+-(void)testCountrySelectAfterFocusingCountryCodeInput
+{
+ // Pretend that the view controller became visible.
+ [self.controller setLocaleCountry];
+
+ // Focus, set and blur the countryCodeInput.
+ UITextField *countryCodeInput = self.controller.countryCodeInput;
+ [self.controller textFieldShouldBeginEditing:countryCodeInput];
+ countryCodeInput.text = @"+33";
+ [self.controller textFieldDidEndEditing:countryCodeInput];
+ XCTAssert([countryCodeInput.text isEqualToString:@"+33"], @"countryCodeInput text does not match set value");
+
+ // Pretend that user selected a country from the CountryViewController.
+ NSString *plistFile = [[NSBundle mainBundle] pathForResource:countryInfoPathInMainBundle ofType:@"plist"];
+ NSDictionary *countryDict = [[NSMutableDictionary alloc] initWithContentsOfFile:plistFile];
+ NSArray *countryList = [[countryDict allKeys] sortedArrayUsingSelector:@selector(localizedCaseInsensitiveCompare:)];
+ NSString *countryTitleForAndorra = [countryList objectAtIndex:4];
+ NSDictionary *countryInfoForAndorra = [countryDict objectForKey:countryTitleForAndorra];
+ [self.controller countryChosen:[NSNotification notificationWithName:@"CountryChosen" object:nil userInfo:countryInfoForAndorra]];
+
+ // On exiting the CountryViewController, the countryCodeInput is
+ // selected again. This time, it should not replace the country code
+ // that was just selected.
+ [self.controller textFieldShouldBeginEditing:countryCodeInput];
+ NSString *expectedCountryCode = [NSString stringWithFormat:@"+%@",[countryInfoForAndorra objectForKey:countryInfoKeyCountryCode]];
+ XCTAssert([countryCodeInput.text isEqualToString:expectedCountryCode], @"countryCodeInput text does not match selected country info");
+}
+
+@end
diff --git a/TextSecureiOSTests/en.lproj/InfoPlist.strings b/TextSecureiOS Tests/en.lproj/InfoPlist.strings
similarity index 100%
rename from TextSecureiOSTests/en.lproj/InfoPlist.strings
rename to TextSecureiOS Tests/en.lproj/InfoPlist.strings
diff --git a/TextSecureiOS.xcodeproj/project.pbxproj b/TextSecureiOS.xcodeproj/project.pbxproj
index 62d83a0..0743d14 100644
--- a/TextSecureiOS.xcodeproj/project.pbxproj
+++ b/TextSecureiOS.xcodeproj/project.pbxproj
@@ -7,58 +7,56 @@
objects = {
/* Begin PBXBuildFile section */
- A51B776F17050C42002B8E53 /* FMDatabase.m in Sources */ = {isa = PBXBuildFile; fileRef = A51B776517050C42002B8E53 /* FMDatabase.m */; };
- A51B777017050C42002B8E53 /* FMDatabaseAdditions.m in Sources */ = {isa = PBXBuildFile; fileRef = A51B776717050C42002B8E53 /* FMDatabaseAdditions.m */; };
- A51B777117050C42002B8E53 /* FMDatabasePool.m in Sources */ = {isa = PBXBuildFile; fileRef = A51B776917050C42002B8E53 /* FMDatabasePool.m */; };
- A51B777217050C42002B8E53 /* FMDatabaseQueue.m in Sources */ = {isa = PBXBuildFile; fileRef = A51B776B17050C42002B8E53 /* FMDatabaseQueue.m */; };
- A51B777417050C42002B8E53 /* FMResultSet.m in Sources */ = {isa = PBXBuildFile; fileRef = A51B776E17050C42002B8E53 /* FMResultSet.m */; };
- A51B778F17050C71002B8E53 /* NSObject+SBJson.m in Sources */ = {isa = PBXBuildFile; fileRef = A51B777717050C71002B8E53 /* NSObject+SBJson.m */; };
- A51B779017050C71002B8E53 /* SBJsonParser.m in Sources */ = {isa = PBXBuildFile; fileRef = A51B777A17050C71002B8E53 /* SBJsonParser.m */; };
- A51B779117050C71002B8E53 /* SBJsonStreamParser.m in Sources */ = {isa = PBXBuildFile; fileRef = A51B777C17050C71002B8E53 /* SBJsonStreamParser.m */; };
- A51B779217050C71002B8E53 /* SBJsonStreamParserAccumulator.m in Sources */ = {isa = PBXBuildFile; fileRef = A51B777E17050C71002B8E53 /* SBJsonStreamParserAccumulator.m */; };
- A51B779317050C71002B8E53 /* SBJsonStreamParserAdapter.m in Sources */ = {isa = PBXBuildFile; fileRef = A51B778017050C71002B8E53 /* SBJsonStreamParserAdapter.m */; };
- A51B779417050C71002B8E53 /* SBJsonStreamParserState.m in Sources */ = {isa = PBXBuildFile; fileRef = A51B778217050C71002B8E53 /* SBJsonStreamParserState.m */; };
- A51B779517050C71002B8E53 /* SBJsonStreamWriter.m in Sources */ = {isa = PBXBuildFile; fileRef = A51B778417050C71002B8E53 /* SBJsonStreamWriter.m */; };
- A51B779617050C71002B8E53 /* SBJsonStreamWriterAccumulator.m in Sources */ = {isa = PBXBuildFile; fileRef = A51B778617050C71002B8E53 /* SBJsonStreamWriterAccumulator.m */; };
- A51B779717050C71002B8E53 /* SBJsonStreamWriterState.m in Sources */ = {isa = PBXBuildFile; fileRef = A51B778817050C71002B8E53 /* SBJsonStreamWriterState.m */; };
- A51B779817050C71002B8E53 /* SBJsonTokeniser.m in Sources */ = {isa = PBXBuildFile; fileRef = A51B778A17050C71002B8E53 /* SBJsonTokeniser.m */; };
- A51B779917050C71002B8E53 /* SBJsonUTF8Stream.m in Sources */ = {isa = PBXBuildFile; fileRef = A51B778C17050C71002B8E53 /* SBJsonUTF8Stream.m */; };
- A51B779A17050C71002B8E53 /* SBJsonWriter.m in Sources */ = {isa = PBXBuildFile; fileRef = A51B778E17050C71002B8E53 /* SBJsonWriter.m */; };
- A51B77A117050F8C002B8E53 /* MessagesDatabase.m in Sources */ = {isa = PBXBuildFile; fileRef = A51B77A017050F8C002B8E53 /* MessagesDatabase.m */; };
+ 05B94BF218BD28E400708011 /* VerificationViewControllerTests.m in Sources */ = {isa = PBXBuildFile; fileRef = 05B94BF118BD28E400708011 /* VerificationViewControllerTests.m */; };
+ 05B94BF418BD2EA000708011 /* TextSecureStoryboard.storyboard in Resources */ = {isa = PBXBuildFile; fileRef = A53718CD16FF95DF00C6FCCF /* TextSecureStoryboard.storyboard */; };
+ 4C0ACB4B186C876200B328D5 /* TSMessageConversationCell.m in Sources */ = {isa = PBXBuildFile; fileRef = 4C0ACB4A186C876200B328D5 /* TSMessageConversationCell.m */; };
+ 4C77526D18707A46000FCCA6 /* PasswordUnlockViewController.m in Sources */ = {isa = PBXBuildFile; fileRef = 4C77526B18707A46000FCCA6 /* PasswordUnlockViewController.m */; };
+ 4CFDC8D2187215F600BDB649 /* TSMessagesDatabaseTests.m in Sources */ = {isa = PBXBuildFile; fileRef = 4CFDC8D1187215F600BDB649 /* TSMessagesDatabaseTests.m */; };
+ 6FBCCDFF18D5361300C5B5F5 /* TSMessageIncomingTest.m in Sources */ = {isa = PBXBuildFile; fileRef = 6FBCCDFD18D5361300C5B5F5 /* TSMessageIncomingTest.m */; };
+ 6FBCCE0018D5361300C5B5F5 /* TSMessageOutgoingTest.m in Sources */ = {isa = PBXBuildFile; fileRef = 6FBCCDFE18D5361300C5B5F5 /* TSMessageOutgoingTest.m */; };
+ 6FCE040B18D427CE00C33B34 /* TSReplaceSegue.m in Sources */ = {isa = PBXBuildFile; fileRef = 6FCE040818D427CE00C33B34 /* TSReplaceSegue.m */; };
+ 6FCE040C18D427CE00C33B34 /* TSStartOverSegue.m in Sources */ = {isa = PBXBuildFile; fileRef = 6FCE040A18D427CE00C33B34 /* TSStartOverSegue.m */; };
+ 8C49FC1018497E86006132F6 /* TSStorageError.m in Sources */ = {isa = PBXBuildFile; fileRef = 8C49FC0F18497E86006132F6 /* TSStorageError.m */; };
+ 8CF7BD8F187097570023A781 /* TSECKeyPairTests.m in Sources */ = {isa = PBXBuildFile; fileRef = 8CF7BD8E187097570023A781 /* TSECKeyPairTests.m */; };
+ 8CF7BD951870C8450023A781 /* TSStorageMasterKey.m in Sources */ = {isa = PBXBuildFile; fileRef = 8CF7BD941870C8450023A781 /* TSStorageMasterKey.m */; };
+ 8CF7BD9B1870F23D0023A781 /* TSUserKeysDatabase.m in Sources */ = {isa = PBXBuildFile; fileRef = 8CF7BD9A1870F23D0023A781 /* TSUserKeysDatabase.m */; };
+ 8CF7BD9D18711B140023A781 /* TSUserKeysDatabaseTests.m in Sources */ = {isa = PBXBuildFile; fileRef = 8CF7BD9C18711B140023A781 /* TSUserKeysDatabaseTests.m */; };
+ 8CF7BD9F187130F80023A781 /* TSStorageMasterKeyTests.m in Sources */ = {isa = PBXBuildFile; fileRef = 8CF7BD9E187130F80023A781 /* TSStorageMasterKeyTests.m */; };
+ 8CF7BDA1187137640023A781 /* TSEncryptedDatabaseTests.m in Sources */ = {isa = PBXBuildFile; fileRef = 8CF7BDA0187137640023A781 /* TSEncryptedDatabaseTests.m */; };
+ A513465D18D65D97005B4FA3 /* TSDeregisterAccountRequest.m in Sources */ = {isa = PBXBuildFile; fileRef = A513465C18D65D97005B4FA3 /* TSDeregisterAccountRequest.m */; };
+ A5145B31184AAD51007BDC73 /* TSMessage.m in Sources */ = {isa = PBXBuildFile; fileRef = A5145B30184AAD51007BDC73 /* TSMessage.m */; };
+ A5145B37184B66AD007BDC73 /* TSRequestAttachmentId.m in Sources */ = {isa = PBXBuildFile; fileRef = A5145B36184B66AD007BDC73 /* TSRequestAttachmentId.m */; };
+ A5145B3A184B68EA007BDC73 /* TSRequestAttachment.m in Sources */ = {isa = PBXBuildFile; fileRef = A5145B39184B68EA007BDC73 /* TSRequestAttachment.m */; };
+ A5145B3D184B6F35007BDC73 /* TSAttachmentManager.m in Sources */ = {isa = PBXBuildFile; fileRef = A5145B3C184B6F35007BDC73 /* TSAttachmentManager.m */; };
+ A515AFDB180966E30084ABA5 /* TSMessagesDatabase.m in Sources */ = {isa = PBXBuildFile; fileRef = A515AFDA180966E30084ABA5 /* TSMessagesDatabase.m */; };
+ A5169D08170FEA8D00A2CE9E /* VerificationViewController.m in Sources */ = {isa = PBXBuildFile; fileRef = A5169CFC170FEA8D00A2CE9E /* VerificationViewController.m */; };
+ A5169D09170FEA8D00A2CE9E /* TextSecureViewController.m in Sources */ = {isa = PBXBuildFile; fileRef = A5169CFD170FEA8D00A2CE9E /* TextSecureViewController.m */; };
+ A5169D0C170FEA8D00A2CE9E /* CountryViewController.m in Sources */ = {isa = PBXBuildFile; fileRef = A5169D04170FEA8D00A2CE9E /* CountryViewController.m */; };
+ A5169D0D170FEA8D00A2CE9E /* CountrySegue.m in Sources */ = {isa = PBXBuildFile; fileRef = A5169D06170FEA8D00A2CE9E /* CountrySegue.m */; };
+ A5169D1E170FEB1900A2CE9E /* FilePath.m in Sources */ = {isa = PBXBuildFile; fileRef = A5169D15170FEB1900A2CE9E /* FilePath.m */; };
+ A5169D1F170FEB1900A2CE9E /* NSString+Conversion.m in Sources */ = {isa = PBXBuildFile; fileRef = A5169D17170FEB1900A2CE9E /* NSString+Conversion.m */; };
+ A5169D20170FEB1900A2CE9E /* Constants.m in Sources */ = {isa = PBXBuildFile; fileRef = A5169D19170FEB1900A2CE9E /* Constants.m */; };
+ A5169D21170FEB1900A2CE9E /* NSData+Conversion.m in Sources */ = {isa = PBXBuildFile; fileRef = A5169D1B170FEB1900A2CE9E /* NSData+Conversion.m */; };
+ A5169D2B170FEB8F00A2CE9E /* KeychainWrapper.m in Sources */ = {isa = PBXBuildFile; fileRef = A5169D23170FEB8E00A2CE9E /* KeychainWrapper.m */; };
+ A5169D2E170FEB8F00A2CE9E /* Cryptography.m in Sources */ = {isa = PBXBuildFile; fileRef = A5169D26170FEB8F00A2CE9E /* Cryptography.m */; };
+ A5169D3D170FEDC600A2CE9E /* main.m in Sources */ = {isa = PBXBuildFile; fileRef = A5169D39170FEDC600A2CE9E /* main.m */; };
+ A5195B9118CBBC0300AFEE04 /* contact_mask.png in Resources */ = {isa = PBXBuildFile; fileRef = A5195B8D18CBBC0300AFEE04 /* contact_mask.png */; };
+ A5195B9218CBBC0300AFEE04 /* contact_mask@2x.png in Resources */ = {isa = PBXBuildFile; fileRef = A5195B8E18CBBC0300AFEE04 /* contact_mask@2x.png */; };
+ A5195B9318CBBC0300AFEE04 /* Default_person.png in Resources */ = {isa = PBXBuildFile; fileRef = A5195B8F18CBBC0300AFEE04 /* Default_person.png */; };
+ A5195B9418CBBC0300AFEE04 /* Default_person@2x.png in Resources */ = {isa = PBXBuildFile; fileRef = A5195B9018CBBC0300AFEE04 /* Default_person@2x.png */; };
+ A5195B9618CBC00100AFEE04 /* apple_logo_animated.gif in Resources */ = {isa = PBXBuildFile; fileRef = A5195B9518CBC00100AFEE04 /* apple_logo_animated.gif */; };
A51B77A317051096002B8E53 /* libsqlite3.dylib in Frameworks */ = {isa = PBXBuildFile; fileRef = A51B77A217051096002B8E53 /* libsqlite3.dylib */; };
- A51B77A617051417002B8E53 /* Message.m in Sources */ = {isa = PBXBuildFile; fileRef = A51B77A517051417002B8E53 /* Message.m */; };
- A51B77AC17052C5C002B8E53 /* FilePath.m in Sources */ = {isa = PBXBuildFile; fileRef = A51B77AB17052C5C002B8E53 /* FilePath.m */; };
- A51B77B3170561C3002B8E53 /* textsecure-verifybutton.png in Resources */ = {isa = PBXBuildFile; fileRef = A51B77AE170561C3002B8E53 /* textsecure-verifybutton.png */; };
- A51B77B4170561C3002B8E53 /* textsecure-selectyourcountry-field.png in Resources */ = {isa = PBXBuildFile; fileRef = A51B77AF170561C3002B8E53 /* textsecure-selectyourcountry-field.png */; };
- A51B77B5170561C3002B8E53 /* textsecure-phonenumber-field.png in Resources */ = {isa = PBXBuildFile; fileRef = A51B77B0170561C3002B8E53 /* textsecure-phonenumber-field.png */; };
- A51B77B6170561C3002B8E53 /* textsecure-gettingstarted-menubar.png in Resources */ = {isa = PBXBuildFile; fileRef = A51B77B1170561C3002B8E53 /* textsecure-gettingstarted-menubar.png */; };
- A51B77B7170561C3002B8E53 /* textsecure-countrycode-field.png in Resources */ = {isa = PBXBuildFile; fileRef = A51B77B2170561C3002B8E53 /* textsecure-countrycode-field.png */; };
- A51B77B917058E6C002B8E53 /* TextSecure-Global-canvas.png in Resources */ = {isa = PBXBuildFile; fileRef = A51B77B817058E6C002B8E53 /* TextSecure-Global-canvas.png */; };
+ A52CE05D1862D88B00AF9E39 /* CryptographyTests.mm in Sources */ = {isa = PBXBuildFile; fileRef = A52CE05C1862D88B00AF9E39 /* CryptographyTests.mm */; };
+ A52ECA7C17ED097300C80BC7 /* NSData+Base64.m in Sources */ = {isa = PBXBuildFile; fileRef = A52ECA7B17ED097300C80BC7 /* NSData+Base64.m */; };
+ A530CB04184A02620052B615 /* TSRecipientPrekeyRequest.m in Sources */ = {isa = PBXBuildFile; fileRef = A530CB03184A02620052B615 /* TSRecipientPrekeyRequest.m */; };
A53718B616FF95DF00C6FCCF /* UIKit.framework in Frameworks */ = {isa = PBXBuildFile; fileRef = A53718B516FF95DF00C6FCCF /* UIKit.framework */; };
A53718B816FF95DF00C6FCCF /* Foundation.framework in Frameworks */ = {isa = PBXBuildFile; fileRef = A53718B716FF95DF00C6FCCF /* Foundation.framework */; };
A53718BA16FF95DF00C6FCCF /* CoreGraphics.framework in Frameworks */ = {isa = PBXBuildFile; fileRef = A53718B916FF95DF00C6FCCF /* CoreGraphics.framework */; };
- A53718C216FF95DF00C6FCCF /* main.m in Sources */ = {isa = PBXBuildFile; fileRef = A53718C116FF95DF00C6FCCF /* main.m */; };
A53718C616FF95DF00C6FCCF /* AppDelegate.m in Sources */ = {isa = PBXBuildFile; fileRef = A53718C516FF95DF00C6FCCF /* AppDelegate.m */; };
- A53718CF16FF95DF00C6FCCF /* MainStoryboard.storyboard in Resources */ = {isa = PBXBuildFile; fileRef = A53718CD16FF95DF00C6FCCF /* MainStoryboard.storyboard */; };
- A53718D216FF95DF00C6FCCF /* SMSViewController.m in Sources */ = {isa = PBXBuildFile; fileRef = A53718D116FF95DF00C6FCCF /* SMSViewController.m */; };
- A53718DA16FF95DF00C6FCCF /* SenTestingKit.framework in Frameworks */ = {isa = PBXBuildFile; fileRef = A53718D916FF95DF00C6FCCF /* SenTestingKit.framework */; };
- A53718DB16FF95DF00C6FCCF /* UIKit.framework in Frameworks */ = {isa = PBXBuildFile; fileRef = A53718B516FF95DF00C6FCCF /* UIKit.framework */; };
- A53718DC16FF95DF00C6FCCF /* Foundation.framework in Frameworks */ = {isa = PBXBuildFile; fileRef = A53718B716FF95DF00C6FCCF /* Foundation.framework */; };
- A53718E416FF95DF00C6FCCF /* InfoPlist.strings in Resources */ = {isa = PBXBuildFile; fileRef = A53718E216FF95DF00C6FCCF /* InfoPlist.strings */; };
- A53718E716FF95DF00C6FCCF /* TextSecureiOSTests.m in Sources */ = {isa = PBXBuildFile; fileRef = A53718E616FF95DF00C6FCCF /* TextSecureiOSTests.m */; };
+ A53718CF16FF95DF00C6FCCF /* TextSecureStoryboard.storyboard in Resources */ = {isa = PBXBuildFile; fileRef = A53718CD16FF95DF00C6FCCF /* TextSecureStoryboard.storyboard */; };
A53718F116FF98C100C6FCCF /* MessageUI.framework in Frameworks */ = {isa = PBXBuildFile; fileRef = A53718F016FF98C100C6FCCF /* MessageUI.framework */; };
- A53718FF16FFB6F800C6FCCF /* tutorial_ok_button.png in Resources */ = {isa = PBXBuildFile; fileRef = A53718FD16FFB6F800C6FCCF /* tutorial_ok_button.png */; };
- A537190016FFB6F800C6FCCF /* tutorial_ok_button@2x.png in Resources */ = {isa = PBXBuildFile; fileRef = A53718FE16FFB6F800C6FCCF /* tutorial_ok_button@2x.png */; };
- A537190216FFB92C00C6FCCF /* tutorial_tutorial_arrow.png in Resources */ = {isa = PBXBuildFile; fileRef = A537190116FFB92C00C6FCCF /* tutorial_tutorial_arrow.png */; };
- A537190516FFBEE300C6FCCF /* VerificationViewController.m in Sources */ = {isa = PBXBuildFile; fileRef = A537190416FFBEE300C6FCCF /* VerificationViewController.m */; };
- A537190816FFC45C00C6FCCF /* textsecure.png in Resources */ = {isa = PBXBuildFile; fileRef = A537190616FFC45B00C6FCCF /* textsecure.png */; };
A537190916FFC45C00C6FCCF /* textsecure@2x.png in Resources */ = {isa = PBXBuildFile; fileRef = A537190716FFC45B00C6FCCF /* textsecure@2x.png */; };
- A537190C1700247600C6FCCF /* Server.m in Sources */ = {isa = PBXBuildFile; fileRef = A537190B1700247400C6FCCF /* Server.m */; };
- A537190F1700284900C6FCCF /* Constants.m in Sources */ = {isa = PBXBuildFile; fileRef = A537190E1700284800C6FCCF /* Constants.m */; };
A53719251700D71B00C6FCCF /* CoreTelephony.framework in Frameworks */ = {isa = PBXBuildFile; fileRef = A53719241700D71A00C6FCCF /* CoreTelephony.framework */; };
- A53719281700DC3300C6FCCF /* CountryViewController.m in Sources */ = {isa = PBXBuildFile; fileRef = A53719271700DC3100C6FCCF /* CountryViewController.m */; };
- A537192E1700FAAB00C6FCCF /* CountryCodes.plist in Resources */ = {isa = PBXBuildFile; fileRef = A537192D1700FAA900C6FCCF /* CountryCodes.plist */; };
- A53719311701040600C6FCCF /* CountrySegue.m in Sources */ = {isa = PBXBuildFile; fileRef = A53719301701040400C6FCCF /* CountrySegue.m */; };
A537294B17011A5200C6FCCF /* ad.png in Resources */ = {isa = PBXBuildFile; fileRef = A53727FE17011A4F00C6FCCF /* ad.png */; };
A537294C17011A5200C6FCCF /* ae.png in Resources */ = {isa = PBXBuildFile; fileRef = A53727FF17011A4F00C6FCCF /* ae.png */; };
A537294D17011A5200C6FCCF /* af.png in Resources */ = {isa = PBXBuildFile; fileRef = A537280017011A4F00C6FCCF /* af.png */; };
@@ -304,7 +302,6 @@
A5372A3D17011A5300C6FCCF /* qu.png in Resources */ = {isa = PBXBuildFile; fileRef = A53728F017011A5100C6FCCF /* qu.png */; };
A5372A3E17011A5300C6FCCF /* qu@2x.png in Resources */ = {isa = PBXBuildFile; fileRef = A53728F117011A5100C6FCCF /* qu@2x.png */; };
A5372A3F17011A5300C6FCCF /* re.png in Resources */ = {isa = PBXBuildFile; fileRef = A53728F217011A5100C6FCCF /* re.png */; };
- A5372A4017011A5300C6FCCF /* resizeAll.sh in Resources */ = {isa = PBXBuildFile; fileRef = A53728F317011A5100C6FCCF /* resizeAll.sh */; };
A5372A4117011A5300C6FCCF /* ro.png in Resources */ = {isa = PBXBuildFile; fileRef = A53728F417011A5100C6FCCF /* ro.png */; };
A5372A4217011A5300C6FCCF /* ro@2x.png in Resources */ = {isa = PBXBuildFile; fileRef = A53728F517011A5100C6FCCF /* ro@2x.png */; };
A5372A4317011A5300C6FCCF /* rs.png in Resources */ = {isa = PBXBuildFile; fileRef = A53728F617011A5100C6FCCF /* rs.png */; };
@@ -392,38 +389,92 @@
A5372A9517011A5300C6FCCF /* zh.png in Resources */ = {isa = PBXBuildFile; fileRef = A537294817011A5200C6FCCF /* zh.png */; };
A5372A9617011A5300C6FCCF /* zm.png in Resources */ = {isa = PBXBuildFile; fileRef = A537294917011A5200C6FCCF /* zm.png */; };
A5372A9717011A5300C6FCCF /* zw.png in Resources */ = {isa = PBXBuildFile; fileRef = A537294A17011A5200C6FCCF /* zw.png */; };
- A5F15A9817027FD000856385 /* Cryptography.m in Sources */ = {isa = PBXBuildFile; fileRef = A5F15A9717027FCF00856385 /* Cryptography.m */; };
+ A538A27E1869DC6500CD0A3D /* TSKeyManager.m in Sources */ = {isa = PBXBuildFile; fileRef = A538A27D1869DC6500CD0A3D /* TSKeyManager.m */; };
+ A539ED1118D5E06F006C1A61 /* TSSettingsViewController.m in Sources */ = {isa = PBXBuildFile; fileRef = A539ED1018D5E06F006C1A61 /* TSSettingsViewController.m */; };
+ A5620DEF186BD4FA0033483E /* TSSubmitMessageRequest.m in Sources */ = {isa = PBXBuildFile; fileRef = A5620DEE186BD4FA0033483E /* TSSubmitMessageRequest.m */; };
+ A56312F818C85B6500222F99 /* Settings.bundle in Resources */ = {isa = PBXBuildFile; fileRef = A56312F718C85B6500222F99 /* Settings.bundle */; };
+ A56312FB18C9A45A00222F99 /* TSWaitingPushMessageDatabase.m in Sources */ = {isa = PBXBuildFile; fileRef = A56312FA18C9A45A00222F99 /* TSWaitingPushMessageDatabase.m */; };
+ A56312FD18C9BDCD00222F99 /* TSWaitingPushMessageDatabaseTests.m in Sources */ = {isa = PBXBuildFile; fileRef = A56312FC18C9BDCD00222F99 /* TSWaitingPushMessageDatabaseTests.m */; };
+ A56807B818CCAF2A0059083C /* TSGroupContext.m in Sources */ = {isa = PBXBuildFile; fileRef = A56807B718CCAF290059083C /* TSGroupContext.m */; };
+ A568910117E2F37000C360A1 /* CoreText.framework in Frameworks */ = {isa = PBXBuildFile; fileRef = A568910017E2F37000C360A1 /* CoreText.framework */; };
+ A568910317E2F37A00C360A1 /* QuartzCore.framework in Frameworks */ = {isa = PBXBuildFile; fileRef = A568910217E2F37A00C360A1 /* QuartzCore.framework */; };
+ A56D31B9180FCA840093D51B /* TSRegisterPrekeysRequest.m in Sources */ = {isa = PBXBuildFile; fileRef = A56D31B8180FCA840093D51B /* TSRegisterPrekeysRequest.m */; };
+ A580D2BD19323E4A00D6C1CC /* UIColor+TextSecure.m in Sources */ = {isa = PBXBuildFile; fileRef = A580D2BC19323E4A00D6C1CC /* UIColor+TextSecure.m */; };
+ A5DE19D2170702E900ACAFDD /* AddressBookUI.framework in Frameworks */ = {isa = PBXBuildFile; fileRef = A5DE19D1170702E900ACAFDD /* AddressBookUI.framework */; };
+ A5DE19D4170702ED00ACAFDD /* AddressBook.framework in Frameworks */ = {isa = PBXBuildFile; fileRef = A5DE19D3170702ED00ACAFDD /* AddressBook.framework */; };
+ A5E6CBFC187629D4002A1735 /* MediaPlayer.framework in Frameworks */ = {isa = PBXBuildFile; fileRef = A5E6CBFB187629D4002A1735 /* MediaPlayer.framework */; };
+ A5E6CC09187AC6D5002A1735 /* TSDownloadAttachment.m in Sources */ = {isa = PBXBuildFile; fileRef = A5E6CC08187AC6D5002A1735 /* TSDownloadAttachment.m */; };
+ A5E6CC6D187D0F4B002A1735 /* IncomingPushMessageSignal.pb.mm in Sources */ = {isa = PBXBuildFile; fileRef = A5E6CC62187D0F4B002A1735 /* IncomingPushMessageSignal.pb.mm */; };
+ A5E6CC6E187D0F4B002A1735 /* IncomingPushMessageSignal.proto in Resources */ = {isa = PBXBuildFile; fileRef = A5E6CC63187D0F4B002A1735 /* IncomingPushMessageSignal.proto */; };
+ A5E6CC6F187D0F4B002A1735 /* PreKeyWhisperMessage.pb.mm in Sources */ = {isa = PBXBuildFile; fileRef = A5E6CC65187D0F4B002A1735 /* PreKeyWhisperMessage.pb.mm */; };
+ A5E6CC70187D0F4B002A1735 /* PreKeyWhisperMessage.proto in Resources */ = {isa = PBXBuildFile; fileRef = A5E6CC66187D0F4B002A1735 /* PreKeyWhisperMessage.proto */; };
+ A5E6CC71187D0F4B002A1735 /* PushMessageContent.pb.mm in Sources */ = {isa = PBXBuildFile; fileRef = A5E6CC68187D0F4B002A1735 /* PushMessageContent.pb.mm */; };
+ A5E6CC72187D0F4B002A1735 /* PushMessageContent.proto in Resources */ = {isa = PBXBuildFile; fileRef = A5E6CC69187D0F4B002A1735 /* PushMessageContent.proto */; };
+ A5E6CC73187D0F4B002A1735 /* WhisperMessage.pb.mm in Sources */ = {isa = PBXBuildFile; fileRef = A5E6CC6B187D0F4B002A1735 /* WhisperMessage.pb.mm */; };
+ A5E6CC74187D0F4B002A1735 /* WhisperMessage.proto in Resources */ = {isa = PBXBuildFile; fileRef = A5E6CC6C187D0F4B002A1735 /* WhisperMessage.proto */; };
+ A5E6CC82187D0FF1002A1735 /* TSEncryptedWhisperMessage.mm in Sources */ = {isa = PBXBuildFile; fileRef = A5E6CC76187D0FF1002A1735 /* TSEncryptedWhisperMessage.mm */; };
+ A5E6CC83187D0FF1002A1735 /* TSMessageSignal.mm in Sources */ = {isa = PBXBuildFile; fileRef = A5E6CC78187D0FF1002A1735 /* TSMessageSignal.mm */; };
+ A5E6CC84187D0FF1002A1735 /* TSPreKeyWhisperMessage.mm in Sources */ = {isa = PBXBuildFile; fileRef = A5E6CC7A187D0FF1002A1735 /* TSPreKeyWhisperMessage.mm */; };
+ A5E6CC85187D0FF1002A1735 /* TSProtocolBufferWrapper.mm in Sources */ = {isa = PBXBuildFile; fileRef = A5E6CC7C187D0FF1002A1735 /* TSProtocolBufferWrapper.mm */; };
+ A5E6CC86187D0FF1002A1735 /* TSPushMessageContent.mm in Sources */ = {isa = PBXBuildFile; fileRef = A5E6CC7E187D0FF1002A1735 /* TSPushMessageContent.mm */; };
+ A5E6CC90187D1E41002A1735 /* TSWhisperMessage.mm in Sources */ = {isa = PBXBuildFile; fileRef = A5E6CC8F187D1E41002A1735 /* TSWhisperMessage.mm */; };
+ A5E6CC9B18826005002A1735 /* TSProtocolBufferWrapperTests.mm in Sources */ = {isa = PBXBuildFile; fileRef = A5E6CC9A18826005002A1735 /* TSProtocolBufferWrapperTests.mm */; };
+ A5E6CC9E18837C31002A1735 /* TSAxolotlRatchet.mm in Sources */ = {isa = PBXBuildFile; fileRef = A5E6CC9D18837C31002A1735 /* TSAxolotlRatchet.mm */; };
A5F15A9A170280B700856385 /* Security.framework in Frameworks */ = {isa = PBXBuildFile; fileRef = A5F15A99170280B700856385 /* Security.framework */; };
- A5F15A9D1702949200856385 /* NSData+Conversion.m in Sources */ = {isa = PBXBuildFile; fileRef = A5F15A9C1702949100856385 /* NSData+Conversion.m */; };
- A5F15AA01702997A00856385 /* KeychainWrapper.m in Sources */ = {isa = PBXBuildFile; fileRef = A5F15A9F1702997A00856385 /* KeychainWrapper.m */; };
- A5F15AA61702DF6E00856385 /* libssl.a in Frameworks */ = {isa = PBXBuildFile; fileRef = A5F15AA41702DF6E00856385 /* libssl.a */; };
- A5F15AA71702DF6E00856385 /* libcrypto.a in Frameworks */ = {isa = PBXBuildFile; fileRef = A5F15AA51702DF6E00856385 /* libcrypto.a */; };
- A5F15B2F1703975F00856385 /* RNCryptor.m in Sources */ = {isa = PBXBuildFile; fileRef = A5F15B221703975F00856385 /* RNCryptor.m */; };
- A5F15B301703975F00856385 /* RNCryptorEngine.m in Sources */ = {isa = PBXBuildFile; fileRef = A5F15B241703975F00856385 /* RNCryptorEngine.m */; };
- A5F15B311703975F00856385 /* RNDecryptor.m in Sources */ = {isa = PBXBuildFile; fileRef = A5F15B261703975F00856385 /* RNDecryptor.m */; };
- A5F15B321703975F00856385 /* RNEncryptor.m in Sources */ = {isa = PBXBuildFile; fileRef = A5F15B281703975F00856385 /* RNEncryptor.m */; };
- A5F15B331703975F00856385 /* RNOpenSSLCryptor.m in Sources */ = {isa = PBXBuildFile; fileRef = A5F15B2A1703975F00856385 /* RNOpenSSLCryptor.m */; };
- A5F15B341703975F00856385 /* RNOpenSSLDecryptor.m in Sources */ = {isa = PBXBuildFile; fileRef = A5F15B2C1703975F00856385 /* RNOpenSSLDecryptor.m */; };
- A5F15B351703975F00856385 /* RNOpenSSLEncryptor.m in Sources */ = {isa = PBXBuildFile; fileRef = A5F15B2E1703975F00856385 /* RNOpenSSLEncryptor.m */; };
- A5F15B381703B98F00856385 /* NSString+Conversion.m in Sources */ = {isa = PBXBuildFile; fileRef = A5F15B371703B98F00856385 /* NSString+Conversion.m */; };
- A5F15B3B1703D15000856385 /* UserDefaults.m in Sources */ = {isa = PBXBuildFile; fileRef = A5F15B3A1703D14F00856385 /* UserDefaults.m */; };
- A5F15B3E1703EB9F00856385 /* Default@2x.png in Resources */ = {isa = PBXBuildFile; fileRef = A5F15B3C1703EB9F00856385 /* Default@2x.png */; };
- A5F15B3F1703EB9F00856385 /* Default.png in Resources */ = {isa = PBXBuildFile; fileRef = A5F15B3D1703EB9F00856385 /* Default.png */; };
- A5F15B491703EE2F00856385 /* Default-568h@2x.png in Resources */ = {isa = PBXBuildFile; fileRef = A5F15B481703EE2F00856385 /* Default-568h@2x.png */; };
- A5F15B551703F20D00856385 /* OpenSans-SemiboldItalic.ttf in Resources */ = {isa = PBXBuildFile; fileRef = A5F15B4B1703F20D00856385 /* OpenSans-SemiboldItalic.ttf */; };
- A5F15B561703F20D00856385 /* OpenSans-Semibold.ttf in Resources */ = {isa = PBXBuildFile; fileRef = A5F15B4C1703F20D00856385 /* OpenSans-Semibold.ttf */; };
- A5F15B571703F20D00856385 /* OpenSans-Regular.ttf in Resources */ = {isa = PBXBuildFile; fileRef = A5F15B4D1703F20D00856385 /* OpenSans-Regular.ttf */; };
- A5F15B581703F20D00856385 /* OpenSans-LightItalic.ttf in Resources */ = {isa = PBXBuildFile; fileRef = A5F15B4E1703F20D00856385 /* OpenSans-LightItalic.ttf */; };
- A5F15B591703F20D00856385 /* OpenSans-Light.ttf in Resources */ = {isa = PBXBuildFile; fileRef = A5F15B4F1703F20D00856385 /* OpenSans-Light.ttf */; };
- A5F15B5A1703F20D00856385 /* OpenSans-Italic.ttf in Resources */ = {isa = PBXBuildFile; fileRef = A5F15B501703F20D00856385 /* OpenSans-Italic.ttf */; };
- A5F15B5B1703F20D00856385 /* OpenSans-ExtraBoldItalic.ttf in Resources */ = {isa = PBXBuildFile; fileRef = A5F15B511703F20D00856385 /* OpenSans-ExtraBoldItalic.ttf */; };
- A5F15B5C1703F20D00856385 /* OpenSans-ExtraBold.ttf in Resources */ = {isa = PBXBuildFile; fileRef = A5F15B521703F20D00856385 /* OpenSans-ExtraBold.ttf */; };
- A5F15B5D1703F20D00856385 /* OpenSans-BoldItalic.ttf in Resources */ = {isa = PBXBuildFile; fileRef = A5F15B531703F20D00856385 /* OpenSans-BoldItalic.ttf */; };
- A5F15B5E1703F20D00856385 /* OpenSans-Bold.ttf in Resources */ = {isa = PBXBuildFile; fileRef = A5F15B541703F20D00856385 /* OpenSans-Bold.ttf */; };
+ A5FBAB95184E980E0012E9A5 /* TSUploadAttachment.m in Sources */ = {isa = PBXBuildFile; fileRef = A5FBAB94184E980E0012E9A5 /* TSUploadAttachment.m */; };
+ A5FE7D84191FA1FA0022C3F7 /* TSPresentIdentityQRCodeViewController.m in Sources */ = {isa = PBXBuildFile; fileRef = A5FE7D7F191FA1FA0022C3F7 /* TSPresentIdentityQRCodeViewController.m */; };
+ A5FE7D85191FA1FA0022C3F7 /* TSScanIdentityBarcodeViewController.m in Sources */ = {isa = PBXBuildFile; fileRef = A5FE7D81191FA1FA0022C3F7 /* TSScanIdentityBarcodeViewController.m */; };
+ A5FE7D86191FA1FA0022C3F7 /* TSVerifyIdentityViewController.m in Sources */ = {isa = PBXBuildFile; fileRef = A5FE7D83191FA1FA0022C3F7 /* TSVerifyIdentityViewController.m */; };
+ A6F91EC0B0694C57850C03BA /* libPods.a in Frameworks */ = {isa = PBXBuildFile; fileRef = AD77BB98A5B14A3490A31E06 /* libPods.a */; };
+ B602B96318CE9A4B00181564 /* TSReceivingChain.m in Sources */ = {isa = PBXBuildFile; fileRef = B602B96218CE9A4B00181564 /* TSReceivingChain.m */; };
+ B621AA731928032D00085CF7 /* TSSocketManager.m in Sources */ = {isa = PBXBuildFile; fileRef = B621AA721928032D00085CF7 /* TSSocketManager.m */; };
+ B635B3C7182181E1003CE732 /* TSMessageViewController.m in Sources */ = {isa = PBXBuildFile; fileRef = B635B390182181E1003CE732 /* TSMessageViewController.m */; };
+ B635B3ED18218456003CE732 /* CoreAudio.framework in Frameworks */ = {isa = PBXBuildFile; fileRef = B635B3EC18218456003CE732 /* CoreAudio.framework */; };
+ B635B3EF18218481003CE732 /* AudioToolbox.framework in Frameworks */ = {isa = PBXBuildFile; fileRef = B635B3EE18218481003CE732 /* AudioToolbox.framework */; };
+ B639AF0D17F5A68100B2244D /* TSNetworkManager.m in Sources */ = {isa = PBXBuildFile; fileRef = B639AF0C17F5A68100B2244D /* TSNetworkManager.m */; };
+ B639AF1117F5AAA300B2244D /* TSRequest.m in Sources */ = {isa = PBXBuildFile; fileRef = B639AF1017F5AAA300B2244D /* TSRequest.m */; };
+ B639F69F180955E100B7DF00 /* TSServerCodeVerificationRequest.m in Sources */ = {isa = PBXBuildFile; fileRef = B639F69E180955E100B7DF00 /* TSServerCodeVerificationRequest.m */; };
+ B63A72161808B8AF00C353F2 /* VerificationCodeViewController.m in Sources */ = {isa = PBXBuildFile; fileRef = B63A72151808B8AF00C353F2 /* VerificationCodeViewController.m */; };
+ B63A72181808BD3D00C353F2 /* gcm.textsecure.whispersystems.org.cer in Resources */ = {isa = PBXBuildFile; fileRef = B63A72171808BD3D00C353F2 /* gcm.textsecure.whispersystems.org.cer */; };
+ B643D7DE189EB9020025C6F3 /* TSContactPickerViewController.m in Sources */ = {isa = PBXBuildFile; fileRef = B643D7DD189EB9020025C6F3 /* TSContactPickerViewController.m */; };
+ B644F95E18DF5D3700D41FA8 /* NSString+randomString.m in Sources */ = {isa = PBXBuildFile; fileRef = B644F95D18DF5D3700D41FA8 /* NSString+randomString.m */; };
+ B646538A18E74D9C006010E0 /* TSDerivedSecrets.m in Sources */ = {isa = PBXBuildFile; fileRef = B646538918E74D9C006010E0 /* TSDerivedSecrets.m */; };
+ B67E30F618CE19E4008502F5 /* TSContact.m in Sources */ = {isa = PBXBuildFile; fileRef = B67E30F518CE19E4008502F5 /* TSContact.m */; };
+ B67E30F918CE1AA8008502F5 /* TSGroupSetupViewController.m in Sources */ = {isa = PBXBuildFile; fileRef = B67E30F818CE1AA8008502F5 /* TSGroupSetupViewController.m */; };
+ B684346618D1FF2B007AEDF6 /* TSSendingChain.m in Sources */ = {isa = PBXBuildFile; fileRef = B684346518D1FF2B007AEDF6 /* TSSendingChain.m */; };
+ B68BFDF2180987C6005CC817 /* TSSetMasterPasswordViewController.m in Sources */ = {isa = PBXBuildFile; fileRef = B68BFDF1180987C6005CC817 /* TSSetMasterPasswordViewController.m */; };
+ B6B478E61809E7F5005DDE12 /* TSContactsIntersectionRequest.m in Sources */ = {isa = PBXBuildFile; fileRef = B6B478E51809E7F5005DDE12 /* TSContactsIntersectionRequest.m */; };
+ B6C5AE5817C212330022EA53 /* Default-568h@2x.png in Resources */ = {isa = PBXBuildFile; fileRef = B6C5AE5717C212330022EA53 /* Default-568h@2x.png */; };
+ B6C5FA7418CE344700ECC200 /* TSConversation.m in Sources */ = {isa = PBXBuildFile; fileRef = B6C5FA7318CE344700ECC200 /* TSConversation.m */; };
+ B6C5FA7718CE354800ECC200 /* TSSession.m in Sources */ = {isa = PBXBuildFile; fileRef = B6C5FA7618CE354800ECC200 /* TSSession.m */; };
+ B6C5FA7A18CE355500ECC200 /* TSChainKey.m in Sources */ = {isa = PBXBuildFile; fileRef = B6C5FA7918CE355500ECC200 /* TSChainKey.m */; };
+ B6C5FA7D18CE357200ECC200 /* TSGroup.m in Sources */ = {isa = PBXBuildFile; fileRef = B6C5FA7C18CE357200ECC200 /* TSGroup.m */; };
+ B6C5FA8018CE3AD600ECC200 /* TSAttachment.m in Sources */ = {isa = PBXBuildFile; fileRef = B6C5FA7F18CE3AD600ECC200 /* TSAttachment.m */; };
+ B6C5FA8318CE3AED00ECC200 /* TSContactManager.m in Sources */ = {isa = PBXBuildFile; fileRef = B6C5FA8218CE3AED00ECC200 /* TSContactManager.m */; };
+ B6C5FA8618CE3AFB00ECC200 /* TSECKeyPair.m in Sources */ = {isa = PBXBuildFile; fileRef = B6C5FA8518CE3AFB00ECC200 /* TSECKeyPair.m */; };
+ B6C5FA8918CE3B0900ECC200 /* TSMessageIncoming.m in Sources */ = {isa = PBXBuildFile; fileRef = B6C5FA8818CE3B0900ECC200 /* TSMessageIncoming.m */; };
+ B6C5FA8C18CE3B1000ECC200 /* TSMessageOutgoing.m in Sources */ = {isa = PBXBuildFile; fileRef = B6C5FA8B18CE3B1000ECC200 /* TSMessageOutgoing.m */; };
+ B6C5FA8F18CE3B2000ECC200 /* TSPrekey.m in Sources */ = {isa = PBXBuildFile; fileRef = B6C5FA8E18CE3B2000ECC200 /* TSPrekey.m */; };
+ B6C5FA9218CE3B3900ECC200 /* TSMessageKeys.m in Sources */ = {isa = PBXBuildFile; fileRef = B6C5FA9118CE3B3900ECC200 /* TSMessageKeys.m */; };
+ B6C5FA9518CE3B4600ECC200 /* TSMessagesManager.mm in Sources */ = {isa = PBXBuildFile; fileRef = B6C5FA9418CE3B4600ECC200 /* TSMessagesManager.mm */; };
+ B6C5FA9818CE3B6300ECC200 /* RKCK.m in Sources */ = {isa = PBXBuildFile; fileRef = B6C5FA9718CE3B6300ECC200 /* RKCK.m */; };
+ B6C5FA9918CE3BB900ECC200 /* TSDatabaseManager.m in Sources */ = {isa = PBXBuildFile; fileRef = 8CF7BD971870D9450023A781 /* TSDatabaseManager.m */; };
+ B6CA8B2418E38F0D0088BC0C /* TSAxolotlConsistencyTest.m in Sources */ = {isa = PBXBuildFile; fileRef = B6CA8B2318E38F0D0088BC0C /* TSAxolotlConsistencyTest.m */; };
+ B6CC7EAB18D52F09006480FB /* Constants.m in Sources */ = {isa = PBXBuildFile; fileRef = A5169D19170FEB1900A2CE9E /* Constants.m */; };
+ B6D23DAF18A91E9800F7E932 /* TSRegisterForPushRequest.m in Sources */ = {isa = PBXBuildFile; fileRef = B68A2291180AC32C00D93C16 /* TSRegisterForPushRequest.m */; };
+ B6E2CFB317F7926000200B69 /* TSRequestVerificationCodeRequest.m in Sources */ = {isa = PBXBuildFile; fileRef = B6E2CFB217F7926000200B69 /* TSRequestVerificationCodeRequest.m */; };
+ B6E2CFB617F794F600200B69 /* NSString+escape.m in Sources */ = {isa = PBXBuildFile; fileRef = B6E2CFB517F794F600200B69 /* NSString+escape.m */; };
+ B6F10B1717EF4A3A00723719 /* NSLocale+phonePrefixes.m in Sources */ = {isa = PBXBuildFile; fileRef = B6F10B1617EF4A3A00723719 /* NSLocale+phonePrefixes.m */; };
+ B6F10B1C17EF61FE00723719 /* CountryCodes.plist in Resources */ = {isa = PBXBuildFile; fileRef = B6F10B1B17EF61FE00723719 /* CountryCodes.plist */; };
+ B6F10B1F17EF8F3C00723719 /* NSString+PhoneFormating.m in Sources */ = {isa = PBXBuildFile; fileRef = B6F10B1E17EF8F3C00723719 /* NSString+PhoneFormating.m */; };
+ B6F7FEC018D77E1500ECC4A2 /* NSData+TSKeyVersion.m in Sources */ = {isa = PBXBuildFile; fileRef = B6F7FEBF18D77E1500ECC4A2 /* NSData+TSKeyVersion.m */; };
+ CE74D2F57964464494640956 /* libPods.a in Frameworks */ = {isa = PBXBuildFile; fileRef = AD77BB98A5B14A3490A31E06 /* libPods.a */; };
+ F8694B5E18C5268500A44474 /* padlock_prompt.png in Resources */ = {isa = PBXBuildFile; fileRef = F8694B5D18C5268500A44474 /* padlock_prompt.png */; };
+ FCD30FC918FDBBB7003BD188 /* SignUpStepsViewController.m in Sources */ = {isa = PBXBuildFile; fileRef = FCD30FC818FDBBB7003BD188 /* SignUpStepsViewController.m */; };
/* End PBXBuildFile section */
/* Begin PBXContainerItemProxy section */
- A53718DD16FF95DF00C6FCCF /* PBXContainerItemProxy */ = {
+ 8C42C14718551B8C000DD353 /* PBXContainerItemProxy */ = {
isa = PBXContainerItemProxy;
containerPortal = A53718AA16FF95DF00C6FCCF /* Project object */;
proxyType = 1;
@@ -433,90 +484,93 @@
/* End PBXContainerItemProxy section */
/* Begin PBXFileReference section */
- A51B776417050C42002B8E53 /* FMDatabase.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = FMDatabase.h; sourceTree = ""; };
- A51B776517050C42002B8E53 /* FMDatabase.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; path = FMDatabase.m; sourceTree = ""; };
- A51B776617050C42002B8E53 /* FMDatabaseAdditions.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = FMDatabaseAdditions.h; sourceTree = ""; };
- A51B776717050C42002B8E53 /* FMDatabaseAdditions.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; path = FMDatabaseAdditions.m; sourceTree = ""; };
- A51B776817050C42002B8E53 /* FMDatabasePool.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = FMDatabasePool.h; sourceTree = ""; };
- A51B776917050C42002B8E53 /* FMDatabasePool.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; path = FMDatabasePool.m; sourceTree = ""; };
- A51B776A17050C42002B8E53 /* FMDatabaseQueue.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = FMDatabaseQueue.h; sourceTree = ""; };
- A51B776B17050C42002B8E53 /* FMDatabaseQueue.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; path = FMDatabaseQueue.m; sourceTree = ""; };
- A51B776D17050C42002B8E53 /* FMResultSet.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = FMResultSet.h; sourceTree = ""; };
- A51B776E17050C42002B8E53 /* FMResultSet.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; path = FMResultSet.m; sourceTree = ""; };
- A51B777617050C71002B8E53 /* NSObject+SBJson.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = "NSObject+SBJson.h"; sourceTree = ""; };
- A51B777717050C71002B8E53 /* NSObject+SBJson.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; path = "NSObject+SBJson.m"; sourceTree = ""; };
- A51B777817050C71002B8E53 /* SBJson.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = SBJson.h; sourceTree = ""; };
- A51B777917050C71002B8E53 /* SBJsonParser.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = SBJsonParser.h; sourceTree = ""; };
- A51B777A17050C71002B8E53 /* SBJsonParser.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; path = SBJsonParser.m; sourceTree = ""; };
- A51B777B17050C71002B8E53 /* SBJsonStreamParser.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = SBJsonStreamParser.h; sourceTree = ""; };
- A51B777C17050C71002B8E53 /* SBJsonStreamParser.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; path = SBJsonStreamParser.m; sourceTree = ""; };
- A51B777D17050C71002B8E53 /* SBJsonStreamParserAccumulator.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = SBJsonStreamParserAccumulator.h; sourceTree = ""; };
- A51B777E17050C71002B8E53 /* SBJsonStreamParserAccumulator.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; path = SBJsonStreamParserAccumulator.m; sourceTree = ""; };
- A51B777F17050C71002B8E53 /* SBJsonStreamParserAdapter.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = SBJsonStreamParserAdapter.h; sourceTree = ""; };
- A51B778017050C71002B8E53 /* SBJsonStreamParserAdapter.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; path = SBJsonStreamParserAdapter.m; sourceTree = ""; };
- A51B778117050C71002B8E53 /* SBJsonStreamParserState.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = SBJsonStreamParserState.h; sourceTree = ""; };
- A51B778217050C71002B8E53 /* SBJsonStreamParserState.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; path = SBJsonStreamParserState.m; sourceTree = ""; };
- A51B778317050C71002B8E53 /* SBJsonStreamWriter.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = SBJsonStreamWriter.h; sourceTree = ""; };
- A51B778417050C71002B8E53 /* SBJsonStreamWriter.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; path = SBJsonStreamWriter.m; sourceTree = ""; };
- A51B778517050C71002B8E53 /* SBJsonStreamWriterAccumulator.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = SBJsonStreamWriterAccumulator.h; sourceTree = ""; };
- A51B778617050C71002B8E53 /* SBJsonStreamWriterAccumulator.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; path = SBJsonStreamWriterAccumulator.m; sourceTree = ""; };
- A51B778717050C71002B8E53 /* SBJsonStreamWriterState.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = SBJsonStreamWriterState.h; sourceTree = ""; };
- A51B778817050C71002B8E53 /* SBJsonStreamWriterState.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; path = SBJsonStreamWriterState.m; sourceTree = ""; };
- A51B778917050C71002B8E53 /* SBJsonTokeniser.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = SBJsonTokeniser.h; sourceTree = ""; };
- A51B778A17050C71002B8E53 /* SBJsonTokeniser.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; path = SBJsonTokeniser.m; sourceTree = ""; };
- A51B778B17050C71002B8E53 /* SBJsonUTF8Stream.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = SBJsonUTF8Stream.h; sourceTree = ""; };
- A51B778C17050C71002B8E53 /* SBJsonUTF8Stream.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; path = SBJsonUTF8Stream.m; sourceTree = ""; };
- A51B778D17050C71002B8E53 /* SBJsonWriter.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = SBJsonWriter.h; sourceTree = ""; };
- A51B778E17050C71002B8E53 /* SBJsonWriter.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; path = SBJsonWriter.m; sourceTree = ""; };
- A51B779F17050F8C002B8E53 /* MessagesDatabase.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = MessagesDatabase.h; sourceTree = ""; };
- A51B77A017050F8C002B8E53 /* MessagesDatabase.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; path = MessagesDatabase.m; sourceTree = ""; };
+ 05B94BF118BD28E400708011 /* VerificationViewControllerTests.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; path = VerificationViewControllerTests.m; sourceTree = ""; wrapsLines = 1; };
+ 4C0ACB49186C876200B328D5 /* TSMessageConversationCell.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; name = TSMessageConversationCell.h; path = Views/Cells/TSMessageConversationCell.h; sourceTree = ""; };
+ 4C0ACB4A186C876200B328D5 /* TSMessageConversationCell.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; name = TSMessageConversationCell.m; path = Views/Cells/TSMessageConversationCell.m; sourceTree = ""; };
+ 4C77526A18707A46000FCCA6 /* PasswordUnlockViewController.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; name = PasswordUnlockViewController.h; path = ViewControllers/PasswordUnlockViewController.h; sourceTree = ""; };
+ 4C77526B18707A46000FCCA6 /* PasswordUnlockViewController.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; name = PasswordUnlockViewController.m; path = ViewControllers/PasswordUnlockViewController.m; sourceTree = ""; };
+ 4CFDC8D1187215F600BDB649 /* TSMessagesDatabaseTests.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; path = TSMessagesDatabaseTests.m; sourceTree = ""; };
+ 6FBCCDFD18D5361300C5B5F5 /* TSMessageIncomingTest.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; path = TSMessageIncomingTest.m; sourceTree = ""; };
+ 6FBCCDFE18D5361300C5B5F5 /* TSMessageOutgoingTest.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; path = TSMessageOutgoingTest.m; sourceTree = ""; };
+ 6FCE040718D427CE00C33B34 /* TSReplaceSegue.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; name = TSReplaceSegue.h; path = Utility/TSReplaceSegue.h; sourceTree = ""; };
+ 6FCE040818D427CE00C33B34 /* TSReplaceSegue.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; name = TSReplaceSegue.m; path = Utility/TSReplaceSegue.m; sourceTree = ""; };
+ 6FCE040918D427CE00C33B34 /* TSStartOverSegue.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; name = TSStartOverSegue.h; path = Utility/TSStartOverSegue.h; sourceTree = ""; };
+ 6FCE040A18D427CE00C33B34 /* TSStartOverSegue.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; name = TSStartOverSegue.m; path = Utility/TSStartOverSegue.m; sourceTree = ""; };
+ 8C42C13918551B8C000DD353 /* TextSecureiOS Tests.xctest */ = {isa = PBXFileReference; explicitFileType = wrapper.cfbundle; includeInIndex = 0; path = "TextSecureiOS Tests.xctest"; sourceTree = BUILT_PRODUCTS_DIR; };
+ 8C42C13A18551B8C000DD353 /* XCTest.framework */ = {isa = PBXFileReference; lastKnownFileType = wrapper.framework; name = XCTest.framework; path = Library/Frameworks/XCTest.framework; sourceTree = DEVELOPER_DIR; };
+ 8C42C14018551B8C000DD353 /* TextSecureiOS Tests-Info.plist */ = {isa = PBXFileReference; lastKnownFileType = text.plist.xml; path = "TextSecureiOS Tests-Info.plist"; sourceTree = ""; };
+ 8C42C14218551B8C000DD353 /* en */ = {isa = PBXFileReference; lastKnownFileType = text.plist.strings; name = en; path = en.lproj/InfoPlist.strings; sourceTree = ""; };
+ 8C42C14618551B8C000DD353 /* TextSecureiOS Tests-Prefix.pch */ = {isa = PBXFileReference; lastKnownFileType = sourcecode.c.h; path = "TextSecureiOS Tests-Prefix.pch"; sourceTree = ""; };
+ 8C49FC0E18497E86006132F6 /* TSStorageError.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; name = TSStorageError.h; path = Model/TSStorageError.h; sourceTree = ""; };
+ 8C49FC0F18497E86006132F6 /* TSStorageError.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; name = TSStorageError.m; path = Model/TSStorageError.m; sourceTree = ""; };
+ 8CF7BD8E187097570023A781 /* TSECKeyPairTests.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; path = TSECKeyPairTests.m; sourceTree = ""; };
+ 8CF7BD931870C8450023A781 /* TSStorageMasterKey.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; name = TSStorageMasterKey.h; path = Security/TSStorageMasterKey.h; sourceTree = ""; };
+ 8CF7BD941870C8450023A781 /* TSStorageMasterKey.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; name = TSStorageMasterKey.m; path = Security/TSStorageMasterKey.m; sourceTree = ""; };
+ 8CF7BD961870D9450023A781 /* TSDatabaseManager.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; name = TSDatabaseManager.h; path = Model/TSDatabaseManager.h; sourceTree = ""; };
+ 8CF7BD971870D9450023A781 /* TSDatabaseManager.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; name = TSDatabaseManager.m; path = Model/TSDatabaseManager.m; sourceTree = ""; };
+ 8CF7BD991870F23D0023A781 /* TSUserKeysDatabase.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; name = TSUserKeysDatabase.h; path = Model/TSUserKeysDatabase.h; sourceTree = ""; };
+ 8CF7BD9A1870F23D0023A781 /* TSUserKeysDatabase.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; name = TSUserKeysDatabase.m; path = Model/TSUserKeysDatabase.m; sourceTree = ""; };
+ 8CF7BD9C18711B140023A781 /* TSUserKeysDatabaseTests.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; name = TSUserKeysDatabaseTests.m; path = "TextSecureiOS Tests/TSUserKeysDatabaseTests.m"; sourceTree = SOURCE_ROOT; };
+ 8CF7BD9E187130F80023A781 /* TSStorageMasterKeyTests.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; name = TSStorageMasterKeyTests.m; path = "TextSecureiOS Tests/TSStorageMasterKeyTests.m"; sourceTree = SOURCE_ROOT; };
+ 8CF7BDA0187137640023A781 /* TSEncryptedDatabaseTests.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; path = TSEncryptedDatabaseTests.m; sourceTree = ""; };
+ 950A849531204A2EBF7475C2 /* Pods.xcconfig */ = {isa = PBXFileReference; includeInIndex = 1; lastKnownFileType = text.xcconfig; name = Pods.xcconfig; path = Pods/Pods.xcconfig; sourceTree = SOURCE_ROOT; };
+ A513465B18D65D97005B4FA3 /* TSDeregisterAccountRequest.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; name = TSDeregisterAccountRequest.h; path = TextSecureiOS/Networking/Requests/TSDeregisterAccountRequest.h; sourceTree = ""; };
+ A513465C18D65D97005B4FA3 /* TSDeregisterAccountRequest.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; name = TSDeregisterAccountRequest.m; path = TextSecureiOS/Networking/Requests/TSDeregisterAccountRequest.m; sourceTree = ""; };
+ A5145B2F184AAD51007BDC73 /* TSMessage.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; name = TSMessage.h; path = Model/TSMessage.h; sourceTree = ""; };
+ A5145B30184AAD51007BDC73 /* TSMessage.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; name = TSMessage.m; path = Model/TSMessage.m; sourceTree = ""; };
+ A5145B35184B66AD007BDC73 /* TSRequestAttachmentId.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; name = TSRequestAttachmentId.h; path = TextSecureiOS/Networking/Requests/TSRequestAttachmentId.h; sourceTree = ""; };
+ A5145B36184B66AD007BDC73 /* TSRequestAttachmentId.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; name = TSRequestAttachmentId.m; path = TextSecureiOS/Networking/Requests/TSRequestAttachmentId.m; sourceTree = ""; };
+ A5145B38184B68EA007BDC73 /* TSRequestAttachment.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; name = TSRequestAttachment.h; path = TextSecureiOS/Networking/Requests/TSRequestAttachment.h; sourceTree = ""; };
+ A5145B39184B68EA007BDC73 /* TSRequestAttachment.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; name = TSRequestAttachment.m; path = TextSecureiOS/Networking/Requests/TSRequestAttachment.m; sourceTree = ""; };
+ A5145B3B184B6F35007BDC73 /* TSAttachmentManager.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; name = TSAttachmentManager.h; path = TextSecureiOS/Networking/TSAttachmentManager.h; sourceTree = ""; };
+ A5145B3C184B6F35007BDC73 /* TSAttachmentManager.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; name = TSAttachmentManager.m; path = TextSecureiOS/Networking/TSAttachmentManager.m; sourceTree = ""; };
+ A515AFD9180966E30084ABA5 /* TSMessagesDatabase.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; name = TSMessagesDatabase.h; path = Model/TSMessagesDatabase.h; sourceTree = ""; };
+ A515AFDA180966E30084ABA5 /* TSMessagesDatabase.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; name = TSMessagesDatabase.m; path = Model/TSMessagesDatabase.m; sourceTree = ""; };
+ A5169CFC170FEA8D00A2CE9E /* VerificationViewController.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; name = VerificationViewController.m; path = ViewControllers/VerificationViewController.m; sourceTree = ""; };
+ A5169CFD170FEA8D00A2CE9E /* TextSecureViewController.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; name = TextSecureViewController.m; path = ViewControllers/TextSecureViewController.m; sourceTree = ""; };
+ A5169CFF170FEA8D00A2CE9E /* VerificationViewController.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; name = VerificationViewController.h; path = ViewControllers/VerificationViewController.h; sourceTree = ""; };
+ A5169D00170FEA8D00A2CE9E /* TextSecureViewController.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; name = TextSecureViewController.h; path = ViewControllers/TextSecureViewController.h; sourceTree = ""; };
+ A5169D04170FEA8D00A2CE9E /* CountryViewController.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; name = CountryViewController.m; path = ViewControllers/CountryViewController.m; sourceTree = ""; };
+ A5169D05170FEA8D00A2CE9E /* CountryViewController.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; name = CountryViewController.h; path = ViewControllers/CountryViewController.h; sourceTree = ""; };
+ A5169D06170FEA8D00A2CE9E /* CountrySegue.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; name = CountrySegue.m; path = ViewControllers/CountrySegue.m; sourceTree = ""; };
+ A5169D07170FEA8D00A2CE9E /* CountrySegue.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; name = CountrySegue.h; path = ViewControllers/CountrySegue.h; sourceTree = ""; };
+ A5169D14170FEB1900A2CE9E /* FilePath.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; name = FilePath.h; path = Utility/FilePath.h; sourceTree = ""; };
+ A5169D15170FEB1900A2CE9E /* FilePath.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; name = FilePath.m; path = Utility/FilePath.m; sourceTree = ""; };
+ A5169D16170FEB1900A2CE9E /* NSString+Conversion.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; name = "NSString+Conversion.h"; path = "TextSecureiOS/Utility/NSString+Conversion.h"; sourceTree = ""; };
+ A5169D17170FEB1900A2CE9E /* NSString+Conversion.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; name = "NSString+Conversion.m"; path = "TextSecureiOS/Utility/NSString+Conversion.m"; sourceTree = ""; };
+ A5169D18170FEB1900A2CE9E /* Constants.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; name = Constants.h; path = Utility/Constants.h; sourceTree = ""; };
+ A5169D19170FEB1900A2CE9E /* Constants.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; name = Constants.m; path = Utility/Constants.m; sourceTree = ""; };
+ A5169D1A170FEB1900A2CE9E /* NSData+Conversion.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; name = "NSData+Conversion.h"; path = "TextSecureiOS/Utility/NSData+Conversion.h"; sourceTree = ""; };
+ A5169D1B170FEB1900A2CE9E /* NSData+Conversion.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; name = "NSData+Conversion.m"; path = "TextSecureiOS/Utility/NSData+Conversion.m"; sourceTree = ""; };
+ A5169D23170FEB8E00A2CE9E /* KeychainWrapper.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; name = KeychainWrapper.m; path = Security/KeychainWrapper.m; sourceTree = ""; };
+ A5169D26170FEB8F00A2CE9E /* Cryptography.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; name = Cryptography.m; path = Security/Cryptography.m; sourceTree = ""; };
+ A5169D27170FEB8F00A2CE9E /* Cryptography.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; name = Cryptography.h; path = Security/Cryptography.h; sourceTree = ""; };
+ A5169D2A170FEB8F00A2CE9E /* KeychainWrapper.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; name = KeychainWrapper.h; path = Security/KeychainWrapper.h; sourceTree = ""; };
+ A5169D39170FEDC600A2CE9E /* main.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; path = main.m; sourceTree = ""; };
+ A5169D3A170FEDC600A2CE9E /* TextSecureiOS-Info.plist */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = text.plist.xml; path = "TextSecureiOS-Info.plist"; sourceTree = ""; };
+ A5169D3C170FEDC600A2CE9E /* TextSecureiOS-Prefix.pch */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = "TextSecureiOS-Prefix.pch"; sourceTree = ""; };
+ A5195B8D18CBBC0300AFEE04 /* contact_mask.png */ = {isa = PBXFileReference; lastKnownFileType = image.png; name = contact_mask.png; path = TextSecureiOSAssets/contact_mask.png; sourceTree = ""; };
+ A5195B8E18CBBC0300AFEE04 /* contact_mask@2x.png */ = {isa = PBXFileReference; lastKnownFileType = image.png; name = "contact_mask@2x.png"; path = "TextSecureiOSAssets/contact_mask@2x.png"; sourceTree = ""; };
+ A5195B8F18CBBC0300AFEE04 /* Default_person.png */ = {isa = PBXFileReference; lastKnownFileType = image.png; name = Default_person.png; path = TextSecureiOSAssets/Default_person.png; sourceTree = ""; };
+ A5195B9018CBBC0300AFEE04 /* Default_person@2x.png */ = {isa = PBXFileReference; lastKnownFileType = image.png; name = "Default_person@2x.png"; path = "TextSecureiOSAssets/Default_person@2x.png"; sourceTree = ""; };
+ A5195B9518CBC00100AFEE04 /* apple_logo_animated.gif */ = {isa = PBXFileReference; lastKnownFileType = image.gif; name = apple_logo_animated.gif; path = TextSecureiOSAssets/apple_logo_animated.gif; sourceTree = ""; };
A51B77A217051096002B8E53 /* libsqlite3.dylib */ = {isa = PBXFileReference; lastKnownFileType = "compiled.mach-o.dylib"; name = libsqlite3.dylib; path = usr/lib/libsqlite3.dylib; sourceTree = SDKROOT; };
- A51B77A417051417002B8E53 /* Message.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = Message.h; sourceTree = ""; };
- A51B77A517051417002B8E53 /* Message.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; path = Message.m; sourceTree = ""; };
- A51B77AA17052C5B002B8E53 /* FilePath.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = FilePath.h; sourceTree = ""; };
- A51B77AB17052C5C002B8E53 /* FilePath.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; path = FilePath.m; sourceTree = ""; };
- A51B77AE170561C3002B8E53 /* textsecure-verifybutton.png */ = {isa = PBXFileReference; lastKnownFileType = image.png; name = "textsecure-verifybutton.png"; path = "TextSecureiOSAssets/vc-verification/textsecure-verifybutton.png"; sourceTree = ""; };
- A51B77AF170561C3002B8E53 /* textsecure-selectyourcountry-field.png */ = {isa = PBXFileReference; lastKnownFileType = image.png; name = "textsecure-selectyourcountry-field.png"; path = "TextSecureiOSAssets/vc-verification/textsecure-selectyourcountry-field.png"; sourceTree = ""; };
- A51B77B0170561C3002B8E53 /* textsecure-phonenumber-field.png */ = {isa = PBXFileReference; lastKnownFileType = image.png; name = "textsecure-phonenumber-field.png"; path = "TextSecureiOSAssets/vc-verification/textsecure-phonenumber-field.png"; sourceTree = ""; };
- A51B77B1170561C3002B8E53 /* textsecure-gettingstarted-menubar.png */ = {isa = PBXFileReference; lastKnownFileType = image.png; name = "textsecure-gettingstarted-menubar.png"; path = "TextSecureiOSAssets/vc-verification/textsecure-gettingstarted-menubar.png"; sourceTree = ""; };
- A51B77B2170561C3002B8E53 /* textsecure-countrycode-field.png */ = {isa = PBXFileReference; lastKnownFileType = image.png; name = "textsecure-countrycode-field.png"; path = "TextSecureiOSAssets/vc-verification/textsecure-countrycode-field.png"; sourceTree = ""; };
- A51B77B817058E6C002B8E53 /* TextSecure-Global-canvas.png */ = {isa = PBXFileReference; lastKnownFileType = image.png; name = "TextSecure-Global-canvas.png"; path = "TextSecureiOSAssets/TextSecure-Global-canvas.png"; sourceTree = ""; };
+ A52CE05C1862D88B00AF9E39 /* CryptographyTests.mm */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.cpp.objcpp; path = CryptographyTests.mm; sourceTree = ""; };
+ A52ECA7A17ED097300C80BC7 /* NSData+Base64.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; name = "NSData+Base64.h"; path = "TextSecureiOS/Utility/NSData+Base64.h"; sourceTree = ""; };
+ A52ECA7B17ED097300C80BC7 /* NSData+Base64.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; name = "NSData+Base64.m"; path = "TextSecureiOS/Utility/NSData+Base64.m"; sourceTree = ""; };
+ A530CB02184A02620052B615 /* TSRecipientPrekeyRequest.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; name = TSRecipientPrekeyRequest.h; path = TextSecureiOS/Networking/Requests/TSRecipientPrekeyRequest.h; sourceTree = ""; };
+ A530CB03184A02620052B615 /* TSRecipientPrekeyRequest.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; name = TSRecipientPrekeyRequest.m; path = TextSecureiOS/Networking/Requests/TSRecipientPrekeyRequest.m; sourceTree = ""; };
A53718B216FF95DF00C6FCCF /* TextSecureiOS.app */ = {isa = PBXFileReference; explicitFileType = wrapper.application; includeInIndex = 0; path = TextSecureiOS.app; sourceTree = BUILT_PRODUCTS_DIR; };
A53718B516FF95DF00C6FCCF /* UIKit.framework */ = {isa = PBXFileReference; lastKnownFileType = wrapper.framework; name = UIKit.framework; path = System/Library/Frameworks/UIKit.framework; sourceTree = SDKROOT; };
A53718B716FF95DF00C6FCCF /* Foundation.framework */ = {isa = PBXFileReference; lastKnownFileType = wrapper.framework; name = Foundation.framework; path = System/Library/Frameworks/Foundation.framework; sourceTree = SDKROOT; };
A53718B916FF95DF00C6FCCF /* CoreGraphics.framework */ = {isa = PBXFileReference; lastKnownFileType = wrapper.framework; name = CoreGraphics.framework; path = System/Library/Frameworks/CoreGraphics.framework; sourceTree = SDKROOT; };
- A53718C116FF95DF00C6FCCF /* main.m */ = {isa = PBXFileReference; lastKnownFileType = sourcecode.c.objc; path = main.m; sourceTree = ""; };
- A53718C316FF95DF00C6FCCF /* TextSecureiOS-Prefix.pch */ = {isa = PBXFileReference; lastKnownFileType = sourcecode.c.h; path = "TextSecureiOS-Prefix.pch"; sourceTree = ""; };
A53718C416FF95DF00C6FCCF /* AppDelegate.h */ = {isa = PBXFileReference; lastKnownFileType = sourcecode.c.h; path = AppDelegate.h; sourceTree = ""; };
A53718C516FF95DF00C6FCCF /* AppDelegate.m */ = {isa = PBXFileReference; lastKnownFileType = sourcecode.c.objc; path = AppDelegate.m; sourceTree = ""; };
- A53718CE16FF95DF00C6FCCF /* en */ = {isa = PBXFileReference; lastKnownFileType = file.storyboard; name = en; path = en.lproj/MainStoryboard.storyboard; sourceTree = ""; };
- A53718D016FF95DF00C6FCCF /* SMSViewController.h */ = {isa = PBXFileReference; lastKnownFileType = sourcecode.c.h; path = SMSViewController.h; sourceTree = ""; };
- A53718D116FF95DF00C6FCCF /* SMSViewController.m */ = {isa = PBXFileReference; lastKnownFileType = sourcecode.c.objc; path = SMSViewController.m; sourceTree = ""; };
- A53718D816FF95DF00C6FCCF /* TextSecureiOSTests.octest */ = {isa = PBXFileReference; explicitFileType = wrapper.cfbundle; includeInIndex = 0; path = TextSecureiOSTests.octest; sourceTree = BUILT_PRODUCTS_DIR; };
+ A53718CE16FF95DF00C6FCCF /* en */ = {isa = PBXFileReference; lastKnownFileType = file.storyboard; name = en; path = en.lproj/TextSecureStoryboard.storyboard; sourceTree = ""; };
A53718D916FF95DF00C6FCCF /* SenTestingKit.framework */ = {isa = PBXFileReference; lastKnownFileType = wrapper.framework; name = SenTestingKit.framework; path = Library/Frameworks/SenTestingKit.framework; sourceTree = DEVELOPER_DIR; };
- A53718E116FF95DF00C6FCCF /* TextSecureiOSTests-Info.plist */ = {isa = PBXFileReference; lastKnownFileType = text.plist.xml; path = "TextSecureiOSTests-Info.plist"; sourceTree = ""; };
- A53718E316FF95DF00C6FCCF /* en */ = {isa = PBXFileReference; lastKnownFileType = text.plist.strings; name = en; path = en.lproj/InfoPlist.strings; sourceTree = ""; };
- A53718E516FF95DF00C6FCCF /* TextSecureiOSTests.h */ = {isa = PBXFileReference; lastKnownFileType = sourcecode.c.h; path = TextSecureiOSTests.h; sourceTree = ""; };
- A53718E616FF95DF00C6FCCF /* TextSecureiOSTests.m */ = {isa = PBXFileReference; lastKnownFileType = sourcecode.c.objc; path = TextSecureiOSTests.m; sourceTree = ""; };
A53718F016FF98C100C6FCCF /* MessageUI.framework */ = {isa = PBXFileReference; lastKnownFileType = wrapper.framework; name = MessageUI.framework; path = System/Library/Frameworks/MessageUI.framework; sourceTree = SDKROOT; };
- A53718FB16FFA12000C6FCCF /* TextSecureiOS-Info.plist */ = {isa = PBXFileReference; lastKnownFileType = text.plist.xml; path = "TextSecureiOS-Info.plist"; sourceTree = ""; };
- A53718FD16FFB6F800C6FCCF /* tutorial_ok_button.png */ = {isa = PBXFileReference; lastKnownFileType = image.png; name = tutorial_ok_button.png; path = TextSecureiOSAssets/tutorial_ok_button.png; sourceTree = ""; };
- A53718FE16FFB6F800C6FCCF /* tutorial_ok_button@2x.png */ = {isa = PBXFileReference; lastKnownFileType = image.png; name = "tutorial_ok_button@2x.png"; path = "TextSecureiOSAssets/tutorial_ok_button@2x.png"; sourceTree = ""; };
- A537190116FFB92C00C6FCCF /* tutorial_tutorial_arrow.png */ = {isa = PBXFileReference; lastKnownFileType = image.png; name = tutorial_tutorial_arrow.png; path = TextSecureiOSAssets/tutorial_tutorial_arrow.png; sourceTree = ""; };
- A537190316FFBEE200C6FCCF /* VerificationViewController.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = VerificationViewController.h; sourceTree = ""; };
- A537190416FFBEE300C6FCCF /* VerificationViewController.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; path = VerificationViewController.m; sourceTree = ""; };
- A537190616FFC45B00C6FCCF /* textsecure.png */ = {isa = PBXFileReference; lastKnownFileType = image.png; name = textsecure.png; path = TextSecureiOSAssets/MainIcon/textsecure.png; sourceTree = ""; };
A537190716FFC45B00C6FCCF /* textsecure@2x.png */ = {isa = PBXFileReference; lastKnownFileType = image.png; name = "textsecure@2x.png"; path = "TextSecureiOSAssets/MainIcon/textsecure@2x.png"; sourceTree = ""; };
- A537190A1700247400C6FCCF /* Server.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = Server.h; sourceTree = ""; };
- A537190B1700247400C6FCCF /* Server.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; path = Server.m; sourceTree = ""; };
- A537190D1700284800C6FCCF /* Constants.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = Constants.h; sourceTree = ""; };
- A537190E1700284800C6FCCF /* Constants.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; path = Constants.m; sourceTree = ""; };
A53719241700D71A00C6FCCF /* CoreTelephony.framework */ = {isa = PBXFileReference; lastKnownFileType = wrapper.framework; name = CoreTelephony.framework; path = System/Library/Frameworks/CoreTelephony.framework; sourceTree = SDKROOT; };
- A53719261700DC2F00C6FCCF /* CountryViewController.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = CountryViewController.h; sourceTree = ""; };
- A53719271700DC3100C6FCCF /* CountryViewController.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; path = CountryViewController.m; sourceTree = ""; };
- A537192D1700FAA900C6FCCF /* CountryCodes.plist */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = text.plist.xml; path = CountryCodes.plist; sourceTree = ""; };
- A537192F1701040200C6FCCF /* CountrySegue.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = CountrySegue.h; sourceTree = ""; };
- A53719301701040400C6FCCF /* CountrySegue.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; path = CountrySegue.m; sourceTree = ""; };
A53727FE17011A4F00C6FCCF /* ad.png */ = {isa = PBXFileReference; lastKnownFileType = image.png; path = ad.png; sourceTree = ""; };
A53727FF17011A4F00C6FCCF /* ae.png */ = {isa = PBXFileReference; lastKnownFileType = image.png; path = ae.png; sourceTree = ""; };
A537280017011A4F00C6FCCF /* af.png */ = {isa = PBXFileReference; lastKnownFileType = image.png; path = af.png; sourceTree = ""; };
@@ -762,7 +816,6 @@
A53728F017011A5100C6FCCF /* qu.png */ = {isa = PBXFileReference; lastKnownFileType = image.png; path = qu.png; sourceTree = ""; };
A53728F117011A5100C6FCCF /* qu@2x.png */ = {isa = PBXFileReference; lastKnownFileType = image.png; path = "qu@2x.png"; sourceTree = ""; };
A53728F217011A5100C6FCCF /* re.png */ = {isa = PBXFileReference; lastKnownFileType = image.png; path = re.png; sourceTree = ""; };
- A53728F317011A5100C6FCCF /* resizeAll.sh */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = text.script.sh; path = resizeAll.sh; sourceTree = ""; };
A53728F417011A5100C6FCCF /* ro.png */ = {isa = PBXFileReference; lastKnownFileType = image.png; path = ro.png; sourceTree = ""; };
A53728F517011A5100C6FCCF /* ro@2x.png */ = {isa = PBXFileReference; lastKnownFileType = image.png; path = "ro@2x.png"; sourceTree = ""; };
A53728F617011A5100C6FCCF /* rs.png */ = {isa = PBXFileReference; lastKnownFileType = image.png; path = rs.png; sourceTree = ""; };
@@ -850,130 +903,168 @@
A537294817011A5200C6FCCF /* zh.png */ = {isa = PBXFileReference; lastKnownFileType = image.png; path = zh.png; sourceTree = ""; };
A537294917011A5200C6FCCF /* zm.png */ = {isa = PBXFileReference; lastKnownFileType = image.png; path = zm.png; sourceTree = ""; };
A537294A17011A5200C6FCCF /* zw.png */ = {isa = PBXFileReference; lastKnownFileType = image.png; path = zw.png; sourceTree = ""; };
- A5F15A9617027FCF00856385 /* Cryptography.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = Cryptography.h; sourceTree = ""; };
- A5F15A9717027FCF00856385 /* Cryptography.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; path = Cryptography.m; sourceTree = ""; };
+ A538A27C1869DC6500CD0A3D /* TSKeyManager.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; name = TSKeyManager.h; path = Security/TSKeyManager.h; sourceTree = ""; };
+ A538A27D1869DC6500CD0A3D /* TSKeyManager.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; name = TSKeyManager.m; path = Security/TSKeyManager.m; sourceTree = ""; };
+ A539ED0F18D5E06F006C1A61 /* TSSettingsViewController.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; name = TSSettingsViewController.h; path = ViewControllers/TSSettingsViewController.h; sourceTree = ""; };
+ A539ED1018D5E06F006C1A61 /* TSSettingsViewController.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; name = TSSettingsViewController.m; path = ViewControllers/TSSettingsViewController.m; sourceTree = ""; };
+ A5620DED186BD4FA0033483E /* TSSubmitMessageRequest.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; name = TSSubmitMessageRequest.h; path = TextSecureiOS/Networking/Requests/TSSubmitMessageRequest.h; sourceTree = ""; };
+ A5620DEE186BD4FA0033483E /* TSSubmitMessageRequest.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; name = TSSubmitMessageRequest.m; path = TextSecureiOS/Networking/Requests/TSSubmitMessageRequest.m; sourceTree = ""; };
+ A56312F718C85B6500222F99 /* Settings.bundle */ = {isa = PBXFileReference; lastKnownFileType = "wrapper.plug-in"; path = Settings.bundle; sourceTree = ""; };
+ A56312F918C9A45A00222F99 /* TSWaitingPushMessageDatabase.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; name = TSWaitingPushMessageDatabase.h; path = Model/TSWaitingPushMessageDatabase.h; sourceTree = ""; };
+ A56312FA18C9A45A00222F99 /* TSWaitingPushMessageDatabase.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; name = TSWaitingPushMessageDatabase.m; path = Model/TSWaitingPushMessageDatabase.m; sourceTree = ""; };
+ A56312FC18C9BDCD00222F99 /* TSWaitingPushMessageDatabaseTests.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; path = TSWaitingPushMessageDatabaseTests.m; sourceTree = ""; };
+ A56807B618CCAF290059083C /* TSGroupContext.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; name = TSGroupContext.h; path = Model/TSGroupContext.h; sourceTree = ""; };
+ A56807B718CCAF290059083C /* TSGroupContext.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; name = TSGroupContext.m; path = Model/TSGroupContext.m; sourceTree = ""; };
+ A568910017E2F37000C360A1 /* CoreText.framework */ = {isa = PBXFileReference; lastKnownFileType = wrapper.framework; name = CoreText.framework; path = System/Library/Frameworks/CoreText.framework; sourceTree = SDKROOT; };
+ A568910217E2F37A00C360A1 /* QuartzCore.framework */ = {isa = PBXFileReference; lastKnownFileType = wrapper.framework; name = QuartzCore.framework; path = System/Library/Frameworks/QuartzCore.framework; sourceTree = SDKROOT; };
+ A56D31B7180FCA840093D51B /* TSRegisterPrekeysRequest.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; name = TSRegisterPrekeysRequest.h; path = TextSecureiOS/Networking/Requests/TSRegisterPrekeysRequest.h; sourceTree = ""; };
+ A56D31B8180FCA840093D51B /* TSRegisterPrekeysRequest.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; name = TSRegisterPrekeysRequest.m; path = TextSecureiOS/Networking/Requests/TSRegisterPrekeysRequest.m; sourceTree = ""; };
+ A580D2BB19323E4A00D6C1CC /* UIColor+TextSecure.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; name = "UIColor+TextSecure.h"; path = "TextSecureiOS/Categories/UIColor+TextSecure.h"; sourceTree = ""; };
+ A580D2BC19323E4A00D6C1CC /* UIColor+TextSecure.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; name = "UIColor+TextSecure.m"; path = "TextSecureiOS/Categories/UIColor+TextSecure.m"; sourceTree = ""; };
+ A5DE19D1170702E900ACAFDD /* AddressBookUI.framework */ = {isa = PBXFileReference; lastKnownFileType = wrapper.framework; name = AddressBookUI.framework; path = System/Library/Frameworks/AddressBookUI.framework; sourceTree = SDKROOT; };
+ A5DE19D3170702ED00ACAFDD /* AddressBook.framework */ = {isa = PBXFileReference; lastKnownFileType = wrapper.framework; name = AddressBook.framework; path = System/Library/Frameworks/AddressBook.framework; sourceTree = SDKROOT; };
+ A5E6CBFB187629D4002A1735 /* MediaPlayer.framework */ = {isa = PBXFileReference; lastKnownFileType = wrapper.framework; name = MediaPlayer.framework; path = System/Library/Frameworks/MediaPlayer.framework; sourceTree = SDKROOT; };
+ A5E6CC07187AC6D5002A1735 /* TSDownloadAttachment.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; name = TSDownloadAttachment.h; path = TextSecureiOS/Networking/Requests/TSDownloadAttachment.h; sourceTree = ""; };
+ A5E6CC08187AC6D5002A1735 /* TSDownloadAttachment.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; name = TSDownloadAttachment.m; path = TextSecureiOS/Networking/Requests/TSDownloadAttachment.m; sourceTree = ""; };
+ A5E6CC61187D0F4B002A1735 /* IncomingPushMessageSignal.pb.hh */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.cpp.h; path = IncomingPushMessageSignal.pb.hh; sourceTree = ""; };
+ A5E6CC62187D0F4B002A1735 /* IncomingPushMessageSignal.pb.mm */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.cpp.objcpp; path = IncomingPushMessageSignal.pb.mm; sourceTree = ""; };
+ A5E6CC63187D0F4B002A1735 /* IncomingPushMessageSignal.proto */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = text; path = IncomingPushMessageSignal.proto; sourceTree = ""; };
+ A5E6CC64187D0F4B002A1735 /* PreKeyWhisperMessage.pb.hh */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.cpp.h; path = PreKeyWhisperMessage.pb.hh; sourceTree = ""; };
+ A5E6CC65187D0F4B002A1735 /* PreKeyWhisperMessage.pb.mm */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.cpp.objcpp; path = PreKeyWhisperMessage.pb.mm; sourceTree = ""; };
+ A5E6CC66187D0F4B002A1735 /* PreKeyWhisperMessage.proto */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = text; path = PreKeyWhisperMessage.proto; sourceTree = ""; };
+ A5E6CC67187D0F4B002A1735 /* PushMessageContent.pb.hh */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.cpp.h; path = PushMessageContent.pb.hh; sourceTree = ""; };
+ A5E6CC68187D0F4B002A1735 /* PushMessageContent.pb.mm */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.cpp.objcpp; path = PushMessageContent.pb.mm; sourceTree = ""; };
+ A5E6CC69187D0F4B002A1735 /* PushMessageContent.proto */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = text; path = PushMessageContent.proto; sourceTree = ""; };
+ A5E6CC6A187D0F4B002A1735 /* WhisperMessage.pb.hh */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.cpp.h; path = WhisperMessage.pb.hh; sourceTree = ""; };
+ A5E6CC6B187D0F4B002A1735 /* WhisperMessage.pb.mm */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.cpp.objcpp; path = WhisperMessage.pb.mm; sourceTree = ""; };
+ A5E6CC6C187D0F4B002A1735 /* WhisperMessage.proto */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = text; path = WhisperMessage.proto; sourceTree = ""; };
+ A5E6CC75187D0FF1002A1735 /* TSEncryptedWhisperMessage.hh */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.cpp.h; name = TSEncryptedWhisperMessage.hh; path = ProtocolBufferWrappers/TSEncryptedWhisperMessage.hh; sourceTree = ""; };
+ A5E6CC76187D0FF1002A1735 /* TSEncryptedWhisperMessage.mm */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.cpp.objcpp; name = TSEncryptedWhisperMessage.mm; path = ProtocolBufferWrappers/TSEncryptedWhisperMessage.mm; sourceTree = ""; };
+ A5E6CC77187D0FF1002A1735 /* TSMessageSignal.hh */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.cpp.h; name = TSMessageSignal.hh; path = ProtocolBuffers/ProtocolBufferWrappers/TSMessageSignal.hh; sourceTree = ""; };
+ A5E6CC78187D0FF1002A1735 /* TSMessageSignal.mm */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.cpp.objcpp; name = TSMessageSignal.mm; path = ProtocolBuffers/ProtocolBufferWrappers/TSMessageSignal.mm; sourceTree = ""; };
+ A5E6CC79187D0FF1002A1735 /* TSPreKeyWhisperMessage.hh */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.cpp.h; name = TSPreKeyWhisperMessage.hh; path = ProtocolBufferWrappers/TSPreKeyWhisperMessage.hh; sourceTree = ""; };
+ A5E6CC7A187D0FF1002A1735 /* TSPreKeyWhisperMessage.mm */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.cpp.objcpp; name = TSPreKeyWhisperMessage.mm; path = ProtocolBufferWrappers/TSPreKeyWhisperMessage.mm; sourceTree = ""; };
+ A5E6CC7B187D0FF1002A1735 /* TSProtocolBufferWrapper.hh */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.cpp.h; name = TSProtocolBufferWrapper.hh; path = ProtocolBuffers/ProtocolBufferWrappers/TSProtocolBufferWrapper.hh; sourceTree = ""; };
+ A5E6CC7C187D0FF1002A1735 /* TSProtocolBufferWrapper.mm */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.cpp.objcpp; name = TSProtocolBufferWrapper.mm; path = ProtocolBuffers/ProtocolBufferWrappers/TSProtocolBufferWrapper.mm; sourceTree = ""; };
+ A5E6CC7D187D0FF1002A1735 /* TSPushMessageContent.hh */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.cpp.h; name = TSPushMessageContent.hh; path = ProtocolBuffers/ProtocolBufferWrappers/TSPushMessageContent.hh; sourceTree = ""; };
+ A5E6CC7E187D0FF1002A1735 /* TSPushMessageContent.mm */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.cpp.objcpp; name = TSPushMessageContent.mm; path = ProtocolBuffers/ProtocolBufferWrappers/TSPushMessageContent.mm; sourceTree = ""; };
+ A5E6CC81187D0FF1002A1735 /* TSWhisperMessage.hh */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.cpp.h; name = TSWhisperMessage.hh; path = ProtocolBufferWrappers/TSWhisperMessage.hh; sourceTree = ""; };
+ A5E6CC8F187D1E41002A1735 /* TSWhisperMessage.mm */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.cpp.objcpp; name = TSWhisperMessage.mm; path = ProtocolBufferWrappers/TSWhisperMessage.mm; sourceTree = ""; };
+ A5E6CC9A18826005002A1735 /* TSProtocolBufferWrapperTests.mm */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.cpp.objcpp; path = TSProtocolBufferWrapperTests.mm; sourceTree = ""; };
+ A5E6CC9C18837C31002A1735 /* TSAxolotlRatchet.hh */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.cpp.h; name = TSAxolotlRatchet.hh; path = Security/TSAxolotlRatchet.hh; sourceTree = ""; };
+ A5E6CC9D18837C31002A1735 /* TSAxolotlRatchet.mm */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.cpp.objcpp; name = TSAxolotlRatchet.mm; path = Security/TSAxolotlRatchet.mm; sourceTree = ""; };
A5F15A99170280B700856385 /* Security.framework */ = {isa = PBXFileReference; lastKnownFileType = wrapper.framework; name = Security.framework; path = System/Library/Frameworks/Security.framework; sourceTree = SDKROOT; };
- A5F15A9B1702949100856385 /* NSData+Conversion.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = "NSData+Conversion.h"; sourceTree = ""; };
- A5F15A9C1702949100856385 /* NSData+Conversion.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; path = "NSData+Conversion.m"; sourceTree = ""; };
- A5F15A9E1702997A00856385 /* KeychainWrapper.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = KeychainWrapper.h; sourceTree = ""; };
- A5F15A9F1702997A00856385 /* KeychainWrapper.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; path = KeychainWrapper.m; sourceTree = ""; };
- A5F15AA41702DF6E00856385 /* libssl.a */ = {isa = PBXFileReference; lastKnownFileType = archive.ar; name = libssl.a; path = Libraries/lib/libssl.a; sourceTree = ""; };
- A5F15AA51702DF6E00856385 /* libcrypto.a */ = {isa = PBXFileReference; lastKnownFileType = archive.ar; name = libcrypto.a; path = Libraries/lib/libcrypto.a; sourceTree = ""; };
- A5F15AAA1702DF9000856385 /* aes.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = aes.h; sourceTree = ""; };
- A5F15AAB1702DF9000856385 /* asn1.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = asn1.h; sourceTree = ""; };
- A5F15AAC1702DF9000856385 /* asn1_mac.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = asn1_mac.h; sourceTree = ""; };
- A5F15AAD1702DF9000856385 /* asn1t.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = asn1t.h; sourceTree = ""; };
- A5F15AAE1702DF9000856385 /* bio.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = bio.h; sourceTree = ""; };
- A5F15AAF1702DF9000856385 /* blowfish.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = blowfish.h; sourceTree = ""; };
- A5F15AB01702DF9000856385 /* bn.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = bn.h; sourceTree = ""; };
- A5F15AB11702DF9000856385 /* buffer.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = buffer.h; sourceTree = ""; };
- A5F15AB21702DF9000856385 /* camellia.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = camellia.h; sourceTree = ""; };
- A5F15AB31702DF9000856385 /* cast.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = cast.h; sourceTree = ""; };
- A5F15AB41702DF9000856385 /* cmac.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = cmac.h; sourceTree = ""; };
- A5F15AB51702DF9000856385 /* cms.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = cms.h; sourceTree = ""; };
- A5F15AB61702DF9000856385 /* comp.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = comp.h; sourceTree = ""; };
- A5F15AB71702DF9000856385 /* conf.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = conf.h; sourceTree = ""; };
- A5F15AB81702DF9000856385 /* conf_api.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = conf_api.h; sourceTree = ""; };
- A5F15AB91702DF9000856385 /* crypto.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = crypto.h; sourceTree = ""; };
- A5F15ABA1702DF9000856385 /* des.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = des.h; sourceTree = ""; };
- A5F15ABB1702DF9000856385 /* des_old.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = des_old.h; sourceTree = ""; };
- A5F15ABC1702DF9000856385 /* dh.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = dh.h; sourceTree = ""; };
- A5F15ABD1702DF9000856385 /* dsa.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = dsa.h; sourceTree = ""; };
- A5F15ABE1702DF9000856385 /* dso.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = dso.h; sourceTree = ""; };
- A5F15ABF1702DF9000856385 /* dtls1.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = dtls1.h; sourceTree = ""; };
- A5F15AC01702DF9000856385 /* e_os2.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = e_os2.h; sourceTree = ""; };
- A5F15AC11702DF9000856385 /* ebcdic.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = ebcdic.h; sourceTree = ""; };
- A5F15AC21702DF9000856385 /* ec.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = ec.h; sourceTree = "